
The Qilin ransomware group has claimed duty for a cyber assault on Yanfeng Automotive Interiors (Yanfeng), one of many world’s largest automotive components suppliers.
Yanfeng is a Chinese language automotive components developer and producer targeted on inside elements and employs over 57,000 folks in 240 areas worldwide.
It sells inside elements to Common Motors, the Volkswagen Group, Ford, Stellantis (Fiat, Chrysler, Jeep, Dodge), BMW, Daimler AG, Toyota, Honda, Nissan, and SAIC Motor. The corporate constitutes an important a part of the availability chain for these automakers.
Earlier this month, it was reported that Yanfeng was impacted by a cyberattack that immediately affected Stellantis, forcing the automotive firm to cease manufacturing at its North American vegetation.
The Chinese language firm remained unresponsive to inquiries for feedback concerning the state of affairs. Nevertheless, its predominant web site was inaccessible till yesterday, when it returned on-line with none statements concerning the outage.
Stellantis advised BleepingComputer they suffered a disruption on account of an “subject” at an exterior provider.
“Attributable to a problem with an exterior provider, manufacturing at a few of Stellantis’ North America meeting vegetation was disrupted the week of November 13,” Stellantis shared in an announcement.
“Full manufacturing in any respect impacted vegetation had resumed by November 16.”
Qilin claims the assault
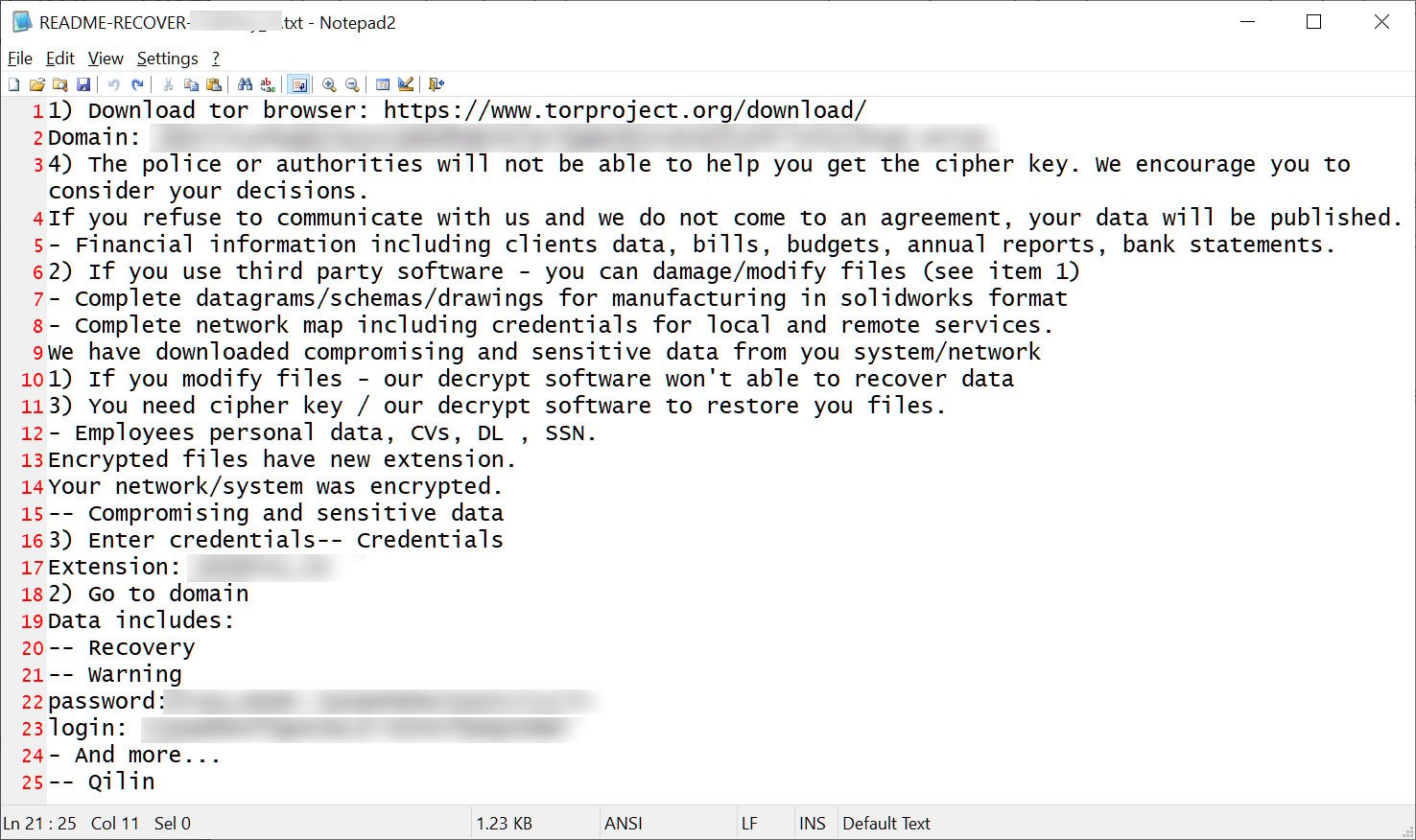
The Qilin ransomware group, also called “Agenda,” claimed the assault on Yanfeng by including them to their Tor information leak extortion website yesterday.
The menace actors revealed a number of samples to show their alleged entry to Yanfeng techniques and recordsdata, together with monetary paperwork, non-disclosure agreements, citation recordsdata, technical information sheets, and inside studies.

Qilin has threatened to launch all information of their possession within the coming days, however no particular deadline was set.
The Qilin ransomware gang launched its RaaS (ransomware as a service) platform on the finish of August 2022 beneath the title ‘Agenda.’
In 2023, the menace actors rebranded their ransomware beneath the title ‘Qilin,’ which they function beneath in the present day.
Supply: BleepingComputer
The menace actors goal firms in all sectors, and plenty of assaults characteristic customization within the course of termination and file extension modifications to maximise affect.
Group-IB managed to infiltrate Qilin’s operations and revealed a report in Might 2023 to share the intelligence it collected, together with particulars concerning the gang’s recruiting, admin panel options, and goal exclusions.
