
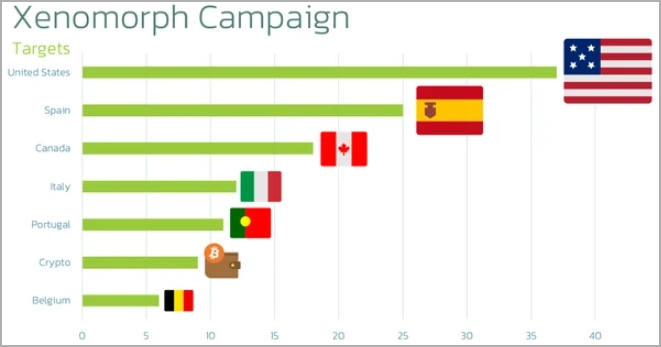
Safety researchers found a brand new marketing campaign that distributes a brand new model of the Xenomorph malware to Android customers in the USA, Canada, Spain, Italy, Portugal, and Belgium.
Analysts at cybersecurity firm ThreatFabric have been monitoring Xenomorph exercise since February 2022 and notice that the brand new marketing campaign launched in mid-August.
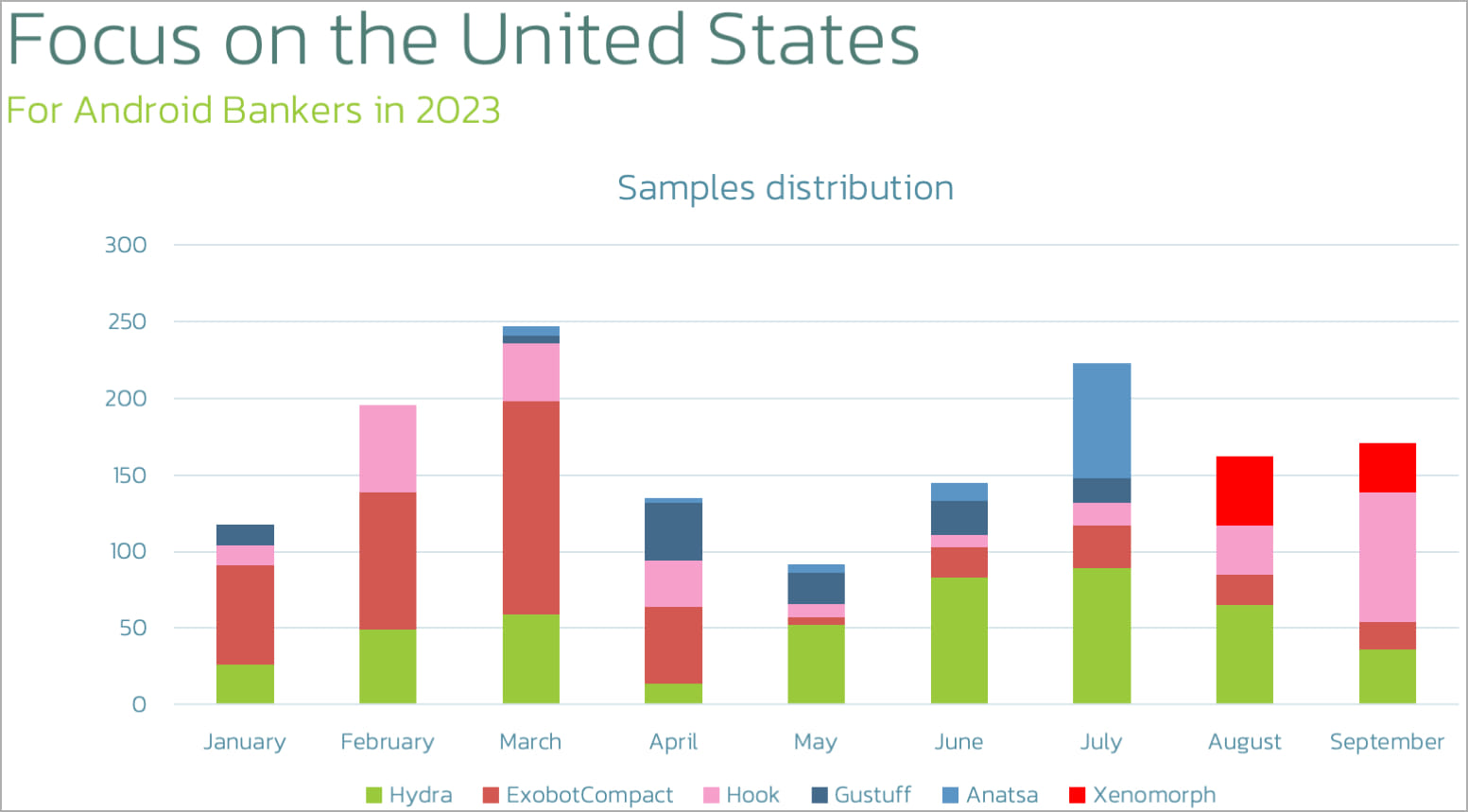
The newest model of Xenomorph is concentrating on customers of cryptocurrency wallets and varied U.S. monetary establishments.
Xenomorph background
Xenomorph first appeared within the wild in early 2022, working as a banking trojan that focused 56 European banks by way of display screen overlay phishing. It was distributed by way of Google Play, the place it counted over 50,000 installations.
Its authors, “Hadoken Safety,” continued growth, and in June 2022, they launched a rewritten model that made the malware modular and extra versatile.
By then, Xenomorph was on Zimperium’s prime ten most prolific banking trojans, so it had already achived the “main risk” standing.
In August 2022, ThreatFabric reported that Xenomorph was being distributed by way of a brand new dropper named “BugDrop,” which bypassed safety features in Android 13.
In December 2022, the identical analysts reported a few new malware distribution platform dubbed “Zombinder,” which embedded the risk into respectable Android apps’ APK file.
Most just lately, in March 2023, Hadoken launched the third main model of Xenomorph, that includes an automatic switch system (ATS) for autonomous on-device transactions, MFA bypass, cookie stealing, and the power to focus on over 400 banks.
New marketing campaign
Within the newest marketing campaign, the malware operators opted to make use of phishing pages, luring guests to replace their Chrome browser and trick them into downloading the malicious APK.

The malware continues to make use of overlays to steal data. Nonetheless, it has now expanded its concentrating on scope to incorporate monetary establishments from the USA and a number of cryptocurrency apps.
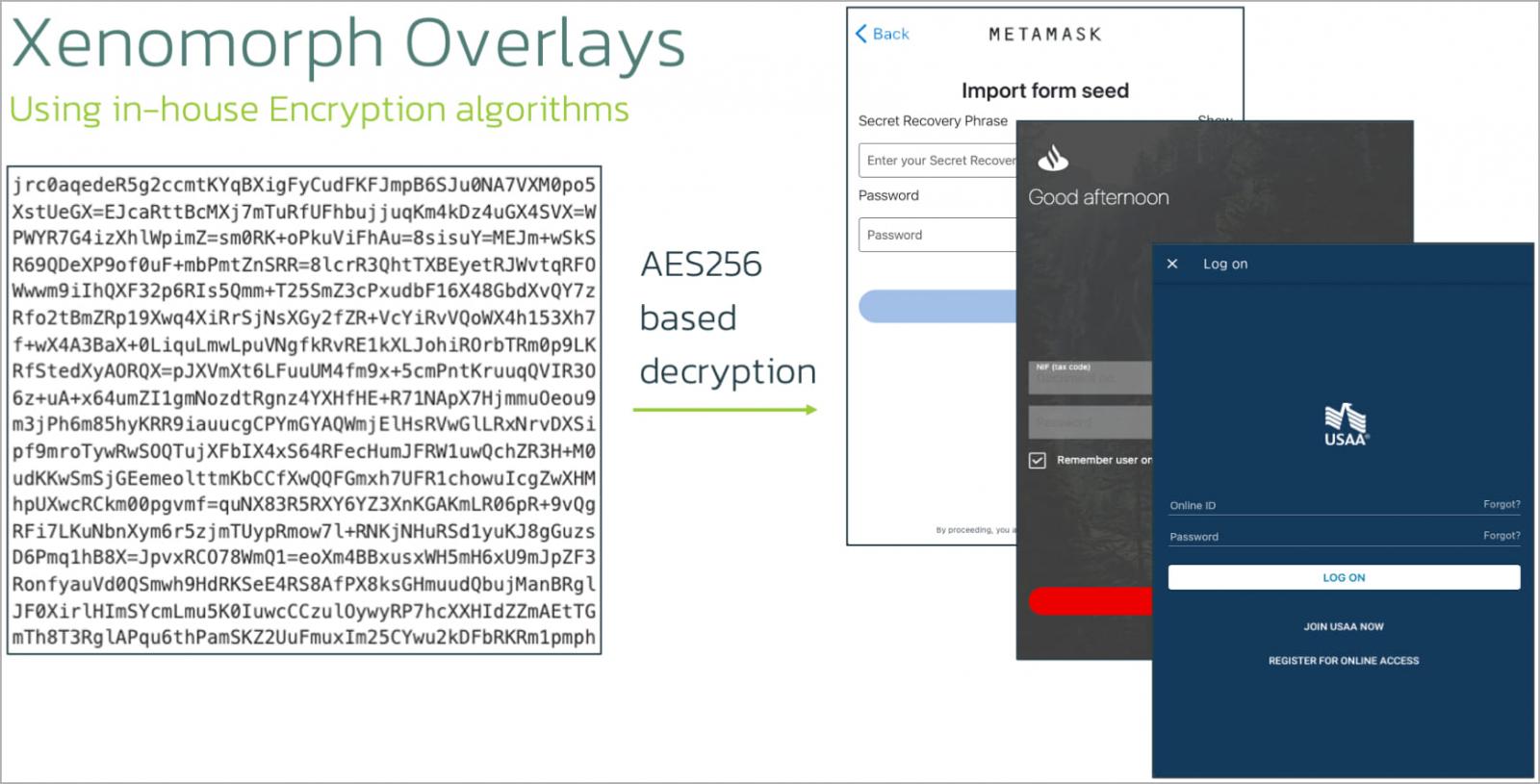
ThreatFabric explains that every Xenomorph pattern is loaded with roughly 100 overlays concentrating on completely different units of banks and crypto apps, relying on the focused demographic.
Newest model
Though the brand new Xenomorph samples aren’t vastly completely different from earlier variants, they arrive with some new options indicating that its authors proceed to refine and improve the malware.
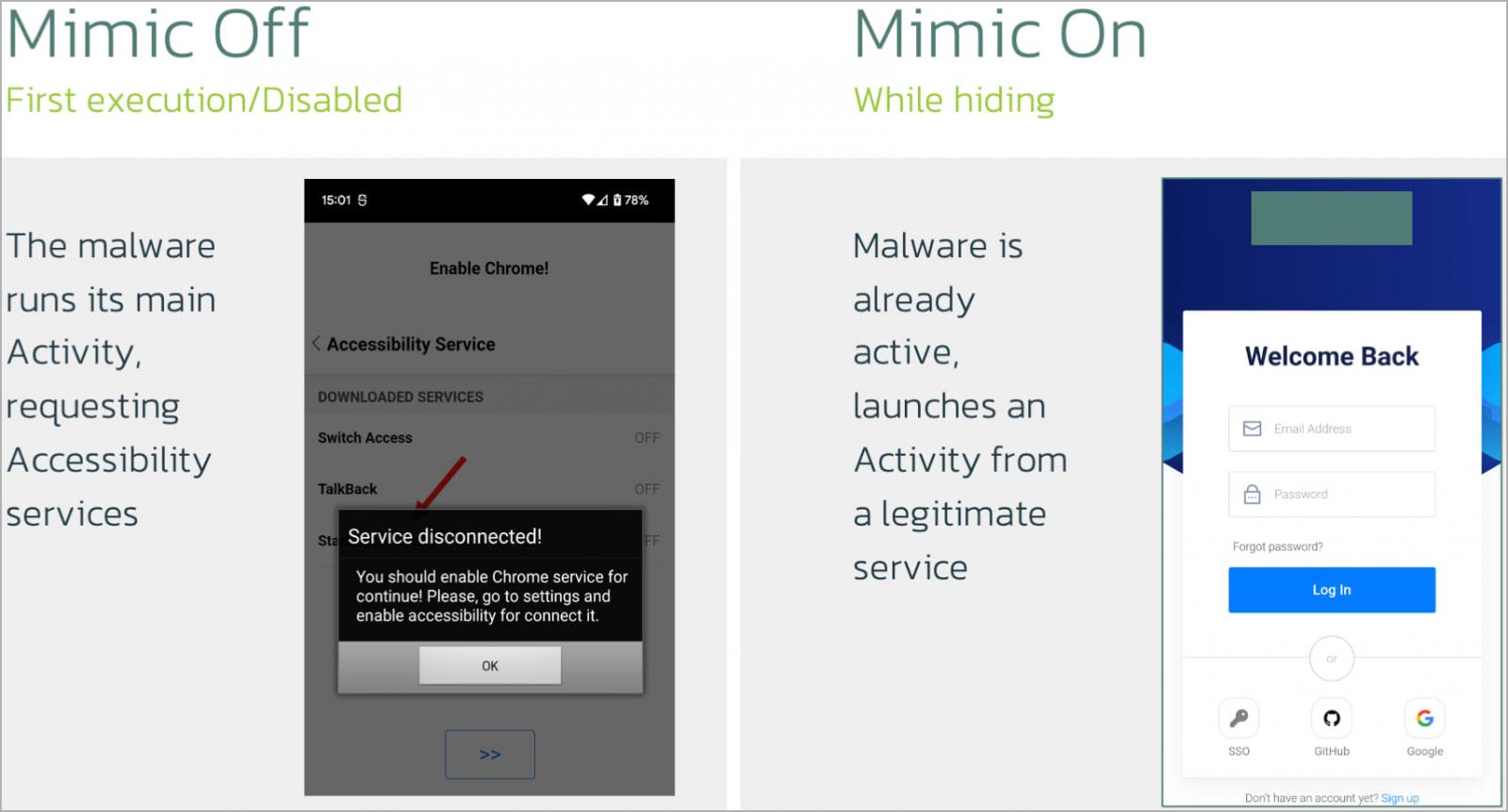
First, a brand new “mimic” function will be activated by a corresponding command, giving the malware the potential to behave as one other utility.
Moreover, mimic has a built-in exercise named IDLEActivity, which acts as a WebView to show respectable internet content material from the context of a trusty course of.
This technique replaces the necessity to cover icons from the app launcher post-installation, which is flagged as suspicious habits by most cellular safety instruments.
One other new function is “ClickOnPoint,”, which permits Xenomorph operators to simulate faucets at particular display screen coordinates.
This enables the operators to maneuver previous affirmation screens or carry out different easy actions with out using the total ATS module, which could set off safety warnings.
Lastly, there is a new “antisleep” system that stops the gadget from switching off its display screen by way of an energetic notification.
That is helpful for prolonging the engagement and avoiding interruptions that require re-establishing command and management communications.
Different findings
By profiting from weak safety measures from the malware operator, ThreatFabric analysts might entry their payload internet hosting infrastructure.
There, they found further malicious payloads, together with the Android malware variants Medusa and Cabassous, the Home windows data stealers RisePro and LummaC2, and the Personal Loader malware loader.
Customers ought to be cautious with prompts on cellular to replace their browsers, as these are seemingly a part of malware distribution campaigns.
Xenomorph’s distribution alongside potent Home windows malware suggests collaboration between risk actors or the potential for the Android trojan being bought as Malware-as-a-Service (MaaS).
