Researchers from 4 American universities have developed a brand new GPU side-channel assault that leverages information compression to leak delicate visible information from fashionable graphics playing cards when visiting net pages.
The researchers have demonstrated the effectiveness of this ‘GPU.zip‘ assault by performing cross-origin SVG filter pixel-stealing assaults by means of the Chrome browser.
The researchers disclosed the vulnerability to impacted video card producers in March 2023. Nonetheless, as of September 2023, no affected GPU distributors (AMD, Apple, Arm, NVIDIA, Qualcomm) or Google (Chrome) have rolled out patches to handle the issue.
The brand new flaw is printed in a paper from researchers on the College of Texas at Austin, Carnegie Mellon College, College of Washington, and College of Illinois Urbana-Champaign and can seem within the forty fifth IEEE Symposium on Safety and Privateness.
Leaking by means of compression
Usually, information compression creates distinct data-dependent DRAM site visitors and cache utilization, which will be abused for leaking secrets and techniques, so software program turns off compression when dealing with delicate information.
The GPU.zip researchers clarify that each one fashionable graphic processor items, particularly built-in Intel and AMD chips, carry out software-visible information compression even when not explicitly requested.
Trendy GPUs observe this dangerous follow as an optimization technique, because it helps save on reminiscence bandwidth and enhance efficiency with out software program.
This compression is commonly undocumented and vendor-specific, and the researchers have discovered a technique to exploit it to leak visible information from GPUs.
Particularly, they demonstrated an assault that extracts particular person pixel information by means of an internet browser on varied gadgets and GPU architectures, as proven under.
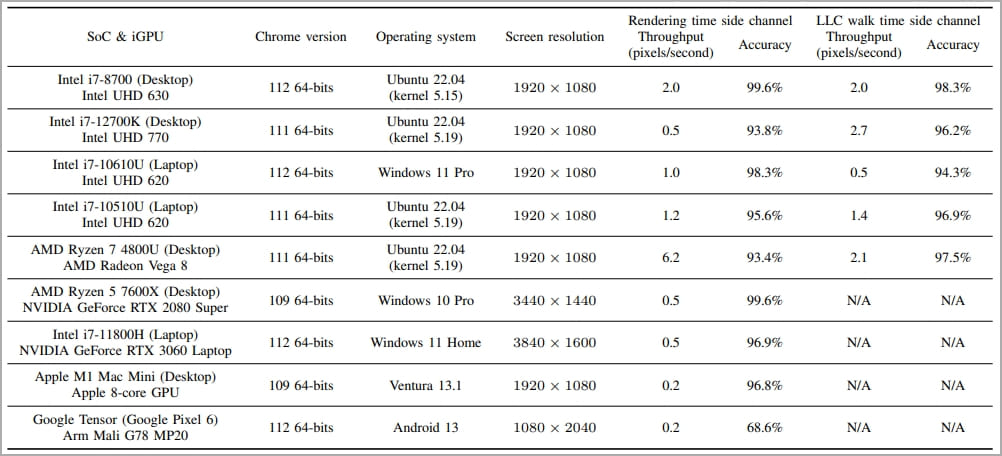
The proof-of-concept assault demonstrates stealing the username from a Wikipedia iframe, which is feasible inside half-hour on Ryzen and 215 minutes on Intel GPUs, at accuracies of 97% and 98.3%, respectively.
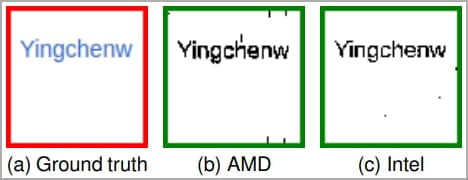
The iframe hosts a cross-origin webpage whose pixels are remoted and was binary, which means they’re transformed into two doable colours.
Subsequent, these pixels are enlarged, and a specialised SVG filter stack is utilized to create textures which might be both compressible or not. By measuring the time taken for the feel to render, the researchers can deduce the unique coloration/state of the goal pixel.
We now have not too long ago seen the appliance of SVG filters to induce data-dependent execution and using JavaScript to measure computation time and frequency to discern the pixel’s coloration on the “Scorching Pixels” assault.
Whereas Scorching Pixels exploits data-dependent computation instances on fashionable processors, GPU.zip hinges on undocumented GPU information compression to realize related outcomes.
GPU.zip severity
GPU.zip impacts nearly all main GPU producers, together with AMD, Apple, Arm, Intel, Qualcomm, and NVIDIA, however not all playing cards are equally affected.
The truth that not one of the impacted distributors have determined to repair the difficulty by optimizing their information compression strategy and limiting its operation to non-sensitive circumstances additional raises the danger.
Though GPU.zip probably impacts the overwhelming majority of laptops, smartphones, tablets, and desktop PCs worldwide, the speedy impression on customers is moderated by the complexity and time required to carry out the assault.
Additionally, web sites that deny cross-origin iframe embedding can’t be used for leaking consumer information by means of this or related side-channel assaults.
“Most delicate web sites already deny being embedded by cross-origin web sites. Because of this, they aren’t weak to the pixel stealing assault we mounted utilizing GPU.zip,” explains the researchers in a FAQ on the crew’s web site.
Lastly, the researchers observe that Firefox and Safari don’t meet all the standards wanted for GPU.zip to work, reminiscent of permitting cross-origin iframes to be loaded with cookies, rendering SVG filters on iframes, and delegating rendering duties to the GPU.

