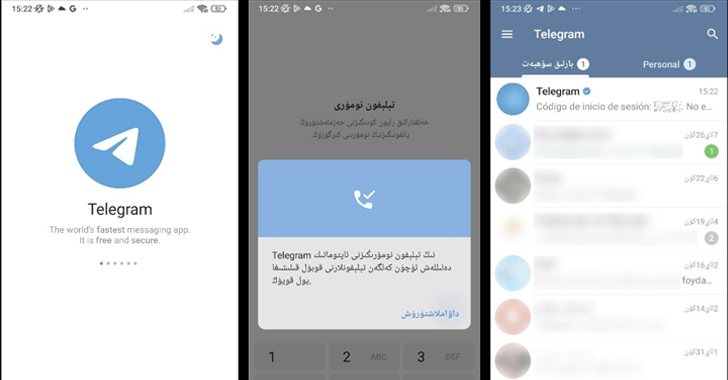
Spy ware masquerading as modified variations of Telegram have been noticed within the Google Play Retailer that is designed to reap delicate data from compromised Android gadgets.
In keeping with Kaspersky safety researcher Igor Golovin, the apps include nefarious options to seize and exfiltrate names, person IDs, contacts, telephone numbers, and chat messages to an actor-controlled server.
The exercise has been codenamed Evil Telegram by the Russian cybersecurity firm.
The apps have been collectively downloaded tens of millions of occasions earlier than they had been taken down by Google. Their particulars are as follows –
- 電報,紙飛機-TG繁體中文版 or 電報,小飛機-TG繁體中文版 (org.telegram.messenger.wab) – 10 million+ downloads
- TG繁體中文版-電報,紙飛機 (org.telegram.messenger.wab) – 50,000+ downloads
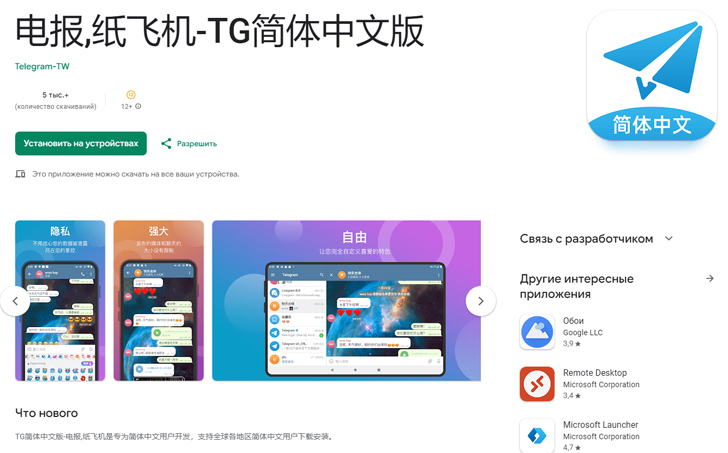
- 电报,纸飞机-TG简体中文版 (org.telegram.messenger.wob) – 50,000+ downloads
- 电报,纸飞机-TG简体中文版 (org.tgcn.messenger.wob) – 10,000+ downloads
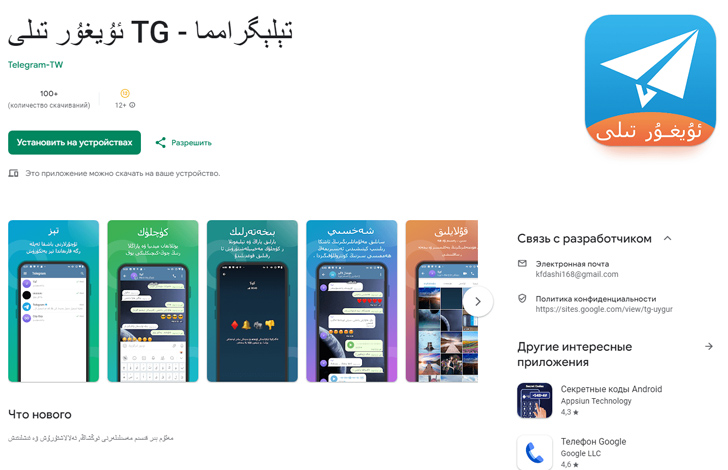
- ئۇيغۇر تىلى TG – تېلېگرامما (org.telegram.messenger.wcb) – 100+ downloads
The final app on the record interprets to “Telegram – TG Uyghur,” indicating a transparent try to focus on the Uyghur group.
It is value noting that the bundle identify related to the Play Retailer model of Telegram is “org.telegram.messenger,” whereas the bundle identify for the APK file immediately downloaded from Telegram’s web site is “org.telegram.messenger.net.”
Using “wab,” “wcb,” and “wob” for the malicious bundle names, due to this fact, highlights the menace actor’s reliance on typosquatting methods to be able to go off because the reputable Telegram app and slip below the radar.
Manner Too Weak: Uncovering the State of the Identification Assault Floor
Achieved MFA? PAM? Service account safety? Learn the way well-equipped your group really is in opposition to identification threats
“At first look, these apps seem like full-fledged Telegram clones with a localized interface,” the corporate mentioned. “Every part seems to be and works virtually the identical as the true factor. [But] there’s a small distinction that escaped the eye of the Google Play moderators: the contaminated variations home a further module:”
The disclosure comes days after ESET revealed a BadBazaar malware marketing campaign concentrating on the official app market that leveraged a rogue model of Telegram to amass chat backups.
Comparable copycat Telegram and WhatsApp apps had been uncovered by the Slovak cybersecurity firm beforehand in March 2023 that got here fitted with clipper performance to intercept and modify pockets addresses in chat messages and redirect cryptocurrency transfers to attacker-owned wallets.