
The Toronto Public Library is experiencing ongoing technical outages on account of a Black Basta ransomware assault.
The Toronto Public Library (TPL) is Canada’s largest public library system, giving entry to 12 million books by way of 100 department libraries throughout town. The library system has 1,200,000 registered members and operates on a funds that surpasses $200M.
Earlier this week, TPL warned {that a} cyberattack is inflicting technical outages on its web sites and a few on-line companies.
These outages embrace the tpl.ca web site being taken offline, the lack to entry your on-line account, and outages within the tpl:map passes and digital collections companies.
The library warned that public computer systems and printing companies are additionally unavailable.
The Toronto Public Library says that there isn’t any proof that the private data of employees or clients has been compromised and that they’re actively investigating the incident with regulation enforcement and third-party cybersecurity consultants.
“TPL has proactively ready for cybersecurity points and promptly initiated measures to mitigate potential impacts,” reads a discover on a short-term library web site hosted on Typepad.
“We’ve engaged with third-party cybersecurity consultants to assist us in resolving this example. We do anticipate although that it could take a number of days earlier than all techniques are absolutely restored to regular operations.”
Do you may have details about this or one other ransomware assault? If you wish to share the data, you may contact us securely and confidentially on Sign at +1 (646) 961-3731, by way of electronic mail at lawrence.abrams@bleepingcomputer.com, or through the use of our suggestions kind.
Black Basta ransomware behind assault on TPL
BleepingComputer has since realized that the Black Basta ransomware operation is behind the assault on the Toronto Public Library.
A photograph of the ransom word shared with BleepingComputer allowed us to verify that the ransomware operation was behind the assault.
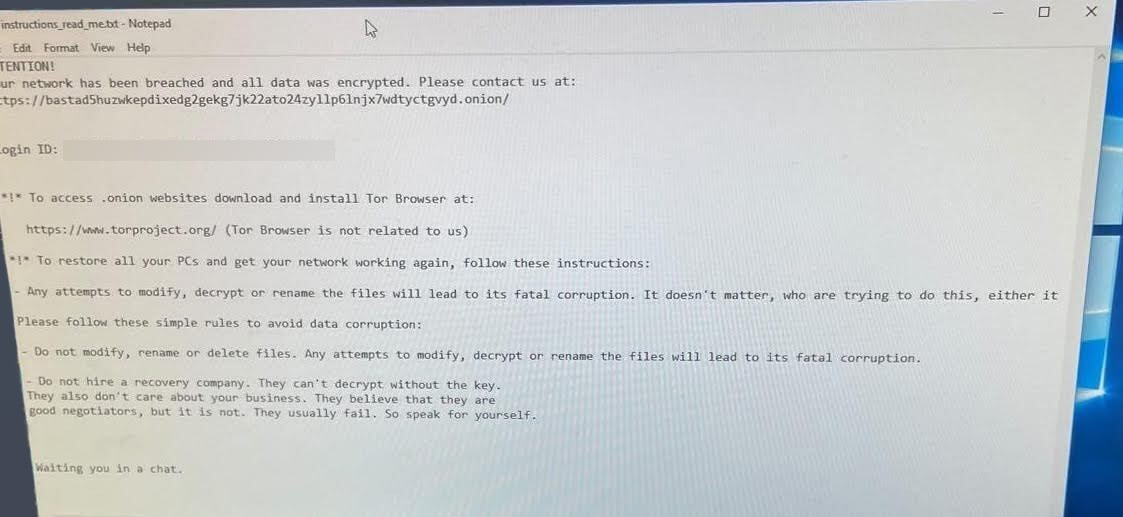
Supply: BleepingComputer
In response to a TPL worker, the assault occurred in a single day on October twenty seventh, impacting quite a few companies Saturday morning.
BleepingComputer was advised that the assault didn’t influence telephones and had restricted influence on electronic mail, with these logged into their Workplace 365 accounts nonetheless in a position to entry them. Nonetheless, staff who weren’t presently logged into electronic mail have been now not in a position to entry the system.
All different inside techniques have been shut down after the assault as a precaution to stop the unfold of the malware.
We have been advised the group’s principal servers containing delicate information weren’t encrypted, doubtlessly that means that the risk actors didn’t have full entry to the group’s networks and information.
Whereas it’s unknown now if the ransomware gang stole information throughout the assault, information theft is a significant factor of their extortion technique.
We’ll study if information was stolen if the risk actors will use it as leverage to strain TPL into paying a ransom.
Who’s Black Basta?
The Black Basta ransomware gang launched its ransomware operation in April 2022 and rapidly started concentrating on company victims in double-extortion assaults.
One among its first assaults was towards the American Dental Affiliation, throughout which the risk actors leaked stolen information.
By June 2022, Black Basta had partnered with the QBot malware operation to drop Cobalt Strike beacons on contaminated units for preliminary entry to company networks.
As soon as they gained entry to a community, they’d steal credentials and unfold laterally all through a community whereas stealing information.
In any case information is stolen and the hackers achieve entry to the Home windows area controller, the risk actors deploy an encryptor all through the community to encrypt units.
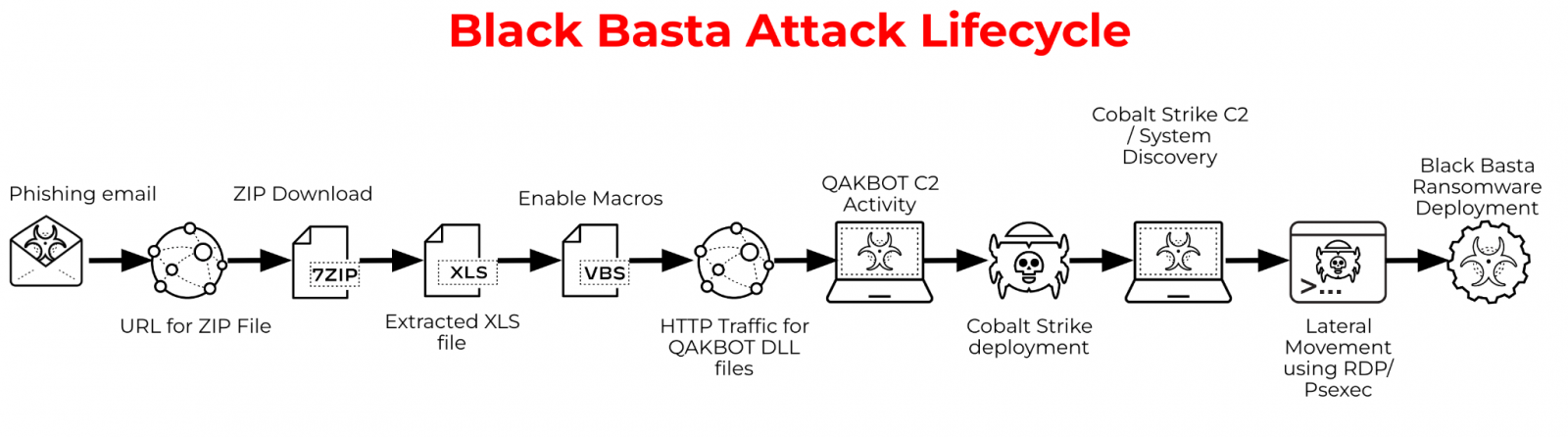
Supply: Palo Alto Networks Unit 42
Like nearly all ransomware operations, Black Basta makes use of a Linux encryptor to focus on VMware ESXi digital machines working on Linux servers.
In June 2022, the Conti ransomware operation shut down after struggling a sequence of embarrassing information breaches. Researchers consider that the cybercrime syndicate splintered into smaller teams, with one in every of them believed to be Black Basta.
Nonetheless, different researchers consider there’s a hyperlink between Black Basta and the Fin7 cybercrime operation, a financially motivated cybercrime gang also called Carbanak.
Since its launch, the risk actors have been answerable for a stream of assaults, together with Capita, Sobeys, Knauf, and Yellow Pages Canada.
Lately, the ransomware operation attacked ABB, a Swiss tech multinational and U.S. authorities contractor, and leaked the corporate’s stolen information.
