Researchers at Eurecom have developed six new assaults collectively named ‘BLUFFS’ that may break the secrecy of Bluetooth periods, permitting for gadget impersonation and man-in-the-middle (MitM) assaults.
Daniele Antonioli, who found the assaults, explains that BLUFFS exploits two beforehand unknown flaws within the Bluetooth normal associated to how session keys are derived to decrypt knowledge in alternate.
These flaws aren’t particular to {hardware} or software program configurations however are architectural as an alternative, that means they have an effect on Bluetooth at a elementary degree.
The problems are tracked beneath the identifier CVE-2023-24023 and influence Bluetooth Core Specification 4.2 by way of 5.4.
Contemplating the widespread use of the well-established wi-fi communication normal and the variations impacted by the exploits, BLUFFS might work in opposition to billions of gadgets, together with laptops, smartphones, and different cell gadgets.
How BLUFFS works
BLUFFS is a sequence of exploits focusing on Bluetooth, aiming to interrupt Bluetooth periods’ ahead and future secrecy, compromising the confidentiality of previous and future communications between gadgets.
That is achieved by exploiting 4 flaws within the session key derivation course of, two of that are new, to drive the derivation of a brief, thus weak and predictable session key (SKC).
Subsequent, the attacker brute-forces the important thing, enabling them to decrypt previous communication and decrypt or manipulate future communications.
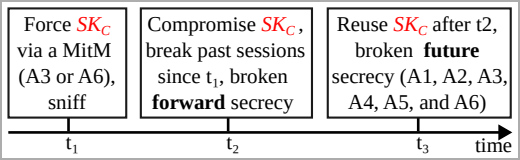
Executing the assault presupposes that the attacker is inside Bluetooth vary of the 2 targets that alternate knowledge and impersonates one to barter for a weak session key with the opposite, proposing the bottom potential key entropy worth and utilizing a relentless session key diversifier.
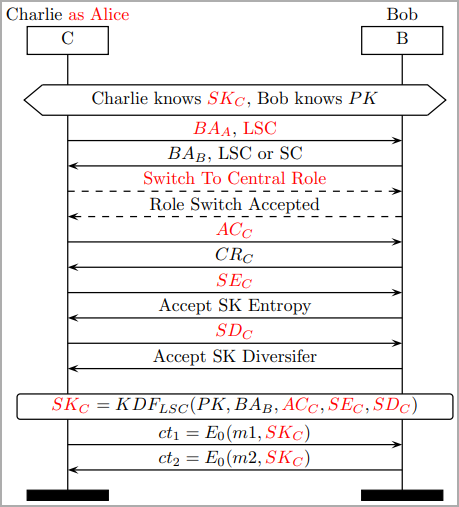
(dl.acm.org)
The revealed paper presents six sorts of BLUFFS assaults, overlaying varied mixtures of impersonating and MitM assaults, which work no matter whether or not the victims assist Safe Connections (SC) or Legacy Safe Connections (LSC).
The researchers developed and shared a toolkit on GitHub that demonstrates the effectiveness of BLUFFS. It features a Python script to check the assaults, the ARM patches, the parser, and the PCAP samples captured throughout their assessments.
Impression and remediation
BLUFFS impacts Bluetooth 4.2, launched in December 2014, and all variations as much as the newest, Bluetooth 5.4, launched in February 2023.
The Eurecom paper presents check outcomes for BLUFFS in opposition to varied gadgets, together with smartphones, earphones, and laptops, operating Bluetooth variations 4.1 by way of 5.2. All of them had been confirmed to be prone to at the least three out of six BLUFFS assaults.
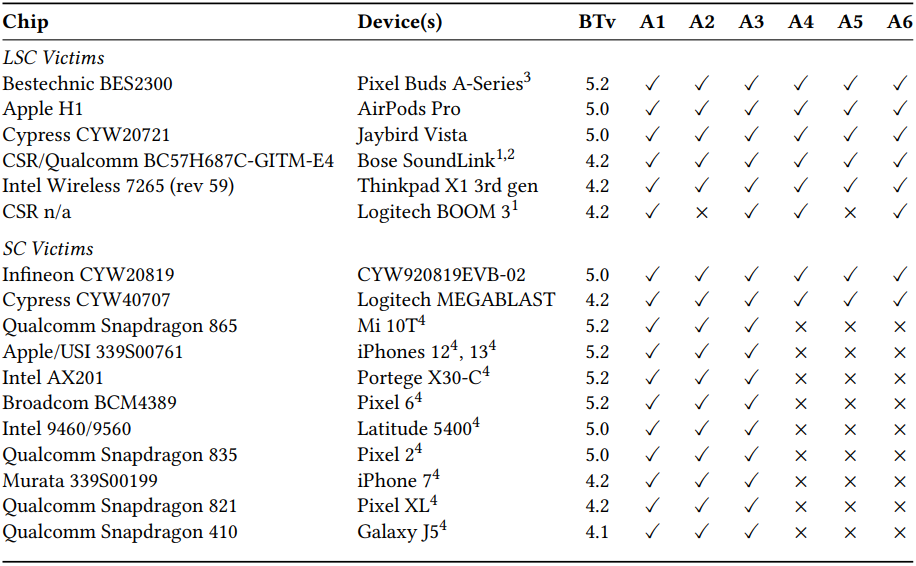
The paper additionally proposes the next backward-compatible modifications that may improve session key derivation and mitigate BLUFFS and related threats:
- Introduce a brand new “Key Derivation Perform” (KDF) for Legacy Safe Connections (LSC) that entails mutual nonce alternate and verification, including minimal overhead.
- Gadgets ought to use a shared pairing key for the mutual authentication of key diversifiers, making certain the legitimacy of session members.
- Implement Safe Connections (SC) mode the place potential.
- Keep a cache of session key diversifiers to forestall reuse.
Bluetooth SIG (Particular Curiosity Group), the non-profit group that oversees the event of the Bluetooth normal and is answerable for licensing the expertise, has obtained Eurecom’s report and revealed an announcement on its website.
The group means that implementations reject connections with low key strengths beneath seven octets, use ‘Safety Mode 4 Degree 4’, which ensures the next encryption energy degree, and function in ‘Safe Connections Solely’ mode when pairing.

