Authored by Fernando Ruiz
McAfee Cellular Analysis Group recognized an Android backdoor carried out with Xamarin, an open-source framework that permits constructing Android and iOS apps with .NET and C#. Dubbed Android/Xamalicious it tries to achieve accessibility privileges with social engineering after which it communicates with the command-and-control server to judge whether or not or to not obtain a second-stage payload that’s dynamically injected as an meeting DLL at runtime stage to take full management of the machine and doubtlessly carry out fraudulent actions equivalent to clicking on advertisements, putting in apps amongst different actions financially motivated with out person consent.
The second stage payload can take full management of the contaminated machine because of the highly effective accessibility providers that had been already granted through the first stage which additionally incorporates features to self-update the principle APK which signifies that it has the potential to carry out any kind of exercise like a adware or banking trojan with out person interplay. Nonetheless, we recognized a hyperlink between Xamalicious and the ad-fraud app “Money Magnet” which robotically clicks advertisements, installs apps, and different actions to fraudulently generate income whereas customers that put in it might earn factors which might be imagined to be redeemable as a retail reward card. Which means that the builders behind these threats are financially motivated and drive ad-fraud subsequently this may be one of many important payloads of Xamalicious.
The utilization of the Xamarin framework allowed malware authors to remain energetic and with out detection for a very long time, profiting from the construct course of for APK recordsdata that labored as a packer to cover the malicious code. As well as, malware authors additionally carried out totally different obfuscation methods and customized encryption to exfiltrate information and talk with the command-and-control server.
We’ve recognized about 25 totally different malicious apps that carry this menace. Some variants have been distributed on Google Play since mid-2020. The apps recognized on this report had been proactively eliminated by Google from Google Play forward of our reporting. McAfee is a member of the App Protection Alliance and an energetic associate within the malware mitigation program, which goals to shortly discover Probably Dangerous Purposes (PHAs) and cease them earlier than they ever make it onto Google Play. Android customers are protected by Google Play Shield, which may warn customers of recognized malicious apps on Android gadgets. McAfee Cellular Safety detects this menace as Android/Xamalicious.
Based mostly on the variety of installations these apps could have compromised no less than 327,000 gadgets from Google Play plus the installations coming from third-party markets that regularly produce new infections primarily based on the detection telemetry of McAfee purchasers all over the world. This menace stays very energetic.
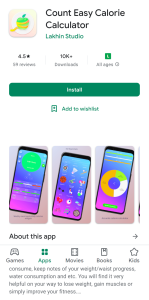
Determine 1. “Rely Straightforward Calorie Calculator” was accessible on Google Play on August 2022 and carries Android/Xamalicious
Android/Xamalicious trojans are apps associated to well being, video games, horoscope, and productiveness. Most of those apps are nonetheless accessible for obtain in third-party marketplaces.
Beforehand we detected malware abusing Xamarin framework such because the open-sourced AndroSpy and forked variations of it, however Xamalicious is carried out in another way. Technical particulars about Xamarin structure are properly documented and element how .NET code is interpreted by Android utilizing Mono.
Acquiring Accessibility Providers
Let’s use the app “Numerology: Private horoscope & Quantity predictions” for instance. As soon as began it instantly requests the sufferer to allow accessibility providers for “appropriate work” and supplies instructions to activate this permission:
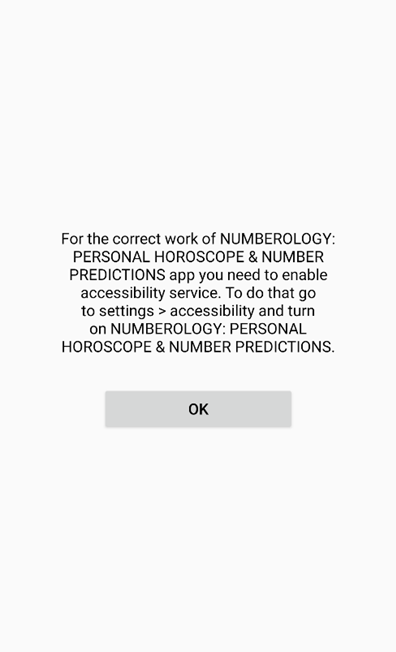
Determine 2. Tricking customers into granting accessibility providers permission
Customers have to manually activate the accessibility providers after a number of OS warnings equivalent to the next on the accessibility choices:
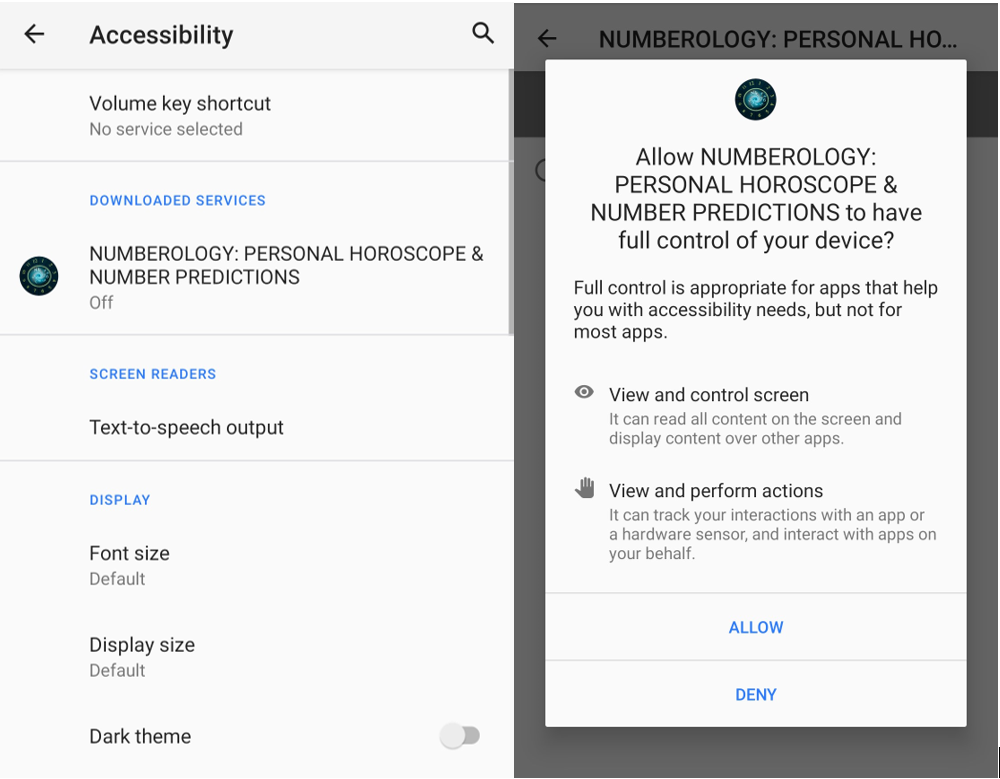
Determine 3. Accessibility providers configuration immediate highlights the dangers of this permission.
The place is the malicious code?
This isn’t the standard Java code or native ELF Android utility, the malware module was written initially in .NET and compiled right into a dynamic hyperlink library (DLL). Then it’s LZ4 compressed, and it may be embedded right into a BLOB file, or instantly accessible within the /assemblies listing on the APK construction. This code is loaded then by a local library (ELF) or by the DEX file at runtime stage. In easy phrases, which means that in some samples the reversing of the DLL assemblies is easy whereas in others it requires additional steps to unpack them.
The malicious code is normally accessible in two totally different meeting recordsdata within the /assemblies listing on the apk. Often, file names are core.dll and a <package-specific>.dll.
Some malware variants has obfuscated the DLL assemblies to keep away from evaluation and reversing of the malicious code whereas others maintain the unique code accessible.
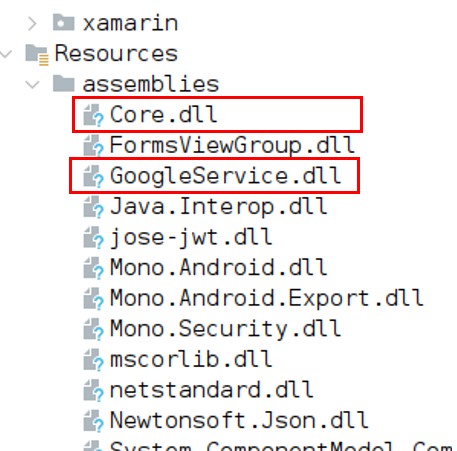
Determine 4. Core.dll and GoogleService.dll comprise malicious code.
Communication with the command-and-control server
As soon as accessibility permissions are granted the malware initiates communication with the malicious server to dynamically load a second-stage payload.
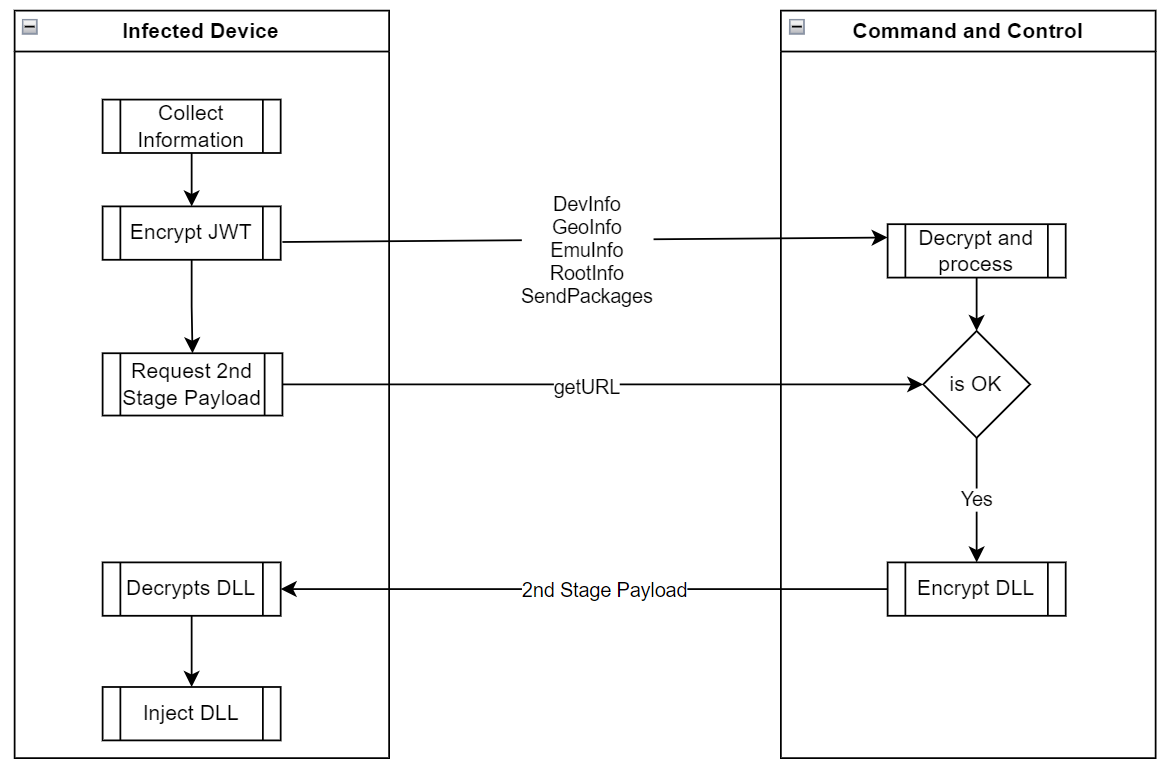
Determine 5. App execution and communication with the malicious server
Gather Gadget Info
Android/Xamalicious collects a number of machine information together with the checklist of put in purposes obtained through system instructions to find out if the contaminated sufferer is an effective goal for the second stage payload. The malware can accumulate location, provider, and community data amongst machine rooting standing, adb connectivity configuration, as an example, if the machine is linked through ADB or is rooted, the C2 won’t present a second-stage payload DLL for obtain.
| Technique/Command | Description |
| DevInfo | {Hardware} and machine data that features:
|
| GeoInfo | Location of the machine primarily based on IP handle, the malware contacts providers equivalent to api.myip.com to confirm the machine location and ISP information.
FraudScore: Self-protection to establish if the machine just isn’t an actual person |
| EmuInfo | It lists all adbProperties that in an actual machine are round 640 properties. This checklist is encoded as a string param in URL encoded format. This information could also be used to determinate if the affected shopper is an actual machine or emulator because it incorporates params equivalent to:
|
| RootInfo | After attempting to establish if the machine is rooted or not with a number of methods the output is consolidated on this command |
| Packages | It makes use of the system instructions “pm checklist packages -s” and “pm checklist packages -3” to checklist system and put in apps on the machine. |
| Accessibility | It supplies the standing if accessibility providers permissions are granted or not |
| GetURL | This command solely supplies the Android Id and it’s a request for the second-stage payload. The C2 evaluates the supplied shopper request and returns a standing and an encrypted meeting DLL. |
Knowledge Encryption in JWT
To evade evaluation and detection, malware authors encrypted all communication and information transmitted between the C2 and the contaminated machine, not solely protected by HTTPS, it’s encrypted as a JSON Net Encryption (JWE) token utilizing RSA-OAEP with a 128CBC-HS256 algorithm nonetheless the RSA key values utilized by the Xamalicious are hardcoded within the decompiled malicious DLL so decryption of transmitted data is feasible if C2 infrastructure is accessible through the evaluation.
Within the Ship() perform Android/Xamalicious first prepares the obtained object, normally a JSON construction calling the perform encrypt() which creates the JWT utilizing a hardcoded RSA key. So the info is exfiltrated absolutely encrypted to the malware host pointing to the trail “/Updater” through HTTP POST methodology.
Then it waits for the C2 response and passes it to the decrypt() perform which has a hardcoded RSA non-public key to correctly decrypt the obtained command which could comprise a second stage payload for the “getURL” command.
Encrypt Technique:
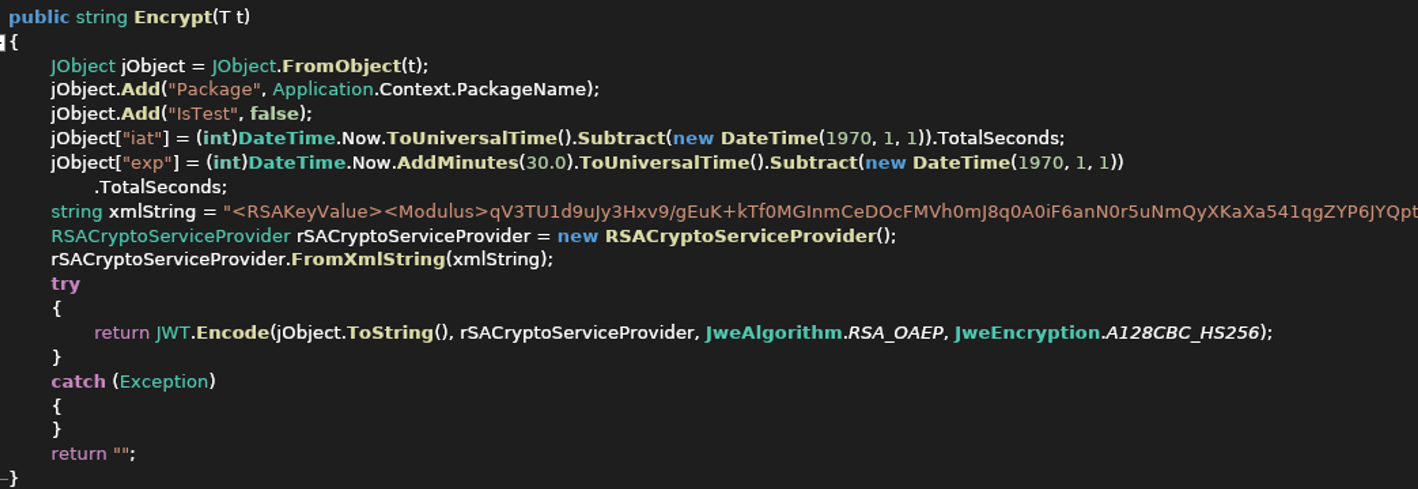
Determine 6. Encrypt perform with hardcoded RSA Key values as XML string
The decryption methodology can also be hardcoded into malware which allowed the analysis group to intercept and decrypt the communication from the C2 utilizing the RSA key values supplied as XML string it’s attainable to construct a certificates with the parameters to decrypt the JWE tokens content material.
C2 analysis
Collected information is transmitted to the C&C to find out if the machine is a correct goal to obtain a second-stage payload. The self-protection mechanism of the malware authors goes past conventional emulation detection and nation code operator limitations as a result of on this case, the command-and-control server won’t ship the second stage payload if the machine is rooted or linked as ADB through USB or doesn’t have a SIM card amongst a number of different atmosphere validations.
DLL Customized Encryption
With the getURL command, the contaminated shopper requests the malicious payload, if the C&C Server determines that the machine is “Okay” to obtain the malicious library it should encrypt a DLL with Superior encryption normal (AES) in Cipher block chaining (CBC) utilizing a customized key for the shopper that requested it primarily based on the machine id and different parameters defined under to decrypt the code because it’s a symmetric encryption methodology, the identical key works for encryption and decryption of the payload.
Delivers the Payload in JWT
The encrypted DLL is inserted as a part of the HTTP response within the encrypted JSON Net Token “JWT”. Then the shopper will obtain the token, decrypt it, after which decrypt the ‘url’ parm with AES CBC and a customized key.
The AES key used to decrypt the meeting is exclusive per contaminated machine and its string of 32 chars of size incorporates appended the machine ID, model, mannequin, and a hardcoded padding of “1” as much as 32 chars of size.
As an illustration, if the machine ID is 0123456ABCDEF010 and the affected machine is a Pixel 5, then the AES secret’s: “0123456ABCDEF010googlePixel 5111”
Which means that the DLL has a number of layers of encryption.
- It’s a HTTPS protected.
- It’s encrypted as a JWE Token utilizing RSA-OAEP with a 128CBC-HS256 algorithm.
- URL parameter that incorporates the DLL is encrypted with AES and encoded as base64
All these efforts are associated to hiding the payload and attempting to remain underneath the radar the place this menace had relative success since some variants may need been energetic years in the past with out AV detections.
DLL Injected
Xamalicious will identify this DLL “cache.bin” and retailer it within the native system to lastly dynamically load it utilizing the Meeting.Load methodology.
As soon as the second stage payload has been loaded the machine might be absolutely compromised as a result of as soon as accessibility permissions are granted, it could obverse and work together with any exercise opening a backdoor to any kind of malicious exercise.
Through the evaluation, the downloaded second stage payload contained a DLL with the category “MegaSDKXE” which was obfuscated and incomplete in all probability as a result of the C2 didn’t obtain the anticipated params to offer the whole malicious second stage that may be restricted to a selected provider, language, app put in, location, time zone or unknown situations of the affected machine, nonetheless, we will guarantee that it is a high-risk backdoor that leaves the chance to dynamically execute any command on the affected machine not restricted to spying, impersonation or as a financially motivated malware.
Money Magnet Advert-Fraud and Xamalicious
One of many Xamalicious samples detected by McAfee Cellular generic signatures was “LetterLink” (com.regaliusgames.llinkgame) which was accessible on Google Play on the finish of 2020, with a ebook icon. It was poorly described as a hidden model of “Money Magnet”: An app that performs ad-fraud with automated clicker exercise, apps downloads, and different duties that result in monetization for internet online affiliate marketing. This utility gives customers factors which might be imagined to be redeemable by retail reward playing cards or cryptocurrency.
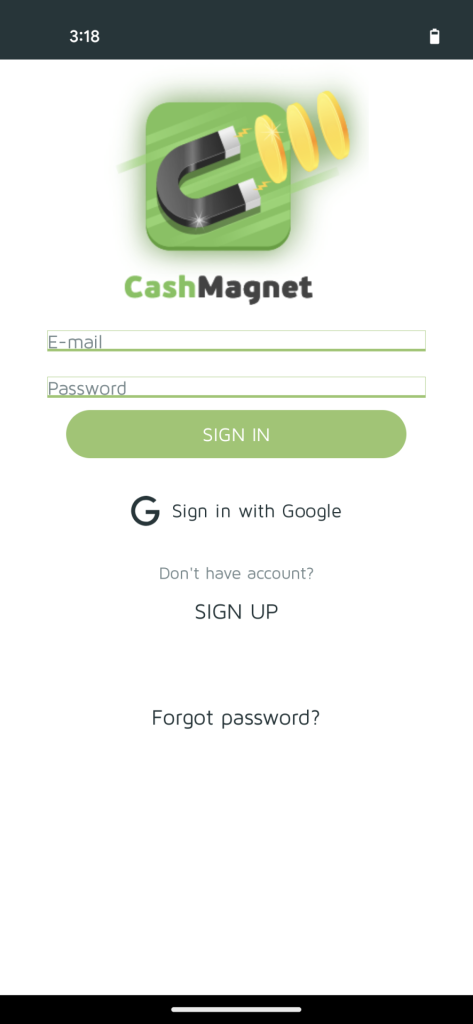
Determine 8a. LetterLink login web page after working the app for the primary time.
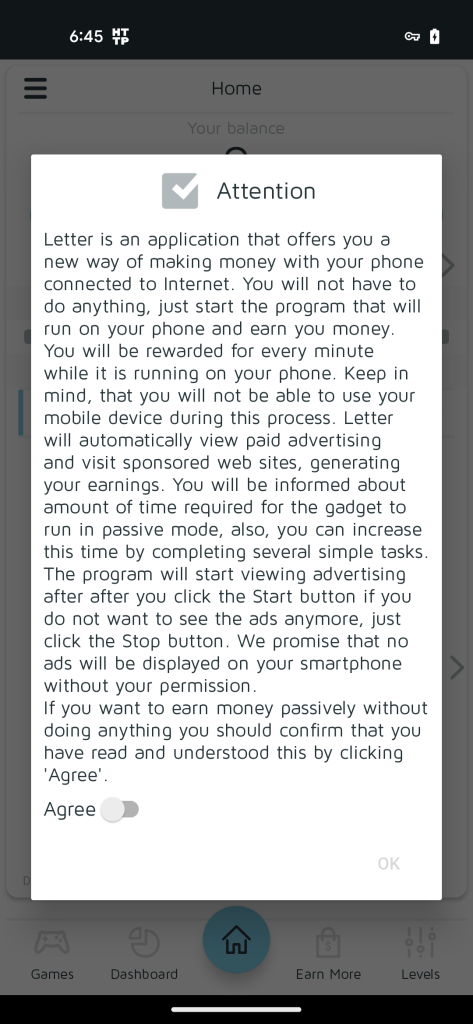
Determine 8b. LetterLink settlement for Money Magnet
Initially printed in 2019 on Google Play, “Money Magnet” (com.uicashmagnet) was described as a passive revenue utility providing customers to earn as much as $30 USD per thirty days working automated advertisements. Because it was eliminated by Google the authors then infiltrated LetterLink and extra just lately “Dots: One Line Connector” (com.orlovst.dots) that are hidden variations of the identical ad-fraud scheme.

Determine 9. LetterLink Icon that hides Money Magnet
“LetterLink” performs a number of Xamalicious actions because it incorporates the “core.dll” library, it connects to the identical C2 server, and it makes use of the identical hardcoded non-public RSA certificates to construct the JWE encrypted tokens which offer a non-repudiation proof that the builders of Money Magnet are behind Xamalicious.
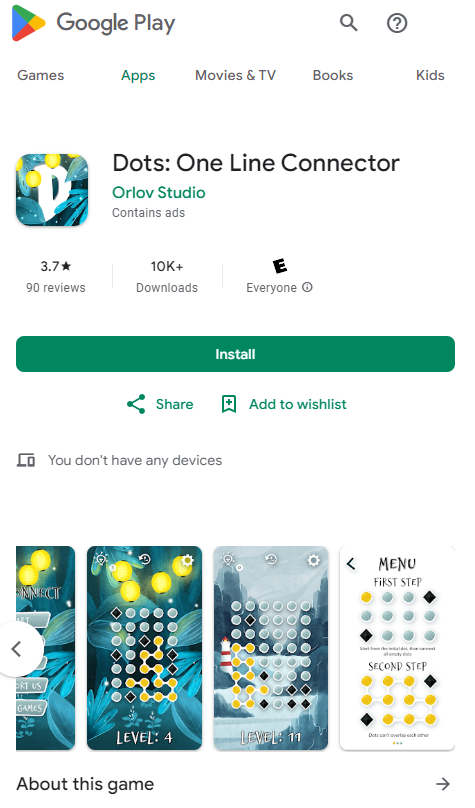
Determine 10. Money Magnet infiltrated the app as a Sport, accessible till the tip of 2023
“Dots: One Line Connector” app just isn’t a sport, the screenshot printed by Google Play doesn’t correspond to the applying conduct as a result of as soon as it’s began it simply asks for authentication credentials with none brand or reference to Money Magnet. “Dots” doesn’t comprise the identical DLLs as its predecessor, nonetheless the communication with the C2 is analogous utilizing the identical RSA key parameters.
Affected Customers
Based mostly on our telemetry we noticed that extra affected customers are within the American continent with essentially the most exercise within the USA, Brazil, and Argentina. In Europe, purchasers additionally reported the an infection, particularly within the UK, Spain, and Germany.
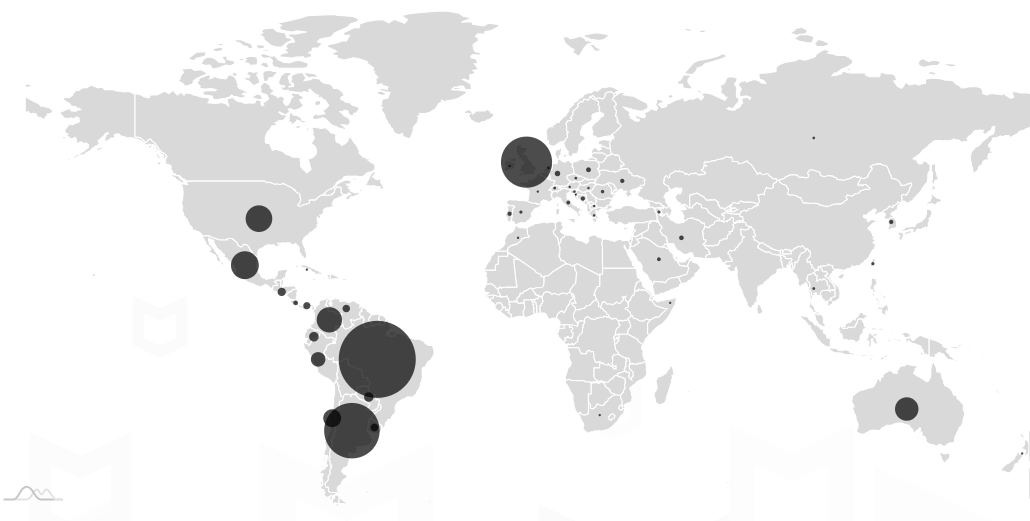
Determine 8. McAfee detections Android/Xamalicious all over the world
Conclusion
Android purposes written in non-java code with frameworks equivalent to Flutter, react native and Xamarin can present a further layer of obfuscation to malware authors that deliberately choose these instruments to keep away from detection and attempt to keep underneath the radar of safety distributors and maintain their presence on apps markets.
Keep away from utilizing apps that require accessibility providers except there’s a real want to be used. If a brand new app tries to persuade you to activate accessibility providers claiming that it’s required and not using a actual and affordable purpose and requesting to disregard the operative system warning, then it’s a pink flag.
The second stage payload may take management of the machine as a result of accessibility permissions are granted so some other permission or motion can then be carried out by the malware if these directions are supplied within the injected code.
As a result of it’s troublesome for customers to actively cope with all these threats, we strongly advocate that customers set up safety software program on their gadgets and all the time maintain updated. Through the use of McAfee Cellular Safety merchandise, customers can additional safeguard their gadgets and mitigate the dangers linked with these sorts of malware, offering a safer and safer expertise.
Android/Xamalicious Samples Distributed on Google Play:
| Package deal Identify | App Identify | Installs |
| com.anomenforyou.essentialhoroscope | Important Horoscope for Android | 100,000 |
| com.littleray.skineditorforpeminecraft | 3D Pores and skin Editor for PE Minecraft | 100,000 |
| com.vyblystudio.dotslinkpuzzles | Brand Maker Professional | 100,000 |
| com.autoclickrepeater.free | Auto Click on Repeater | 10,000 |
| com.lakhinstudio.counteasycaloriecalculator | Rely Straightforward Calorie Calculator | 10,000 |
| com.muranogames.easyworkoutsathome | Sound Quantity Extender | 5,000 |
| com.regaliusgames.llinkgame | LetterLink | 1,000 |
| com.Ushak.NPHOROSCOPENUMBER | NUMEROLOGY: PERSONAL HOROSCOPE &NUMBER PREDICTIONS | 1,000 |
| com.browgames.stepkeepereasymeter | Step Keeper: Straightforward Pedometer | 500 |
| com.shvetsStudio.trackYourSleep | Observe Your Sleep | 500 |
| com.devapps.soundvolumebooster | Sound Quantity Booster | 100 |
| com.Osinko.HoroscopeTaro | Astrological Navigator: Day by day Horoscope & Tarot | 100 |
| com.Potap64.universalcalculator | Common Calculator | 100 |
Indicator of compromise
| SHA256 | Package deal Identify |
| 63cb930ab83afe80d40ba620a0f2ed5e8a55cceec23bdad919bf9dfa3d8c6e5b | com.android.accessibility.service |
| 7149acb072fe3dcf4dcc6524be68bd76a9a2896e125ff2dddefb32a4357f47f6 | com.android.accessibility.service |
| a5de2dc4e6005e75450a0df0ea83816996092261f7dac30b5cf909bf6daaced0 | com.android.accessibility.service |
| 22803693c21ee17667d764dd226177160bfc2a5d315e66dc355b7366b01df89b | com.android.callllogbacup |
| efbb63f9fa17802f3f9b3a0f4236df268787e3d8b7d2409d1584d316dabc0cf9 | com.android.dreammusic |
| e801844333031b7fd4bd7bb56d9fb095f0d89eb89d5a3cc594a4bed24f837351 | com.android.statementsandservices |
| 6316edebe5995fc3e2715a44b78dcb2ec4f0409234851ee5dbb20c0fb60d1bf0 | com.android.tvresources |
| d3833f608e476ed24382bf3991cec503ebc7124481758bdb5e46390b367c1210 | com.android.ui.clock |
| 5fffb10487e718634924552b46e717bbcbb6a4f9b1fed02483a6517f9acd2f61 | com.android.ui.clock |
| 81a9a6c86b5343a7170ae5abd15f9d2370c8282a4ed54d8d28a3e1ab7c8ae88e | com.android.ui.clock |
| ac9bb11cf71b11d3d50620660b56f1612e10e4ee9f7fc5637c0c281a688ef978 | com.android.venting |
| 9c646516dd189cab1b6ced59bf98ade42e19c56fc075e42b85d597449bc9708b | com.android.model.shared |
| a4e7279daf2261d74e108be9ea46373777adb209de06d229cee1f77f7196bfdf | com.android.model.shared |
| 177ff9e281f96bf08ff9724e0c92cecc7538692cadc217cc2770c668b451f2dc | com.android.model.shared |
| 488942923780887114471dd0114ffb144deb8054773351b2b2aac3c974c569d8 | com.android.wall.lifetick |
| dfdca848aecb3439b8c93fd83f1fd4036fc671e3a2dcae9875b4648fd26f1d63 | com.anomenforyou.essentialhoroscope |
| e7ffcf1db4fb13b5cb1e9939b3a966c4a5a894f7b1c1978ce6235886776c961e | com.autoclickrepeater.free |
| 8927ff14529f03cbb2ebf617c298f291c2d69be44a8efa4e0406dea16e53e6f9 | com.autoclickrepeater.free |
| 117fded1dc51eff3788f1a3ec2b941058ce32760acf61a35152be6307f6e2052 | com.browgames.stepkeepereasymeter |
| 28a4ae5c699a7d96e963ca5ceec304aa9c4e55bc661e16c194bdba9a8ad847b7 | com.devapps.soundvolumebooster |
| b0b9a8e9ec3d0857b70464617c09ffffce55671b227a9fdbb178be3dbfebe8ed | com.kolomia.mineskineditor |
| 899b0f186c20fdbfe445b4722f4741a5481cd3cbcb44e107b8e01367cccfdda3 | com.lakhinstudio.counteasycaloriecalculator |
| e52b65fdcb77ed4f5989a69d57f1f53ead58af43fa4623021a12bc11cebe29ce | com.lakhinstudio.counteasycaloriecalculator |
| e694f9f7289677adaf2c2e93ba0ac24ae38ab9879a34b86c613dd3c60a56992d | com.littleray.skineditorforpeminecraft |
| 19ffe895b0d1be65847e01d0e3064805732c2867ce485dfccc604432faadc443 | com.muranogames.easyworkoutsathome |
| 6a3455ff881338e9337a75c9f2857c33814b7eb4060c06c72839b641b347ed36 | com.Osinko.HoroscopeTaro |
| e6668c32b04d48209d5c71ea96cb45a9641e87fb075c8a7697a0ae28929913a6 | com.Potap64.universalcalculator |
| 6953ba04233f5cf15ab538ae191a66cb36e9e0753fcaeeb388e3c03260a64483 | com.regaliusgames.llinkgame |
| f52917321b1010c0b145f699531947c84b26d63e91a5a67bf5131ba8904e1326 | com.shvetsstudio.newmapsforminecraftpe |
| cb8d4ae27b64c56831a4e9bb5f1d53a3a72eaea369ab7b40851009ed577d2b14 | com.shvetsStudio.trackYourSleep |
| 01c56911c7843098777ec375bb5b0029379b0457a9675f149f339b7db823e996 | com.shvetsStudio.trackYourSleep |
| f42e79c4dc6b1573731610a1135cb0a71152e869c598215f0db09958f2d761f5 | com.skladainc.phonedetectiveclaptofind |
| e55408ef4f10715e7a521e95df038114a75f865f5b2ac3c1dcfee2261724b5df | com.skladainc.phonedetectiveclaptofind |
| cc439631c09763003b92b80bbea2ff0f5d764694575ed7a9be155fbc420753db | com.skladainc.phonedetectiveclaptofind |
| 3201785a7de8e37e5d12e8499377cfa3a5b0fead6667e6d9079d8e99304ce815 | com.turovskyi.magicofnumbers |
| acb5de2ed2c064e46f8d42ee82feabe380364a6ef0fbfeb73cf01ffc5e0ded6b | com.Ushak.NPHOROSCOPENUMBER |
| 9b4dc1e80a4f4c798d0d87a52f52e28700b5b38b38a532994f70830f24f867ba | com.Ushak.NPHOROSCOPENUMBER |
| 1bfc02c985478b21c6713311ca9108f6c432052ea568458c8bd7582f0a825a48 | com.vyblystudio.dotslinkpuzzles |
