Assaults on software program provide chains elevated dramatically in 2023, with a rise of 200% in comparison with 2022, in response to Sonatype’s new report. Additionally, vulnerabilities are nonetheless current in downloaded dependencies, which is a purpose why extra laws and processes in software program improvement are wanted.
This analysis from Sonatype, a U.S.-based firm specializing in software program provide chain administration and safety, additionally covers builders’ challenges and the potential advantages to utilizing AI safety options.
Leap to:
Assaults on open supply software program to unfold malicious packages
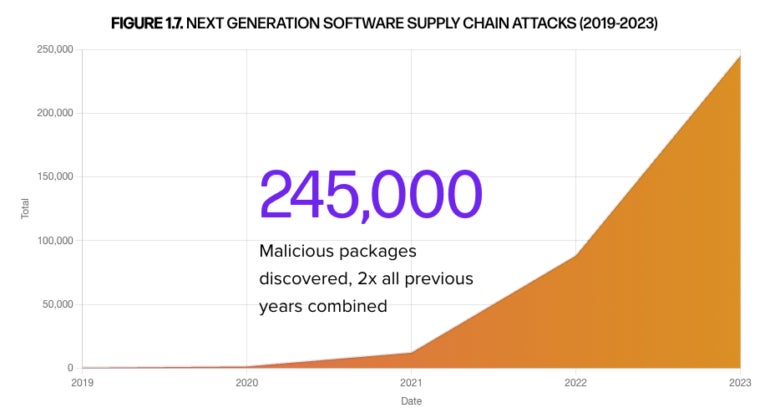
Based on Sonatype’s report, 2022 noticed an enormous enhance of malicious assaults on the open supply software program provide chain, which has stored rising in 2023. The year-over-year monitoring exhibits 245,032 malicious packages as of September 2023, which is 3 times the variety of malicious packages seen in 2022 or two occasions all earlier years mixed (Determine A). Sonatype’s analysis is according to the European Union Company for Cybersecurity’s reporting in late 2022 that the compromise of software program provide chains by way of software program dependencies is the primary rising risk.
Determine A
Due to this large enhance in assaults, many open-source techniques have applied new safety insurance policies and enhancements, comparable to necessary multifactor authentication for builders; nevertheless, oftentimes, malicious packages are dealt with the identical as packages with vulnerabilities, which means they’re taken down the identical manner as vulnerabilities, which is inappropriate for malicious content material, because the packages may keep on-line longer for that purpose.
Of the survey respondents, that is how lengthy it takes to mitigate a vulnerability of their group from the second it’s detected (Determine B):
- Between per week and by no means: 39%
- Lower than a day: 19.2%
- Greater than per week: 36.2%
- Lower than an hour: 3.1%
Determine B

Concerning repository downloads, practically 96% of elements downloads with recognized vulnerabilities may very well be prevented, as fixes had been already accessible on the time of obtain. This exhibits that organizations should pay nearer consideration to the variations of software program they set up. As a foul instance, susceptible variations of Log4j nonetheless account for practically 1 / 4 of all new downloads of that software program.
From the typical 37.8 billion month-to-month downloads from the Maven Central repository, 3.97 billion susceptible elements had been consumed.
“Our business must direct its efforts in the direction of the appropriate place. The truth that there’s been a repair for nearly all downloads of elements with a recognized vulnerability tells us an instantaneous focus needs to be supporting builders to turn into higher decision-makers, and giving them entry to the appropriate instruments,” mentioned Brian Fox, chief technical officer at Sonatype, in an interview with TechRepublic.
Development in whole open supply ecosystem
It’s additionally attention-grabbing to notice that the entire open supply ecosystem has grown. The highest 4 main open supply ecosystems — Java (Maven), JavaScript (rpm), Python (PyPI) and .NET (NuGet Gallery) — all present a YoY share between 27% and 28% for challenge development, with 367,000 as much as 2.5M tasks per ecosystem (Determine C).
Determine C

This development exhibits a rise in software program productiveness after a slowdown between 2020 and 2022, most likely as a result of COVID-19 pandemic. One other rationalization, in response to Sonatype, may very well be that ” … a variety of these tasks are in truth coming from business exercise and never folks with spare time, which was in abundance in the course of the pandemic.”
Preventing vulnerabilities in open supply software program
The most effective technique for figuring out vulnerabilities in software program is code evaluate (Determine D), the place code adjustments are peer-reviewed earlier than being put on-line.
Determine D

Second comes the binary checks: When a bundle comprises a binary, it must be correctly checked for vulnerabilities. Mission dependencies additionally should be pinned to particular variations.
Department safety is critical on the “default” and “launch” branches to forestall maintainers from circumventing workflows comparable to steady integration exams or code evaluate when updating.
As well as, it’s vital to make use of tasks which can be well-maintained, as a result of they present decrease charges of vulnerabilities. As said by Sonatype, ” … enterprises trying to reduce their open supply vulnerability danger ought to select well-maintained tasks that carry out code evaluate and monitor them to make sure they haven’t reached end-of-life.”
SEE: Guidelines: Community and techniques safety (TechRepublic Premium)
Builders’ challenges and the open supply dependency administration drawback
Software program provide chain safety is advanced and is impacted by numerous elements. As an illustration, along with builders’ programming challenges, they face obligations of their work, comparable to making knowledgeable selections relating to open-source elements for his or her software program tasks. The dependency administration has been often known as “dependency hell” in builders’ communities and could be very troublesome to cope with.
For instance, the typical Java software wants 148 dependencies, with round 10 annual releases. For growing that software, the developer must rigorously choose and handle these 148 dependencies, but also needs to observe a median of 1,500 dependency adjustments per yr. That monitoring wants safety and authorized experience that not all builders have in an effort to select the most secure variations.
Including stress on the builders to be environment friendly and quick can result in them feeling overwhelmed, leading to weaker selections.
These dependency selections are additionally altered by software program recognition, which tends to convey a false feeling of security, as in style code isn’t essentially safe code. Inactive releases, which characterize 85% of tasks in repositories, overwhelm builders with accessible choices.
To assist resolve this drawback, Sonatype has developed a scoring system primarily based on 5 key dimensions: safety, license, age, recognition and launch stability (Determine E).
Determine E

A cautious evaluation of these elements facilitates selections in software program provide chain administration. It’s additionally advisable to make use of repository administration software program that may be custom-made to organizations’ wants and helps builders to cease losing time in dealing with too many updates.
Software program provide chain laws
Whereas we’re nonetheless within the early levels of laws for software program provide chains, it appears vital sufficient to see steerage and regulation emerge in lots of nations. The regulatory actions from key nations such because the U.S., Europe, U.Okay., Australia, Canada, Japan and New Zealand present a shared motivation to enhance digital defenses and shield organizations’ infrastructures.
Software program producers are prone to face extra obligations and liabilities when their software program doesn’t inherently combine a safety function, whereas strong processes to handle cybersecurity incidents should be deployed in all organizations.
Extra worldwide collaboration might be essential to extend safety in software program improvement. As said by Sonatype in its report, laws ” … in addition to future associated initiatives will play a pivotal function in shaping the way forward for cybersecurity insurance policies and practices at scale worldwide.”
Advantages to utilizing AI-driven safety options
Synthetic intelligence and machine studying are applied sciences with the facility to reshape software program improvement.
AI has been broadly adopted in response to the survey, with 97% at the moment incorporating generative AI of their workflow to some extent. And, 47% of DevOps and 57% of SecOps respondents reported using AI saved them greater than six hours per week.
From a safety standpoint, AI-driven options can establish vulnerabilities or bugs in software program code sooner and extra effectively than conventional strategies. There are advantages for builders of all ranges.
Senior builders can leverage AI instruments to finish tedious duties and develop elements of their code, whereas junior builders profit from having AI instruments reply their questions effectively whereas offering perception into technical phrases and jargon. Each junior and senior builders can use queries to develop fundamental code quick whereas permitting them to give attention to extra advanced points of their tasks. AI instruments may even be used as useful debugging instruments along with producing code.
Watch out when deploying and monitoring AI instruments
AI instruments, notably giant language fashions, want cautious monitoring and shouldn’t function in an automatic manner. LLMs may expertise false data or hallucinations, which needs to be detected and cared for.
LLM-as-a-service accelerates improvement and improves performances, but may be pricey (enterprises pay for every token despatched and acquired) when closely used. Furthermore, the organizations subscribing to it are ” … susceptible to vendor outages, deprecated options, or unexpected adjustments in mannequin efficiency that will not align with the precise activity at hand” as said by Sonatype.
When utilized in organizations, open-source LLMs should be rigorously deployed. The fashions used should be rigorously chosen (there are greater than 300,000 fashions accessible) in response to the applying and tuned to the computational necessities and efficiency of the construction. A licensing danger exists; a mannequin that’s launched underneath a license that restricts business use or requests particular circumstances may result in a phrases violation if not examined rigorously.

