A pattern of the Qilin ransomware gang’s VMware ESXi encryptor has been discovered and it may very well be one of the vital superior and customizable Linux encryptors seen up to now.
The enterprise is more and more shifting to digital machines to host their servers, as they permit for higher utilization of accessible CPU, reminiscence, and storage sources.
Resulting from this adoption, virtually all ransomware gangs have created devoted VMware ESXi encryptors to focus on these servers.
Whereas many ransomware operations make the most of the leaked Babuk supply code to create their encryptors, a couple of, reminiscent of Qilin, create their very own encryptors to focus on Linux servers.
Qilin targets VMware ESXi
Final month, safety researcher MalwareHunterTeam discovered a Linux ELF64 encryptor for the Qilin ransomware gang and shared it with BleepingComputer to research.
Whereas the encryptor can be utilized on Linux, FreeBSD, and VMware ESXi servers, it closely focuses on encrypting digital machines and deleting their snapshots.
Qilin’s encryptor is constructed with an embedded configuration specifying the extension for encrypted information, the processes to terminate, the information to encrypt or exclude, and the folders to encrypt or exclude.
Nonetheless, it additionally consists of quite a few command-line arguments permitting intensive customization of those configuration choices and the way information are encrypted on a server.
These command line arguments embody choices to allow a debug mode, carry out a dry run with out encrypting any information, or customise how digital machines and their snapshots are encrypted.
Supply: BleepingComputer
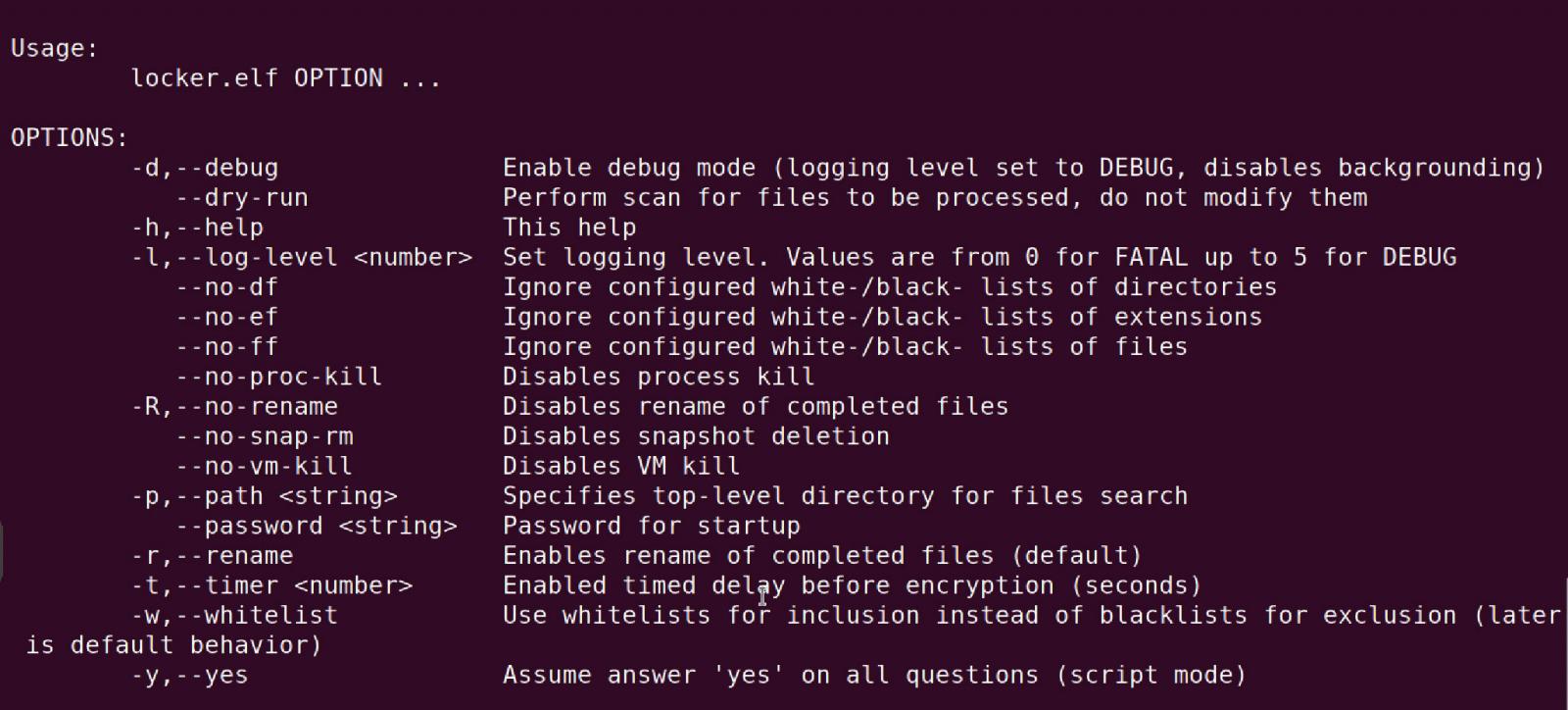
The total listing of command line choices are listed under:
OPTIONS:
-d,--debug Allow debug mode (logging stage set to DEBUG, disables backgrounding)
--dry-run Carry out scan for information to be processed, don't modify them
-h,--help This assist
-l,--log-level <quantity> Set logging stage. Values are from 0 for FATAL as much as 5 for DEBUG
--no-df Ignore configured white-/black- lists of directories
--no-ef Ignore configured white-/black- lists of extensions
--no-ff Ignore configured white-/black- lists of information
--no-proc-kill Disables course of kill
-R,--no-rename Disables rename of accomplished information
--no-snap-rm Disables snapshot deletion
--no-vm-kill Disables VM kill
-p,--path <string> Specifies top-level listing for information search
--password <string> Password for startup
-r,--rename Permits rename of accomplished information (default)
-t,--timer <quantity> Enabled timed delay earlier than encryption (seconds)
-w,--whitelist Use whitelists for inclusion as an alternative of blacklists for exclusion (later is default conduct)
-y,--yes Assume reply 'sure' on all questions (script mode)Within the pattern analyzed by BleepingComputer.com, the encryptor is configured by default with the next exclusions and focusing on standards:
Processes to not terminate:
"kvm", "qemu", "xen"Directories to exclude from encryption:
"/boot/", "/proc/", "/sys/", "/run/", "/dev/", "/lib/", "/and so forth/", "/bin/", "/mbr/", "/lib64/", "/vmware/lifecycle/", "/vdtc/", "/healthd/"Recordsdata to exclude from encryption:
"initrd", "vmlinuz", "basemisc.tgz", "boot.cfg", "bootpart.gz", "options.gz", "imgdb.tgz", "jumpstrt.gz", "onetime.tgz", "state.tgz", "useropts.gz"File extensions to exclude from encryption:
"v00", "v01", "v02", "v03", "v04", "v05", "v06", "v07", "v08", "v09", "b00", "b01", "b02", "b03", "b04", "b05", "b06", "b07", "b08", "b09", "t00", "t01", "t02", "t03", "t04", "t05", "t06", "t07", "t08", "t09"Directories to focus on for encryption:
"/dwelling", "/usr/dwelling", "/tmp", "/var/www", "/usr/native/www", "/mnt", "/media", "/srv", "/knowledge", "/backup", "/var/lib/mysql", "/var/mail", "/var/spool/mail", "/var/vm", "/var/lib/vmware", "/decide/virtualbox", "/var/lib/xen", "/var/decide/xen", "/kvm", "/var/lib/docker", "/var/lib/libvirt", "/var/run/sr-mount", "/var/lib/postgresql", "/var/lib/redis", "/var/lib/mongodb", "/var/lib/couchdb", "/var/lib/neo4j", "/var/lib/cassandra", "/var/lib/riak", "/var/lib/influxdb", "/var/lib/elasticsearch"Recordsdata to focus on for encryption:
"3ds", "3g2", "3gp", "7z", "aac", "abw", "ac3", "accdb", "ai", "aif", "aiff", "amr", "apk", "app", "asf", "asx", "atom", "avi", "bak", "bat", "bmp", "bup", "bz2", "cab", "cbr", "cbz", "cda", "cdr", "chm", "class", "cmd", "conf", "cow", "cpp", "cr2", "crdownload", "cs", "csv", "cue", "cur", "dat", "db", "dbf", "dds", "deb", "der", "desktop", "dmg", "dng", "doc", "docm", "dot", "dotm", "dotx", "dpx", "drv", "dtd", "dvi", "dwg", "dxf", "eml", "eps", "epub", "f4v", "fnt", "fon", "gam", "ged", "gif", "gpx", "gz", "h264", "hdr", "hpp", "hqx", "htm", "html", "ibooks", "ico", "ics", "iff", "picture", "img", "indd", "iso", "jar", "java", "jfif", "jpe", "jpeg", "jpf", "jpg", "js", "json", "jsp", "key", "kml", "kmz", "log", "m4a", "m4b", "m4p", "m4v", "mcd", "mdbx", "mht", "mid", "mkv", "ml", "mobi", "mov", "mp3", "mp4", "mpa", "mpeg", "mpg", "msg", "nes", "numbers", "odp", "ods", "odt", "ogg", "ogv", "otf", "ova", "ovf", "pages", "parallels", "pcast", "pct", "pdb", "pdf", "pds", "pef", "php", "pkg", "pl", "plist", "png", "pptm", "prproj", "ps", "psd", "ptx", "py", "qcow", "qcow2", "qed", "qt", "r3d", "ra", "rar", "rm", "rmvb", "rtf", "rv", "rw2", "sh", "shtml", "sit", "sitx", "sketch", "spx", "sql", "srt", "svg", "swf", "tar", "tga", "tgz", "thmx", "tif", "tiff", "torrent", "ttf", "txt", "url", "vdi", "vhd", "vhdx", "vmdk", "vmem", "vob", "vswp", "vvfat", "wav", "wbmp", "webm", "webp", "wm", "wma", "wmv", "wpd", "wps", "xhtml", "xlsm", "xml", "xspf", "xvid", "yaml", "yml", "zip", "zipx"Configuring an inventory of digital machines that shouldn’t be encrypted can be potential.
When executing the encryptor, a risk actor should specify the beginning listing for encryption and a selected password tied to the encryptor.
When executed, the ransomware will decide whether it is operating in Linux, FreeBSD, or VMware ESXi server.
If it detects VMware ESXi, it is going to run the next esxcli and esxcfg-advcfg instructions, which we have now not seen in different ESXi encryptors previously.
for I in $(esxcli storage filesystem listing |grep 'VMFS-5' |awk '{print $1}'); do vmkfstools -c 10M -d eagerzeroedthick $I/eztDisk > /dev/null; vmkfstools -U $I/eztDisk > /dev/null; performed
for I in $(esxcli storage filesystem listing |grep 'VMFS-5' |awk '{print $1}'); do vmkfstools -c 10M -d eagerzeroedthick $I/eztDisk; vmkfstools -U $I/eztDisk; performed
for I in $(esxcli storage filesystem listing |grep 'VMFS-6' |awk '{print $1}'); do vmkfstools -c 10M -d eagerzeroedthick $I/eztDisk > /dev/null; vmkfstools -U $I/eztDisk > /dev/null; performed
for I in $(esxcli storage filesystem listing |grep 'VMFS-6' |awk '{print $1}'); do vmkfstools -c 10M -d eagerzeroedthick $I/eztDisk; vmkfstools -U $I/eztDisk; performed
esxcfg-advcfg -s 32768 /BufferCache/MaxCapacity
esxcfg-advcfg -s 20000 /BufferCache/FlushIntervalVMware knowledgeable Melissa Palmer informed BleepingComputer that these instructions have been possible copied from VMware assist bulletins to resolve a identified VMware reminiscence heap exhaustion bug and improve efficiency when executing ESXi instructions on the server.
Earlier than encrypting any detected digital machines, the ransomware will first terminate all VMs and delete their snapshots utilizing the next instructions:
esxcli vm course of listing
vim-cmd vmsvc/getallvms
esxcli vm course of kill -t drive -w %llu
vim-cmd vmsvc/snapshot.removeall %llu > /dev/null 2>&1All focused information will then be encrypted and have the configured extension appended to the file title.
In every folder, a ransom notice named [extension]_RECOVER.txt will probably be created that comprises hyperlinks to the ransomware gang’s Tor negotiation web site and the login credentials required to entry the sufferer’s chat web page.
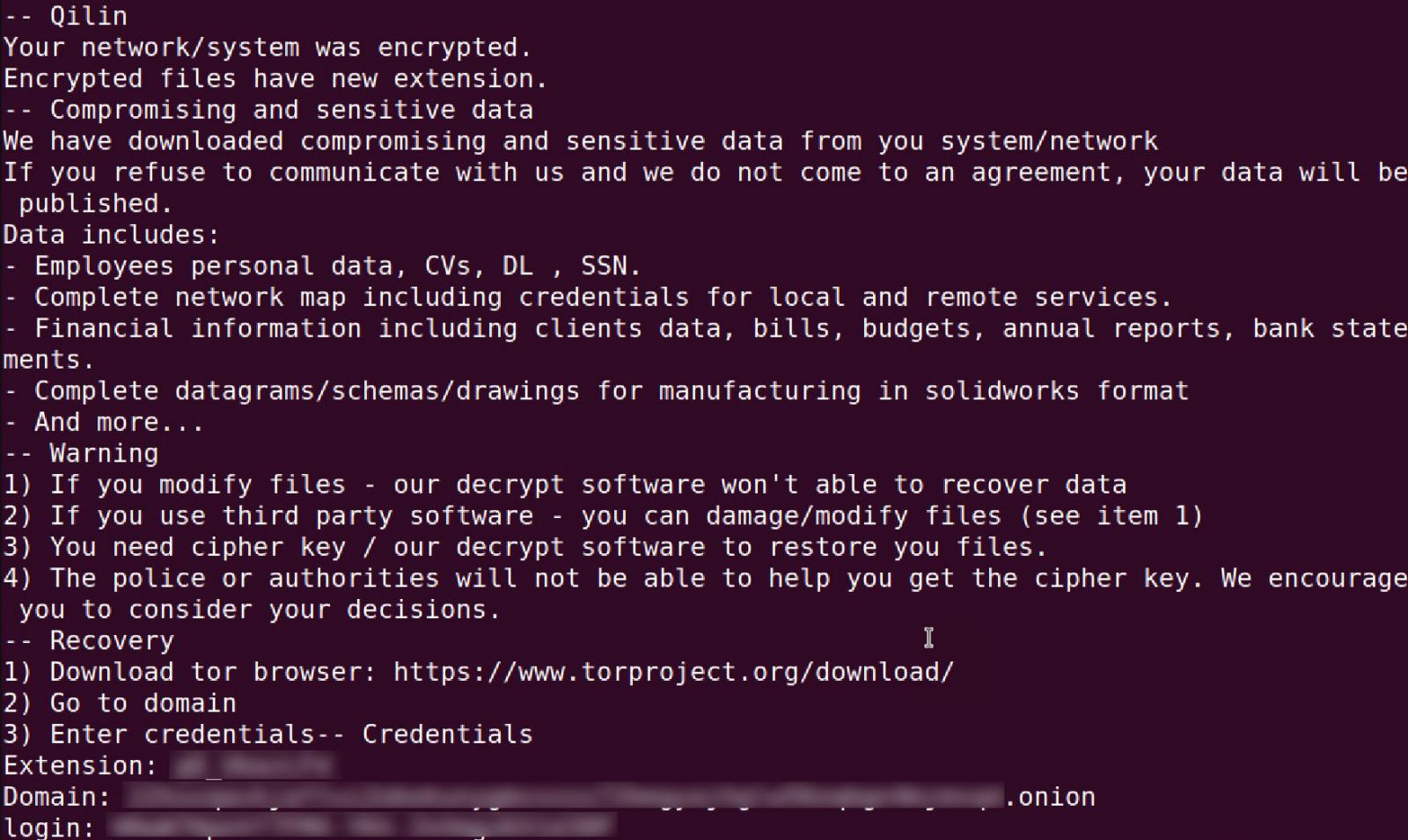
Supply: BleepingComputer
BleepingComputer has seen ransom calls for starting from $25,000 to tens of millions of {dollars}.
The Qilin ransomware operation
The Qilin ransomware operation was initially launched as “Agenda” in August 2022. Nonetheless, by September, it had rebranded beneath the title Qilin, which it continues to function as to this present day.
Like different enterprise-targeting ransomware operations, Qilin will breach an organization’s networks and steal knowledge as they unfold laterally to different programs.
When performed accumulating knowledge and gaining server administrator credentials, the risk actors deploy the ransomware to encrypt all units on the community.
The stolen knowledge and the encrypted information are then used as leverage in double-extortion assaults to coerce an organization into paying a ransom demand.
Since its launch, the ransomware operation has had a gentle stream of victims however has seen elevated exercise in the direction of the top of 2023.
A latest assault by Qilin was on the auto-parts large Yanfeng.

