Recruiters and anybody else concerned in hiring processes needs to be educated about this social engineering assault risk.
A brand new report from U.S.-based cybersecurity firm Proofpoint exposes a brand new assault marketing campaign operated by a financially-oriented risk actor dubbed TA4557 with excessive monetary knowledge theft dangers and presumably extra dangers akin to mental property theft.
On this social engineering marketing campaign, the risk actor targets recruiters with benign content material earlier than infecting their machines with the More_Eggs malware. This risk actor takes further care to keep away from being detected.
Leap to:
How recruiters are focused by risk actor TA4557
The newest assault marketing campaign from risk actor TA4557, as uncovered by Proofpoint, targets recruiters by sending them a direct electronic mail. The group pretends to be a person involved in a job (Determine A).
Determine A
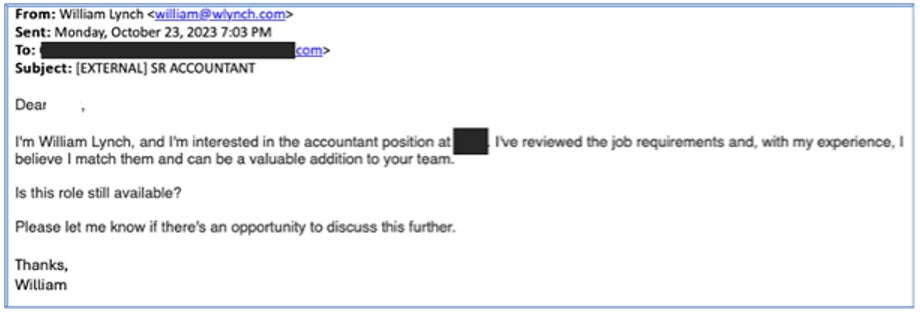
The e-mail doesn’t embody any malicious content material. As soon as the recruiter replies to the e-mail, the attacker replies with a hyperlink resulting in an attacker-controlled web site posing as a person’s resume (Determine B).
Determine B
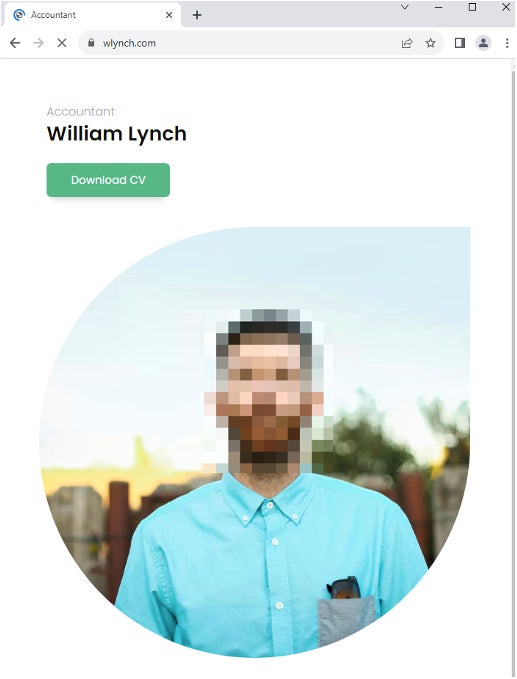
An alternate technique utilized by the risk actor consists of replying to the recruiter with a PDF or Microsoft Workplace Phrase file containing directions to go to the pretend resume web site.
An infection results in More_Eggs malware
The web site employs filtering mechanisms to evaluate whether or not the next section of the assault needs to be initiated. If the factors for filtering should not met, the person is introduced with a plain textual content resume. If the filtering checks are efficiently handed, the person is redirected to the candidate web site, the place they’re prompted to resolve a CAPTCHA.
Upon profitable completion, the person is supplied with a ZIP file that features a Microsoft Home windows shortcut (LNK) file. If executed, the LNK file abuses a reliable software program ie4uinit.exe to obtain and run a scriptlet from a location saved within the ie4uinit.inf file. The approach often called Residing Off The Land consists of utilizing present reliable software program and instruments to perform malicious actions on the system, which minimizes the chance of being detected.
The downloaded scriptlet decrypts and drops a DLL file earlier than trying to create a brand new course of to execute the DLL by utilizing Home windows Administration Instrumentation. If it fails, the scriptlet tries one other method by utilizing the ActiveX Object Run technique.
As soon as the DLL is executed, it decrypts the More_Eggs malware together with the reliable MSXSL executable. Then, it initiates the creation of the MSXSL course of utilizing the WMI service. The DLL deletes itself as soon as the infecting course of is completed.
In response to Proofpoint, More_Eggs is a malware that allows persistence and profiling of the contaminated system; additionally it is usually used to obtain extra payloads.
A discreet but environment friendly risk actor
TA4557 employs varied methods to evade detection and keep a low profile, demonstrating a dedication to staying beneath the radar.
In different assault campaigns, principally in 2022 and 2023, the risk actor used a special approach that primarily consisted of making use of for open positions on job provide web sites. The risk actor used malicious URLs or recordsdata containing malicious URLs within the software, however the URLs weren’t hyperlinked, which means the recipient needed to copy and paste the URLs instantly into their browser. That approach is attention-grabbing as a result of the usage of such a hyperlink will probably not set off as many safety alarms. In response to Proofpoint researchers, TA4557 nonetheless makes use of that approach in parallel with the newly reported approach.
As well as, the risk actor beforehand created pretend LinkedIn profiles, pretending to be a recruiter and reaching out to individuals searching for a job.
The usage of LOTL methods is a sign that the risk actor tries to remain discreet and undetected.
The DLL file utilized by the risk actor employs anti-sandbox and anti-analysis methods, akin to incorporating a loop strategically crafted to increase the execution time whereas slowly retrieving the RC4 key wanted to decipher the More_Eggs backdoor. A number of checks are additionally performed to see if the code is operating in a sandbox or in a debugging setting. As soon as the an infection course of has gone by, the DLL deletes itself to take away proof of its presence and render incident evaluation tougher.
TA4557 is described by Proofpoint as a “expert, financially motivated risk actor” who demonstrates sophistical social engineering. The group frequently adjustments its sender emails, pretend resume domains and infrastructure. Proofpoint believes the identical risk actor focused anti-money laundering officers at U.S. credit score unions in 2019.
From a worldwide viewpoint, the researchers seen a rise in risk actors partaking their targets utilizing benign content material first to construct confidence in the course of the interplay earlier than sharing dangerous content material.
Find out how to defend from this malware risk
TA4557 makes use of social engineering to contaminate the machines of unsuspecting victims, that are recruiters on this assault marketing campaign; previously, the risk actor additionally focused people searching for jobs. So, it’s suggested to coach all individuals concerned in hiring processes about these sorts of social engineering methods.
It’s endorsed by no means to open a doc or click on on a hyperlink that appears suspicious. When doubtful, workers should alert their IT division and have the paperwork or hyperlinks analyzed.
Safety options have to be deployed on all endpoints, and alerts needs to be rigorously analyzed.
Electronic mail content material needs to be analyzed by safety options able to detecting anomalies as an alternative of solely URLs or hooked up recordsdata to attempt to detect social engineering-based campaigns.
All working techniques and software program have to be saved updated and patched to keep away from being compromised by widespread vulnerabilities.
Disclosure: I work for Pattern Micro, however the views expressed on this article are mine.

