
Right now, the Akira ransomware gang claimed that it breached the community of Nissan Australia, the Australian division of Japanese automotive maker Nissan.
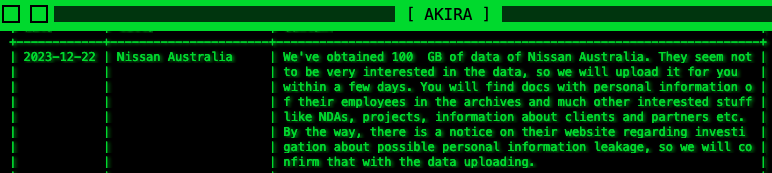
In a brand new entry added to the operation’s date leak weblog on December 22, Akira says that its operators allegedly stole round 100GB of paperwork from the automaker’s techniques.
The attackers have threatened to leak delicate enterprise and consumer knowledge on-line, as ransom negotiations with Nissan failed after the corporate both refused to have interaction or pay the ransom.
“They appear to not be very within the knowledge, so we’ll add it for you inside a couple of days,” the ransomware group says. “You can see docs with private info of their staff within the archives and far different stuff like NDAs, tasks, details about purchasers and companions and many others.”
Akira surfaced in March 2023 and drew consideration after shortly amassing a lot of victims from numerous business sectors.
In June 2023, Akira ransomware operators began deploying a Linux variant of their encryptor designed to focus on VMware ESXi digital machines broadly utilized in enterprise environments.
Based on negotiations seen by BleepingComputer, the ransomware group is asking for ransom funds from $200,000 to hundreds of thousands of {dollars}, relying on the breached group’s dimension.
Whereas one other ransomware pressure named Akira was launched 5 years in the past, in 2017, the 2 operations are unlikely to be associated.
Nissan nonetheless working to revive techniques
Whereas the corporate has but to attribute a cyberattack disclosed on December 5, it did add a brand new replace to its web site at the moment confirming that attackers have breached a few of its techniques in Australia and New Zealand.
Nissan says it is nonetheless investigating the incident’s impression and whether or not private info has been accessed. It is also engaged on restoring techniques affected within the assault (a course of that began on December 5, after the incident was disclosed.
“We can’t but affirm the extent of the cyber incident. We’re working with our world incident response group and cybersecurity consultants to research the incident as a matter of urgency,” Nissan stated.
“Some vendor techniques will likely be impacted nonetheless, your native Nissan Dealership is working. Please communicate on to your native Nissan vendor to help with all car and servicing queries.”
After detecting the breach, Nissan notified the Australian and the New Zealand Cyber Safety Centres and related privateness regulators and regulation enforcement our bodies.
Possible due to the danger that some knowledge saved on the compromised techniques was both accessed or stolen, Nissan additionally warned clients to “be vigilant for any uncommon or suspicious on-line exercise.”
Nissan has but to answer to a request for remark and extra info on the cyber incident from BleepingComputer.
