The Operation Triangulation spyware and adware assaults focusing on Apple iOS units leveraged never-before-seen exploits that made it doable to even bypass pivotal hardware-based safety protections erected by the corporate.
Russian cybersecurity agency Kaspersky, which found the marketing campaign firstly of 2023 after changing into one of many targets, described it because the “most refined assault chain” it has ever noticed thus far. The marketing campaign is believed to have been energetic since 2019.
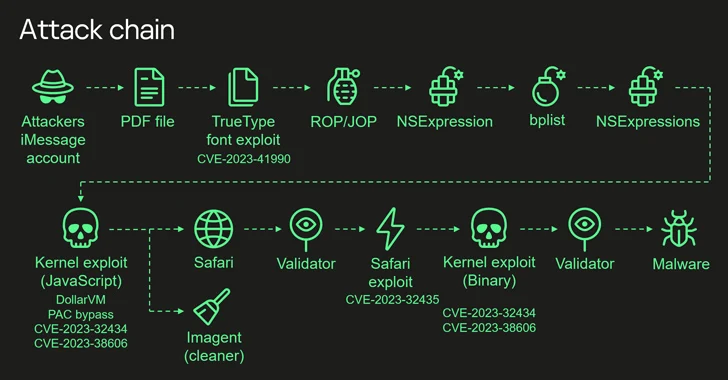
The exploitation exercise concerned the usage of 4 zero-day flaws that have been usual into a series to acquire an unprecedented degree of entry and backdoor goal units operating iOS variations as much as iOS 16.2 with the last word objective of gathering delicate data.
From USER to ADMIN: Study How Hackers Achieve Full Management
Uncover the key techniques hackers use to turn into admins, easy methods to detect and block it earlier than it is too late. Register for our webinar as we speak.
The start line of the zero-click assault is an iMessage bearing a malicious attachment, which is robotically processed sans any consumer interplay to finally get hold of elevated permissions and deploy a spyware and adware module. Particularly, it includes the weaponization of the next vulnerabilities –
- CVE-2023-41990 – A flaw within the FontParser element that might result in arbitrary code execution when processing a specifically crafted font file, which is shipped through iMessage. (Addressed in iOS 15.7.8 and iOS 16.3)
- CVE-2023-32434 – An integer overflow vulnerability within the Kernel that might be exploited by a malicious app to execute arbitrary code with kernel privileges. (Addressed in iOS 15.7.7, iOS 15.8, and iOS 16.5.1 )
- CVE-2023-32435 – A reminiscence corruption vulnerability in WebKit that might result in arbitrary code execution when processing specifically crafted internet content material. (Addressed in iOS 15.7.7 and iOS 16.5.1)
- CVE-2023-38606 – A difficulty within the kernel that allows a malicious app to switch delicate kernel state. (Addressed in iOS 16.6)
It is price noting that patches for CVE-2023-41990 have been launched by Apple in January 2023, though particulars in regards to the exploitation have been solely made public by the corporate on September 8, 2023, the identical day it shipped iOS 16.6.1 to resolve two different flaws (CVE-2023-41061 and CVE-2023-41064) that have been actively abused in reference to a Pegasus spyware and adware marketing campaign.
This additionally brings the tally of the variety of actively exploited zero-days resolved by Apple for the reason that begin of the 12 months to twenty.
Of the 4 vulnerabilities, CVE-2023-38606 deserves a particular point out because it facilitates a bypass of hardware-based safety safety for delicate areas of the kernel reminiscence by leveraging memory-mapped I/O (MMIO) registers, a characteristic that was by no means recognized or documented till now.
The exploit, particularly, targets Apple A12-A16 Bionic SoCs, singling out unknown MMIO blocks of registers that belong to the GPU coprocessor. It is presently not recognized how the mysterious menace actors behind the operation realized about its existence. Additionally unclear is whether or not it was developed by Apple or it is a third-party element like ARM CoreSight.
To place it in one other manner, CVE-2023-38606 is the essential hyperlink within the exploit chain that is carefully intertwined with the success of the Operation Triangulation marketing campaign, given the truth that it permits the menace actor to realize complete management of the compromised system.
“Our guess is that this unknown {hardware} characteristic was most probably supposed for use for debugging or testing functions by Apple engineers or the manufacturing facility, or that it was included by mistake,” safety researcher Boris Larin stated. “As a result of this characteristic will not be utilized by the firmware, we do not know how attackers would know easy methods to use it.”
“{Hardware} safety fairly often depends on ‘safety by obscurity,’ and it’s rather more troublesome to reverse-engineer than software program, however it is a flawed strategy, as a result of eventually, all secrets and techniques are revealed. Methods that depend on “safety by obscurity” can by no means be actually safe.”
The event comes because the Washington Publish reported that Apple’s warnings in late October about how Indian journalists and opposition politicians might have been focused by state-sponsored spyware and adware assaults prompted the federal government to query the veracity of the claims and describe them as a case of “algorithmic malfunction” throughout the tech large’s programs.
As well as, senior administration officers demanded that the corporate soften the political affect of the warnings and pressed the corporate to supply different explanations as to why the warnings might have been despatched. Thus far, India has neither confirmed nor denied utilizing spyware and adware comparable to these by NSO Group’s Pegasus.
Citing folks with information of the matter, the Washington Publish famous that “Indian officers requested Apple to withdraw the warnings and say it had made a mistake,” and that “Apple India’s company communications executives started privately asking Indian know-how journalists to emphasise of their tales that Apple’s warnings might be false alarms” to shift the highlight away from the federal government.