Picture: Midjourney
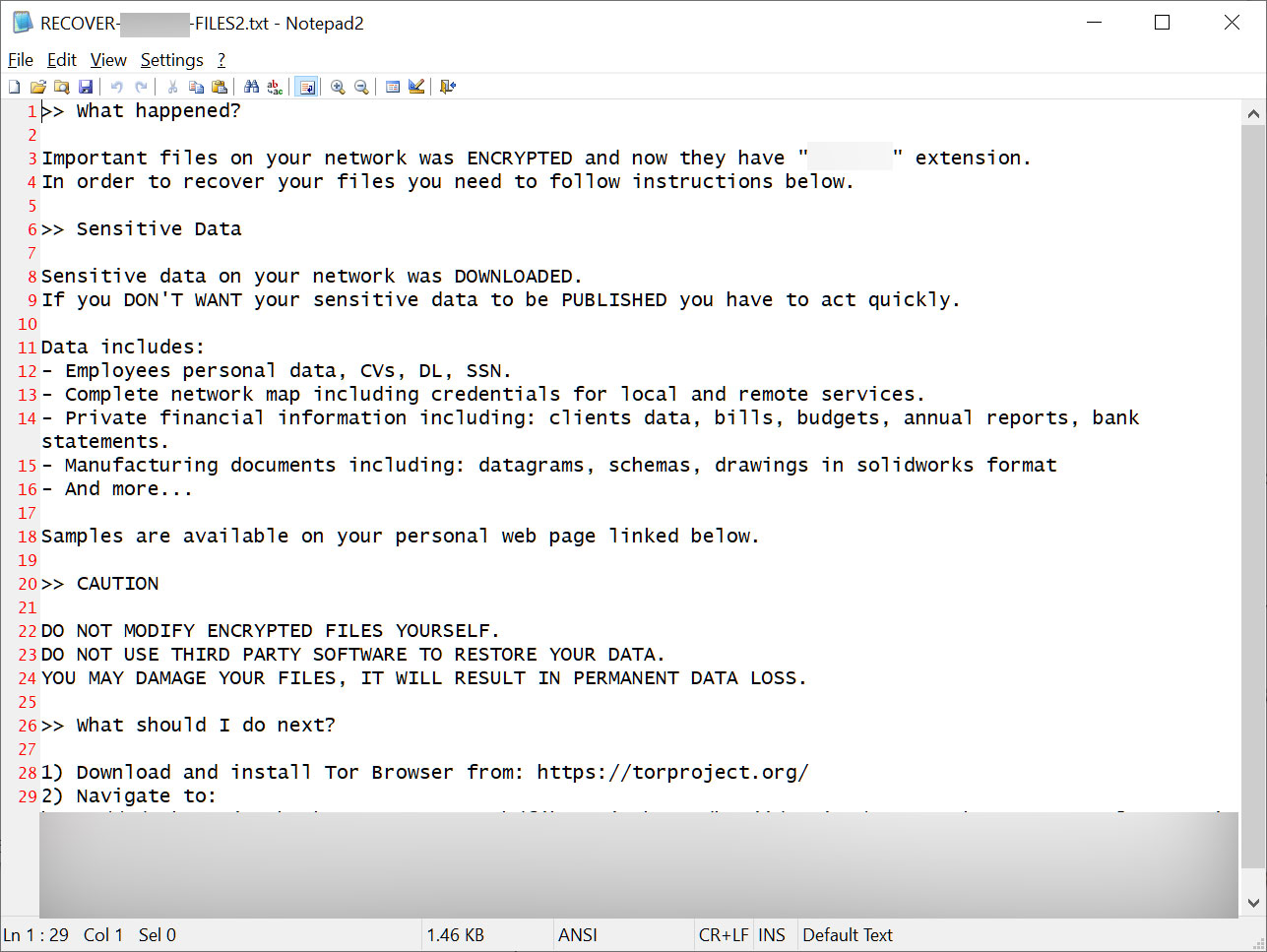
The BlackCat (ALPHV) ransomware gang now makes use of stolen Microsoft accounts and the lately noticed Sphynx encryptor to encrypt targets’ Azure cloud storage.
Whereas investigating a latest breach, Sophos X-Ops incident responders found that the attackers used a brand new Sphynx variant with added assist for utilizing customized credentials.
After getting access to the Sophos Central account utilizing a stolen One-Time Password (OTP), they disabled Tamper Safety and modified the safety insurance policies. These actions have been doable after stealing the OTP from the sufferer’s LastPass vault utilizing the LastPass Chrome extension.
Subsequently, they encrypted the Sophos buyer’s programs and distant Azure cloud storage and appended the .zk09cvt extension to all locked information. In whole, the ransomware operators might encrypt 39 Azure Storage accounts efficiently.
They infiltrated the sufferer’s Azure portal utilizing a stolen Azure key that offered them entry to the focused storage accounts. The keys used within the assault have been injected throughout the ransomware binary after being encoded utilizing Base64.
The attackers additionally used a number of Distant Monitoring and Administration (RMM) instruments like AnyDesk, Splashtop, and Atera all through the intrusion.
Sophos found the Sphynx variant in March 2023 throughout an investigation into a knowledge breach that shared similarities with one other assault described in an IBM-Xforce report printed in Could (the ExMatter software was used to extract the stolen information in each cases).
Microsoft additionally discovered final month that the brand new Sphynx encryptor is embedding the Remcom hacking software and the Impacket networking framework for lateral motion throughout compromised networks.
As a ransomware operation that emerged in November 2021, BlackCat/ALPHV is suspected to be a DarkSide/BlackMatter rebrand.
Identified initially as DarkSide, this group garnered international consideration after breaching Colonial Pipeline, drawing quick scrutiny from worldwide legislation enforcement businesses.
Though they rebranded as BlackMatter in July 2021, operations have been abruptly halted in November when authorities seized their servers and safety agency Emsisoft developed a decryption software exploiting a vulnerability within the ransomware.
This gang has persistently been acknowledged as some of the refined and high-profile ransomware outfits that targets enterprises on a world scale, repeatedly adapting and refining its techniques.
For example, in a new extortion strategy final summer time, the ransomware gang used a devoted clear internet web site to leak the stolen information of a particular sufferer, offering the sufferer’s prospects and workers with the means to find out whether or not their information had been uncovered.
Extra lately, BlackCat launched a knowledge leak API in July designed to streamline the dissemination of stolen information.
This week, one of many gang’s associates gang (tracked as Scattered Spider) claimed the assault on MGM Resorts, saying they encrypted over 100 ESXi hypervisors after the corporate took down its inner infrastructure and refused to barter a ransom fee.
Final April, the FBI issued a warning highlighting that the group was behind the profitable breaches of greater than 60 entities worldwide between November 2021 and March 2022.

