
Google’s Risk Evaluation Group (TAG) has found that risk actors exploited a zero-day vulnerability in Zimbra Collaboration electronic mail server to steal delicate knowledge from authorities methods in a number of international locations.
Hackers leveraged a medium-severity safety difficulty now recognized as CVE-2023-37580 since June 29, practically a month earlier than the seller addressed it in model 8.8.15 Patch 41of the software program on July 25.
The flaw is an XSS (cross-site scripting) difficulty current within the Zimbra Traditional Net Shopper.
Assault and response timeline
In line with Google’s risk analysts, the risk actors exploited the vulnerability on authorities methods in Greece, Moldova, Tunisia, Vietnam, and Pakistan to steal electronic mail knowledge, consumer credentials, and authentication tokens, carry out electronic mail forwarding, and lead victims to phishing pages.
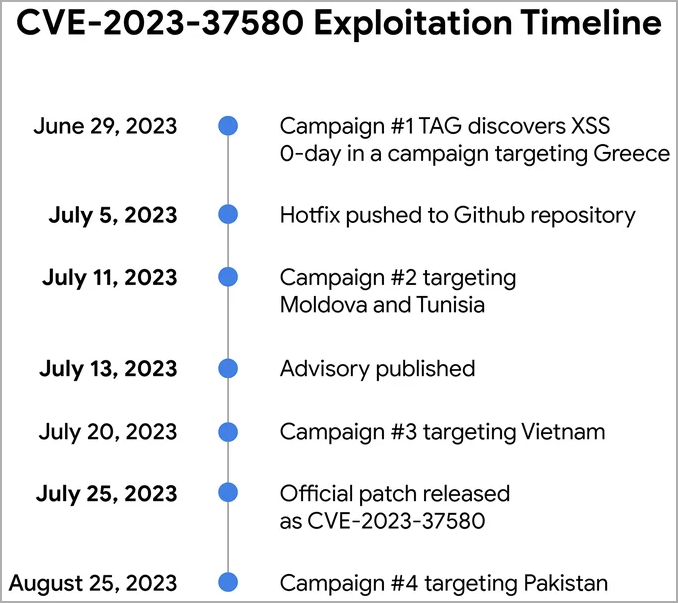
Google noticed 4 distinct risk actors utilizing the vulnerability that was unknown on the time of exploitation in late June 2023 in opposition to a authorities group in Greece.
The attackers despatched emails with a malicious URL that allowed electronic mail knowledge exfiltration and enabled auto-forwarding to an attacker-controlled deal with.
Zimbra pushed an emergency hotfix on GitHub after Google analysts alerted the corporate of the noticed compromises.
The second marketing campaign was performed on July 11 by a risk actor tracked as “Winter Vivern,” who focused authorities organizations in Moldova and Tunisia. The exploit URLs on this case loaded malicious JavaScript on the goal methods.
On July 13, Zimbra printed a safety advisory recommending mitigations for the vulnerability however there was no be aware about hackers actively exploiting the bug.
A 3rd marketing campaign started on July 20 from an unidentified risk group focusing on a Vietnamese authorities group. These assaults used an exploit URL to direct victims to a phishing web page.
5 days later Zimbra lastly launched an official patch for CVE-2023-37580, but nonetheless omitting details about the energetic exploitation.
Google notes that the three risk actors exploited the vulnerability earlier than the discharge of the official repair.
In a fourth marketing campaign on August 25, a risk actor that doubtless discovered the bug after the seller addressed it, the bug was leveraged on the methods of a Pakistani authorities group to steal Zimbra authentication tokens.
Google’s report doesn’t disclose many particulars about the attackers however nonetheless serves as a reminder concerning the significance of well timed safety updates, even when these concern medium-severity vulnerabilities as a result of adversaries already on the system could use them to additional their assault.
The exploitation of CVE-2023-37580 is without doubt one of the a number of examples of XXS flaws leveraged to assault mail servers, like CVE-2022-24682 and CVE-2023-5631, which influence Zimbra and Roundcube.
