
A number of information-stealing malware households are abusing an undocumented Google OAuth endpoint named “MultiLogin” to revive expired authentication cookies and log into customers’ accounts, even when an account’s password was reset.
Session cookies are a particular kind of browser cookie that accommodates authentication info, permitting an individual to robotically log in to web sites and providers with out getting into their credentials.
These kind of cookies are supposed to have a restricted lifespan, in order that they can’t be used indefinitely by menace actors to log into accounts if they’re stolen.
In late November 2023, BleepingComputer reported on two information-stealers, particularly Lumma and Rhadamanthys, who claimed they may restore expired Google authentication cookies stolen in assaults.
These cookies would permit the cybercriminals to achieve unauthorized entry to Google accounts even after the legit homeowners have logged out, reset their passwords, or their session has expired.
BleepingComputer has contacted Google a number of occasions over a month with questions on these claims and the way they plan to mitigate the problem, however we by no means obtained a response.
Exploiting Google OAuth endpoint
A report revealed right this moment by CloudSEK researchers sheds extra mild on how this zero-day exploit works and paints a dire image concerning the dimensions of its exploitation.
The exploit was first revealed by a menace actor named PRISMA on October 20, 2023, who posted on Telegram that they found a solution to restore expired Google authentication cookies.
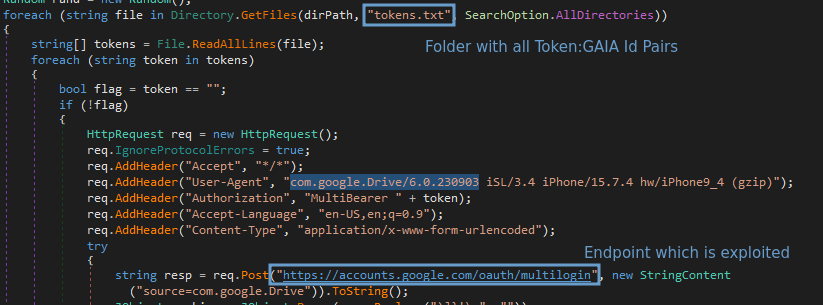
After reverse engineering the exploit, CloudSEK found it makes use of an undocumented Google OAuth endpoint named “MultiLogin,” which is meant for synchronizing accounts throughout completely different Google providers by accepting a vector of account IDs and auth-login tokens.
“This request is used to set chrome accounts in browser within the Google authentication cookies for a number of google web sites (e.g. youtube),” explains a description of the API endpoint within the Google Chrome supply code.
“This request is a part of Gaia Auth API, and is triggered each time accounts in cookies usually are not in step with accounts in browser,” a variable within the supply code additional explains.
CloudSEK says that information-stealing malware abusing this endpoint extracts tokens and account IDs of Chrome profiles logged right into a Google account. This stolen info accommodates two essential items of information: service (GAIA ID) and encrypted_token.
The encrypted tokens are decrypted utilizing an encryption saved in Chrome’s ‘Native State’ file. This identical encryption key can be used to decrypt saved passwords within the browser.
Utilizing the stolen token:GAIA pairs with the MultiLogin endpoint, the menace actors can regenerate expired Google Service cookies and keep persistent entry on compromised accounts.
Supply: CloudSEK
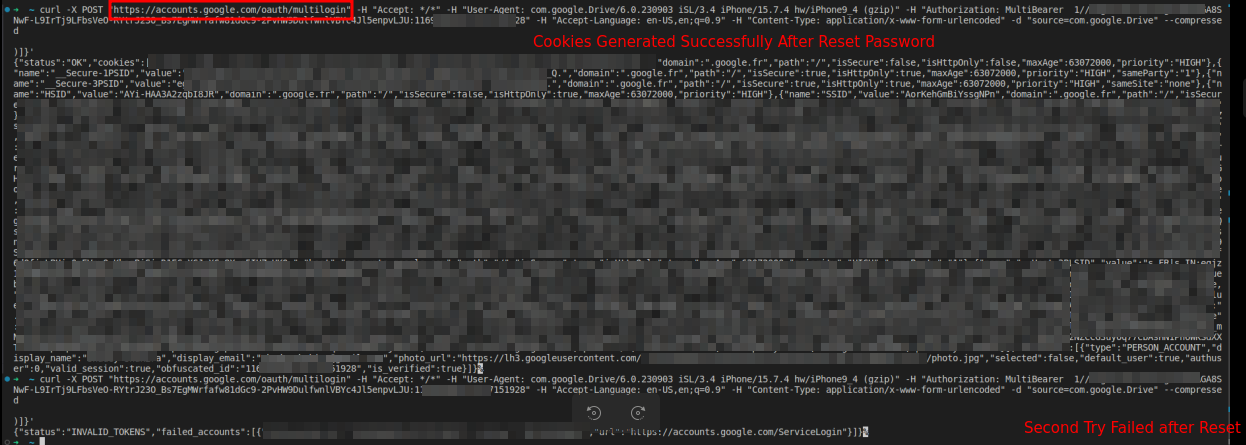
In a dialogue with CloudSek researcher Pavan Karthick, BleepingComputer was informed they reverse-engineered the exploit and have been in a position to make use of it to regenerate expired Google authentication cookies, as proven under.
Supply: CloudSEK
Nonetheless, Karthick defined that the authentication cookie can solely be regenerated as soon as if a consumer resets their Google password. In any other case, it may be regenerated a number of occasions, offering persistent entry to the account.
Malware devs rush so as to add exploit
Lumma stealer first adopted the exploit on November 14, whose builders utilized blackboxing strategies equivalent to encrypting the token:GAIA pair with non-public keys to cover the mechanism from rivals and stop the replication of the characteristic.
Nonetheless, others have been capable of copy the characteristic or incorporate PRISMA’s exploit into their stealers, with Rhadamanthys being the primary to observe on November 17.
Since then, quite a few different info stealers have adopted the exploit, together with Stealc on December 1, Medusa on December 11, RisePro on December 12, and Whitesnake on December 26.
So, no less than six info-stealers presently declare the flexibility to regenerate Google cookies utilizing this API endpoint.
Menace intelligence agency Hudson Rock has additionally revealed the next video on YouTube, the place a cybercriminal demonstrates how the cookie restoration exploit works.
A subsequent launch by Lumma up to date the exploit to counteract Google’s mitigations, suggesting that the tech large is aware of concerning the actively exploited zero-day flaw.
Particularly, Lumma turned to utilizing SOCKS proxies to evade Google’s abuse detection measures and applied encrypted communication between the malware and the MultiLogin endpoint.
Nonetheless, since Google hasn’t confirmed the abuse of the MultiLogin endpoint, the standing of the exploitation and its mitigation efforts stay unclear presently.
