
A complicated cross-platform malware platform named StripedFly flew beneath the radar of cybersecurity researchers for 5 years, infecting over 1,000,000 Home windows and Linux methods throughout that point.
Kaspersky found the true nature of the malicious framework final yr, discovering proof of its exercise beginning in 2017, with the malware wrongly labeled as only a Monero cryptocurrency miner.
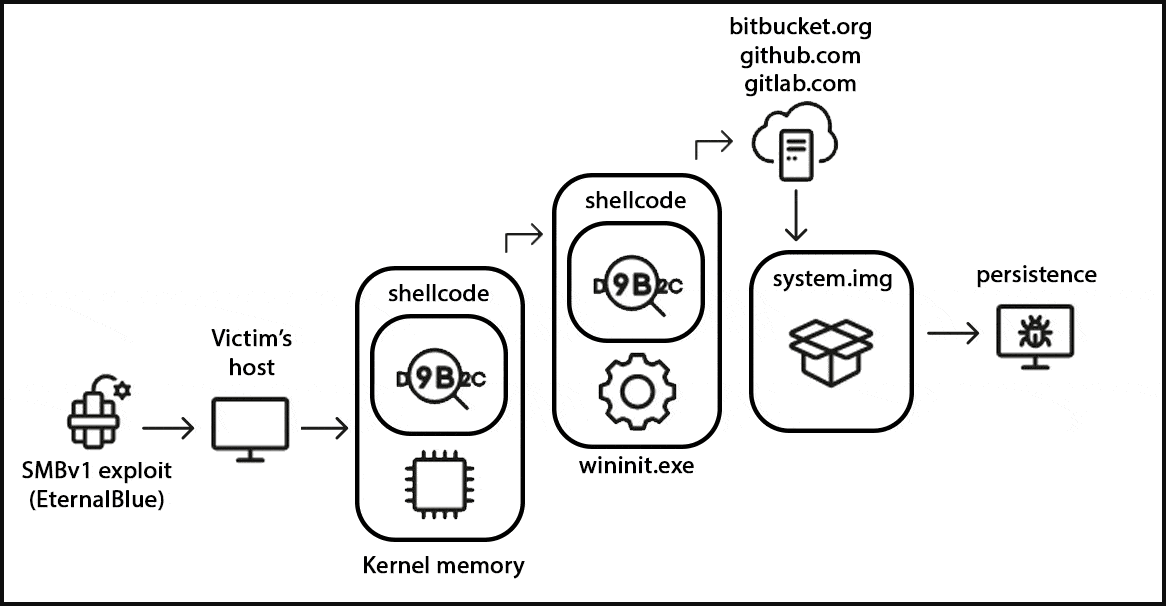
The analysts describe StripedFly as nothing wanting spectacular, that includes subtle TOR-based visitors concealing mechanisms, automated updating from trusted platforms, worm-like spreading capabilities, and a customized EternalBlue SMBv1 exploit created earlier than the general public disclosure of the flaw.
Whereas it is unclear if this malware framework was utilized for income technology or cyber espionage, Kaspersky says its sophistication signifies that that is an APT (superior persistent risk) malware.
Based mostly on the compiler timestamp for the malware, the earliest identified model of StripedFly that includes an EternalBlue exploit dates April 2016, whereas the public leak by the Shadow Brokers group occurred in August 2016.
StripedFly in over 1,000,000 methods
The StripedFly malware framework was first found after Kaspersky discovered the platform’s shellcode injected within the WININIT.EXE course of, a legit Home windows OS course of that handles the initialization of varied subsystems.
After investigating the injected code, they decided it downloads and executes further recordsdata, similar to PowerShell scripts, from legit internet hosting providers like Bitbucket, GitHub, and GitLab, together with PowerShell scripts.
Additional investigation confirmed that contaminated gadgets had been seemingly first breached utilizing a customized EternalBlue SMBv1 exploit that focused internet-exposed computer systems.
The ultimate StripedFly payload (system.img) includes a customized light-weight TOR community shopper to guard its community communications from interception, the power to disable the SMBv1 protocol, and unfold to different Home windows and Linux gadgets on the community utilizing SSH and EternalBlue.
The malware’s command and management (C2) server is on the TOR community, and communication with it includes frequent beacon messages containing the sufferer’s distinctive ID.
For persistence on Home windows methods, StripedFly adjusts its conduct based mostly on the extent of privileges it runs on and the presence of PowerShell.
With out PowerShell, it generates a hidden file within the %APPDATA% listing. In circumstances the place PowerShell is on the market, it executes scripts for creating scheduled duties or modifying Home windows Registry keys.
On Linux, the malware assumes the identify ‘sd-pam‘. It achieves persistence utilizing systemd providers, an autostarting .desktop file, or by modifying numerous profile and startup recordsdata, similar to /and many others/rc*, profile, bashrc, or inittab recordsdata.
The Bitbucket repository delivering the ultimate stage payload on Home windows methods signifies that between April 2023 and September 2023, there have been practically 60,000 system infections.
It’s estimated that StripedFly has contaminated not less than 220,000 Home windows methods since February 2022, however stats from earlier than that date are unavailable, and the repository was created in 2018.
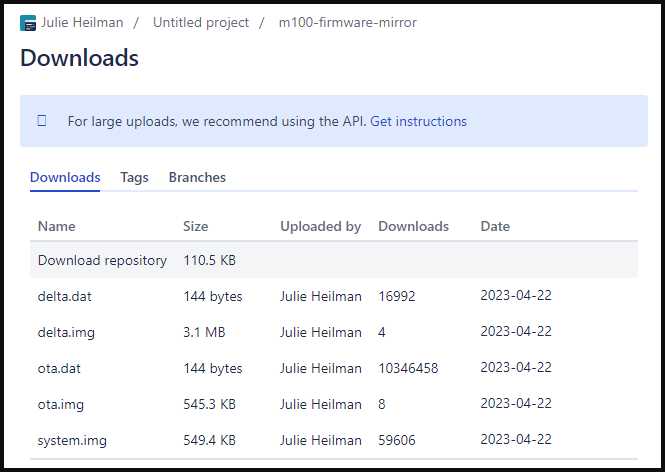
Nevertheless, Kaspersky estimates that over 1 million gadgets had been contaminated by the StripedFly framework.
Malware modules
The malware operates as a monolithic binary executable with pluggable modules, giving it an operational versatility usually related to APT operations.
Here is a abstract of StripedFly’s modules from Kaspersky’s report:
- Configuration storage: Shops encrypted malware configuration.
- Improve/Uninstall: Manages updates or elimination based mostly on C2 server instructions.
- Reverse proxy: Permits distant actions on the sufferer’s community.
- Miscellaneous command handler: Executes assorted instructions like screenshot seize and shellcode execution.
- Credential harvester: Scans and collects delicate consumer knowledge like passwords and usernames.
- Repeatable duties: Carries out particular duties beneath sure circumstances, similar to microphone recording.
- Recon module: Sends detailed system data to the C2 server.
- SSH infector: Makes use of harvested SSH credentials to penetrate different methods.
- SMBv1 infector: Worms into different Home windows methods utilizing a customized EternalBlue exploit.
- Monero mining module: Mines Monero whereas camouflaged as a “chrome.exe” course of.
The presence of the Monero crypto miner is taken into account a diversion try, with the first aims of the risk actors being knowledge theft and system exploitation facilitated by the opposite modules.
“The malware payload encompasses a number of modules, enabling the actor to carry out as an APT, as a crypto miner, and whilst a ransomware group,” reads Kaspersky’s report.
“Notably, the Monero cryptocurrency mined by this module reached its peak worth at $542.33 on January 9, 2018, in comparison with its 2017 worth of round $10. As of 2023, it has maintained a worth of roughly $150.”
“Kaspersky specialists emphasize that the mining module is the first issue enabling the malware to evade detection for an prolonged interval.”
The researchers additionally recognized hyperlinks to the ransomware variant ThunderCrypt, which makes use of the identical C2 server at “ghtyqipha6mcwxiz[.]onion:1111.”
The ‘repeatable duties module’ additionally means that the unidentified attackers may very well be excited about income technology for some victims.
