
Google has fastened the sixth Chrome zero-day vulnerability this 12 months in an emergency safety replace launched right now to counter ongoing exploitation in assaults.
The corporate acknowledged the existence of an exploit for the safety flaw (tracked as CVE-2023-6345) in a brand new safety advisory printed right now.
“Google is conscious that an exploit for CVE-2023-6345 exists within the wild,” the corporate stated.
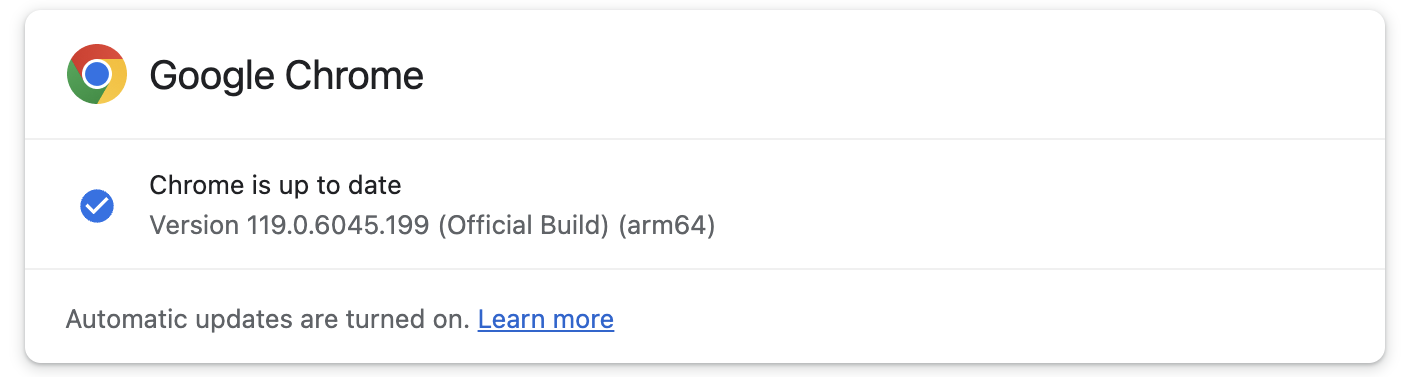
The vulnerability is now addressed within the Secure Desktop channel, with patched variations rolling out globally to Home windows customers (119.0.6045.199/.200) and Mac and Linux customers (119.0.6045.199).
Though the advisory says the safety replace could take days or perhaps weeks to achieve the complete consumer base, it was out there instantly when BleepingComputer checked for updates earlier right now.
The net browser will examine for brand new updates routinely and set up them after the following launch for customers who do not wish to do it manually.
Doubtless exploited in spy ware assaults
This high-severity zero-day vulnerability stems from an integer overflow weak point inside the Skia open-source 2D graphics library, posing dangers starting from crashes to the execution of arbitrary code (Skia can be used as a graphics engine by different merchandise like ChromeOS, Android, and Flutter).
The bug was reported on Friday, November 24, by Benoît Sevens and Clément Lecigne, two safety researchers with Google’s Risk Evaluation Group (TAG).
Google TAG is thought for uncovering zero-days, usually exploited by state-sponsored hacking teams in spy ware campaigns concentrating on high-profile people like journalists and opposition politicians.
The corporate says that entry to the zero-day’s particulars would possibly stay restricted till most customers have up to date their browser, with the limitation to be prolonged if the flaw additionally impacts utilized by third-party software program that hasn’t but been patched.
“Entry to bug particulars and hyperlinks could also be stored restricted till a majority of customers are up to date with a repair. We may even retain restrictions if the bug exists in a 3rd social gathering library that different tasks equally depend upon, however have not but fastened,” the corporate stated.
This goals to scale back the probability of risk actors creating their very own CVE-2023-6345 exploits, benefiting from newly launched technical info on the vulnerability.
In September, Google fastened two different zero-days (tracked as CVE-2023-5217 and CVE-2023-4863) exploited in assaults, the fourth and fifth ones for the reason that begin of 2023.
Replace: Revised story and title to accurately tag the zero-day because the sixth one patched this 12 months.
