Cybersecurity researchers have found an up to date model of an Android banking malware referred to as Chameleon that has expanded its concentrating on to incorporate customers within the U.Okay. and Italy.
“Representing a restructured and enhanced iteration of its predecessor, this developed Chameleon variant excels in executing Gadget Takeover (DTO) utilizing the accessibility service, all whereas increasing its focused area,” Dutch cellular safety agency ThreatFabric mentioned in a report shared with The Hacker Information.
Chameleon was beforehand documented by Cyble in April 2023, noting that it had been used to single out customers in Australia and Poland since a minimum of January. Like different banking malware, it is recognized to abuse its permissions to Android’s accessibility service to reap delicate knowledge and conduct overlay assaults.
The rogue apps containing the sooner model had been hosted on phishing pages and located to impersonate real establishments within the international locations, such because the Australian Taxation Workplace (ATO) and a cryptocurrency buying and selling platform referred to as CoinSpot, in an try and lend them a veil of credibility.
The newest findings from ThreatFabric present that the banking trojan is now being delivered by way of Zombinder, an off-the-shelf dropper-as-a-service (DaaS) that is bought to different menace actors and which can be utilized to “bind” malicious payloads to reputable apps.
Beat AI-Powered Threats with Zero Belief – Webinar for Safety Professionals
Conventional safety measures will not reduce it in at this time’s world. It is time for Zero Belief Safety. Safe your knowledge like by no means earlier than.
Though the providing was suspected to have been shut down earlier this 12 months, it resurfaced final month, promoting capabilities to bypass the ‘Restricted Settings’ function in Android to put in malware on units and procure entry to the accessibility service.
Each the malicious artifacts distributing Chameleon masquerade because the Google Chrome net browser. Their bundle names are listed under –
- Z72645c414ce232f45.Z35aad4dde2ff09b48
- com.busy.girl
A notable function of the improved variant is its skill to conduct Gadget Takeover (DTO) fraud, which leverages the accessibility service to carry out unauthorized actions on the sufferer’s behalf.
However to be able to trick customers into enabling the setting, the malware checks the Android model on the put in system and if it is discovered to be Android 13 or later, prompts the consumer to show it on.
“Upon receiving affirmation of Android 13 Restricted Settings being current on the contaminated system, the banking trojan initiates the loading of an HTML web page,” ThreatFabric defined. “The web page is guiding customers by way of a guide step-by-step course of to allow the accessibility service on Android 13 and better.”
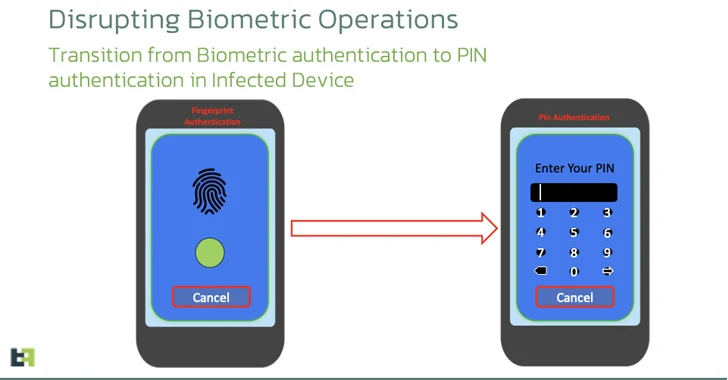
One other new addition is using Android APIs to disrupt the biometric operations of the focused system by covertly transitioning the lock display screen authentication mechanism to a PIN in order to permit the malware to “unlock the system at will” utilizing the accessibility service.
“The emergence of the brand new Chameleon banking trojan is one other instance of the delicate and adaptive menace panorama throughout the Android ecosystem,” the corporate mentioned. “Evolving from its earlier iteration, this variant demonstrates elevated resilience and superior new options.”
The event comes as Zimperium revealed that 29 malware households – 10 of them new – focused 1,800 banking functions throughout 61 international locations over the previous 12 months. The brand new energetic households embrace Nexus, Godfather, PixPirate, Saderat, Hook, PixBankBot, Xenomorph v3, Vultur, BrasDex, and GoatRAT.
The U.S. prime international locations focused comprise the U.S. (109 financial institution apps), the U.Okay. (48), Italy (44), Australia (34), Turkey (32), France (30), Spain (29), Portugal (27), Germany (23), Canada (17), and Brazil (11). Probably the most focused monetary companies apps are PhonePe (India), WeChat, Financial institution of America, Nicely Fargo, (U.S.), Binance (Malta), Barclays (U.Okay.), QNB Finansbank (Turkey), and CaixaBank (Spain).
“Conventional banking functions stay the prime goal, with a staggering 1103 apps – accounting for 61% of the targets – whereas the rising FinTech and Buying and selling apps at the moment are within the crosshairs, making up the remaining 39%,” the corporate mentioned.