
Microsoft warns that financially-motivated menace actors are utilizing OAuth functions to automate BEC and phishing assaults, push spam, and deploy VMs for cryptomining.
OAuth (brief for Open Authorization) is an open commonplace for granting apps safe delegated entry to server sources primarily based on user-defined permissions by way of token-based authentication and authorization with out offering credentials.
Current incidents investigated by Microsoft Risk Intelligence consultants revealed that attackers primarily goal consumer accounts that lack strong authentication mechanisms (e.g., multi-factor authentication) in phishing or password-spraying assaults, specializing in these with permissions to create or modify OAuth apps.
The hijacked accounts are then used to create new OAuth functions and grant them excessive privileges, permitting their malicious exercise to stay hidden whereas guaranteeing continued entry even when the unique account is misplaced.
These high-privileged OAuth apps are utilized for a broad spectrum of illicit actions, together with deploying digital machines devoted to cryptocurrency mining, securing continued entry in Enterprise E-mail Compromise (BEC) assaults, and initiating spam campaigns that exploit the domains of compromised organizations.
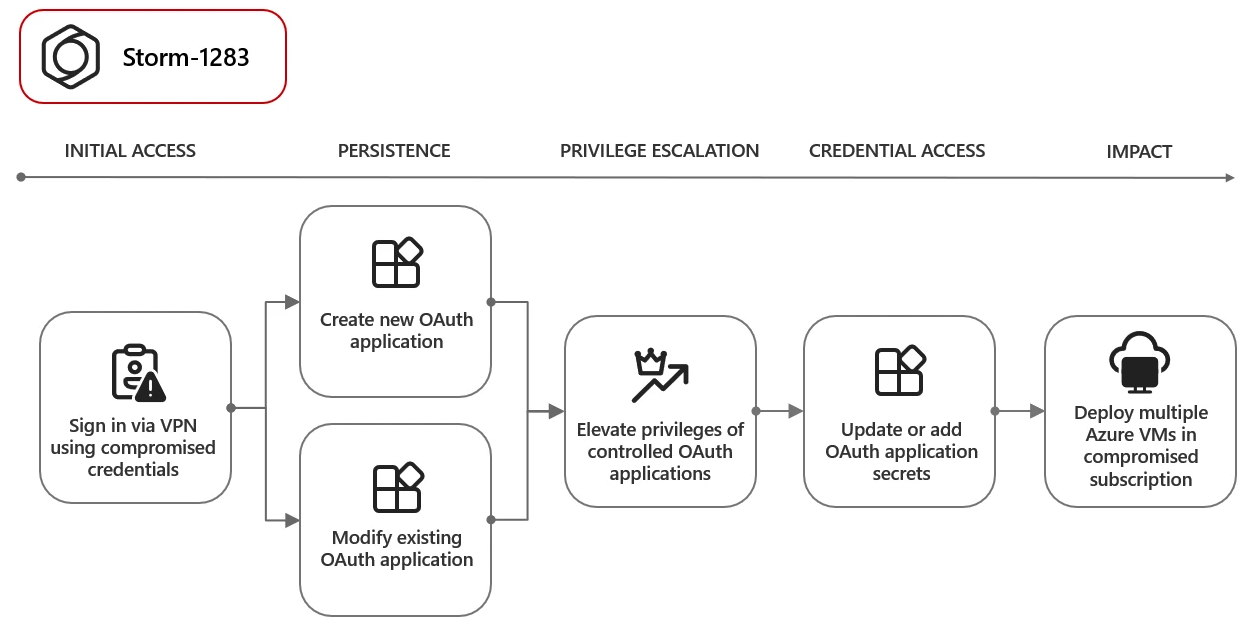
One notable occasion includes a menace actor tracked as Storm-1283, who created an OAuth app to deploy cryptocurrency mining digital machines. The monetary influence on focused organizations ranged from $10,000 to $1.5 million, relying on the assault’s length.
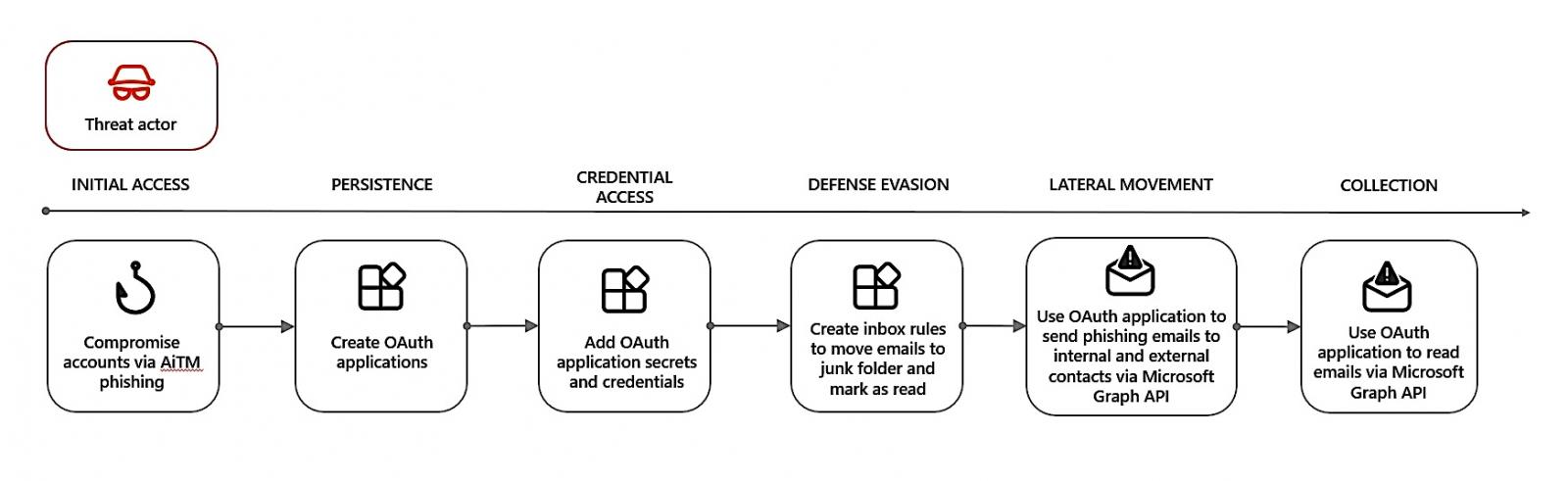
One other menace actor exploited OAuth apps created utilizing compromised accounts to keep up persistence and launch phishing campaigns utilizing an adversary-in-the-middle (AiTM) phishing package.
The identical assailant used the breached accounts for Enterprise E-mail Compromise (BEC) reconnaissance through the use of Microsoft Outlook Net Software (OWA) to seek for attachments linked to “fee” and “bill.”
In separate situations, the attacker created multitenant OAuth apps for persistence, including new credentials, and studying emails or sending phishing emails by way of the Microsoft Graph API.
“On the time of research, we noticed that menace actor created round 17,000 multitenant OAuth functions throughout totally different tenants utilizing a number of compromised consumer accounts,” Microsoft stated.
“Primarily based on the e-mail telemetry, we noticed that the malicious OAuth functions created by the menace actor despatched greater than 927,000 phishing emails. Microsoft has taken down all of the malicious OAuth functions discovered associated to this marketing campaign, which ran from July to November 2023.”
A 3rd menace actor tracked as Storm-1286 hacked consumer accounts that weren’t protected by multi-factor authentication (MFA) in a collection of password-spraying assaults.
The compromised accounts have been then used to create new OAuth apps within the focused group, which enabled the attackers to ship hundreds of spam emails daily and, in some instances, months after the preliminary breach.
To defend towards malicious actors misusing OAuth apps, Microsoft recommends utilizing MFA to thwart credential stuffing and phishing assaults.
Safety groups also needs to allow conditional entry insurance policies to dam assaults that leverage stolen credentials, steady entry analysis to routinely revoke consumer entry primarily based on threat triggers, and Azure Lively Listing safety defaults to make sure MFA is enabled and privileged actions are protected.
