Kiddowares ‘Parental Management – Children Place’ app for Android is impacted by a number of vulnerabilities that would allow attackers to add arbitrary recordsdata on protected units, steal consumer credentials, and permit kids to bypass restrictions with out the mother and father noticing.
The Children Place app is a parental management suite with 5 million downloads on Google Play, providing monitoring and geolocation capabilities, web entry and buying restrictions, display screen time administration, dangerous content material blocking, distant gadget entry, and extra.
Researchers at SEC Seek the advice of have discovered that the Children Place app variations 3.8.49 and older are weak to 5 flaws that would affect the security and privateness of its customers.
The 5 safety points are the next:
- Person registration and login actions return the unsalted MD5 hash of the password, which could be intercepted and simply decrypted. MD5 hashes are now not thought-about cryptographically safe, as they are often brute-forced utilizing fashionable computer systems.
- The customizable identify of the kid’s gadget could be manipulated to set off an XSS payload within the mum or dad internet dashboard. Youngsters or attackers can inject malicious scripts to execute on the mum or dad’s dashboard, reaching unauthorized entry. The difficulty has obtained the identifier CVE-2023-29079.
- All requests within the internet dashboard are weak to cross-site request forgery (CSRF) assaults. The assault requires information of the gadget ID, which is obtainable from the browser historical past. The difficulty has obtained the identifier CVE-2023-29078.
- An attacker might exploit the app’s dashboard characteristic, initially meant for folks to ship recordsdata as much as 10MB to their kid’s gadget, to add arbitrary recordsdata to an AWS S3 bucket. This course of generates a obtain URL which is then despatched to the kid’s gadget. No antivirus scan takes place on the uploaded recordsdata, so these can include malware.
- The app consumer (baby) can briefly take away all utilization restrictions to bypass parental controls. Exploiting the flaw, tracked as CVE-2023-28153, doesn’t generate a notification to the mum or dad, so it goes unnoticed until a guide test is carried out on the dashboard.
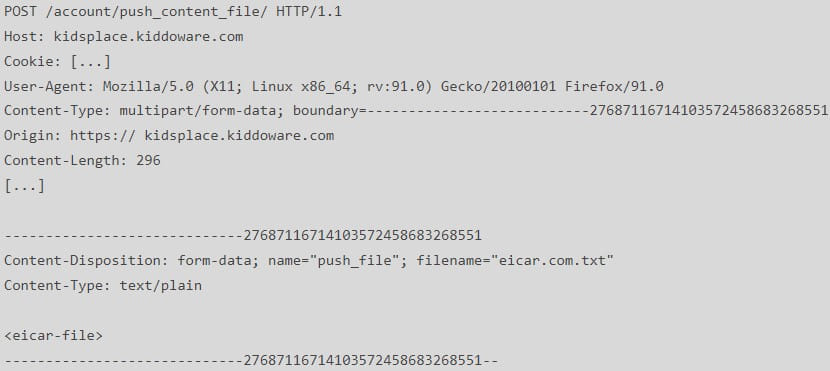
SEC Seek the advice of’s report accommodates proof-of-concept requests or step-by-step directions on exploiting the above points, making it straightforward for risk actors to take advantage of the vulnerabilities on older variations of the apps or for kids to bypass restrictions.
Subsequently, it’s important to replace to a safe model of the app, which is 3.8.50 or later.
The analysts found the issues on November 23, 2022, whereas testing Children Place 3.8.45 and reported it to the seller, Kiddoware.
The seller ultimately addressed all issues with model 3.8.50, launched on February 14, 2023.
App customers can replace to the newest model by opening the Google Play retailer, tapping their account icon, deciding on ‘Handle apps & gadget,’ and tapping on ‘Verify for updates.’
Alternatively, long-press the app’s icon after which choose App information → App particulars → Replace.

