
The UK Nationwide Cyber Safety Centre (NCSC) and Microsoft warn that the Russian state-backed actor “Callisto Group” (aka “Seaborgium” or “Star Blizzard”) is concentrating on organizations worldwide with spear-phishing campaigns used to steal account credentials and knowledge.
Callisto is a sophisticated persistent risk actor (APT) that has been energetic since late 2015 and has been attributed to Russia’s ‘Centre 18’ division of the Federal Safety Service (FSB)
Final 12 months, Microsoft’s risk analysts disrupted a gaggle’s assault concentrating on varied European NATO international locations by deactivating the risk actor’s Microsoft accounts used for surveillance and e-mail assortment. Microsoft additionally reported 69 domains related to their phishing campaigns to close down the websites.
In January this 12 months, NCSC warned about Callisto’s assaults, underlining the group’s open-source intelligence (OSINT) and social engineering expertise.
At present, the UK formally attributed assaults to Callisto that led to the leaking of UK-US commerce paperwork, the 2018 hack of the UK suppose tank Institute for Statecraft, and extra lately, the hack on StateCraft’s founder Christopher Donnelly.
As well as, the UK says the group is behind credential and knowledge theft assaults in opposition to parliamentarians from a number of political events, universities, journalists, the general public sector, non-government organizations, and different civil society organizations.
“The Overseas, Commonwealth and Improvement Workplace has additionally summoned the Russian Ambassador to precise the UK’s deep concern about Russia’s sustained makes an attempt to make use of cyber to intrude in political and democratic processes within the UK and past,” reads a press assertion from UK.
Callisto’s newest ways
In a bulletin printed at this time, the UK’s NCSC says Callisto stays targeted on launching spear-phishing assaults concentrating on the nation’s governmental organizations, suppose tanks, politicians, defense-industrial models, and varied NGOs.
“This advisory raises consciousness of the spear-phishing strategies Star Blizzard makes use of to focus on people and organisations. This exercise is continuous by means of 2023,” warns the NCSC.
The attackers supply key data from social media platforms like LinkedIn after which strategy their targets by emailing private addresses which are much less prone to be monitored by enterprise safety software program.
After constructing rapport with the goal over time, Callisto sends a malicious hyperlink embedded in a PDF doc hosted on Google Drive or OneDrive, which takes the goal to a phishing website.
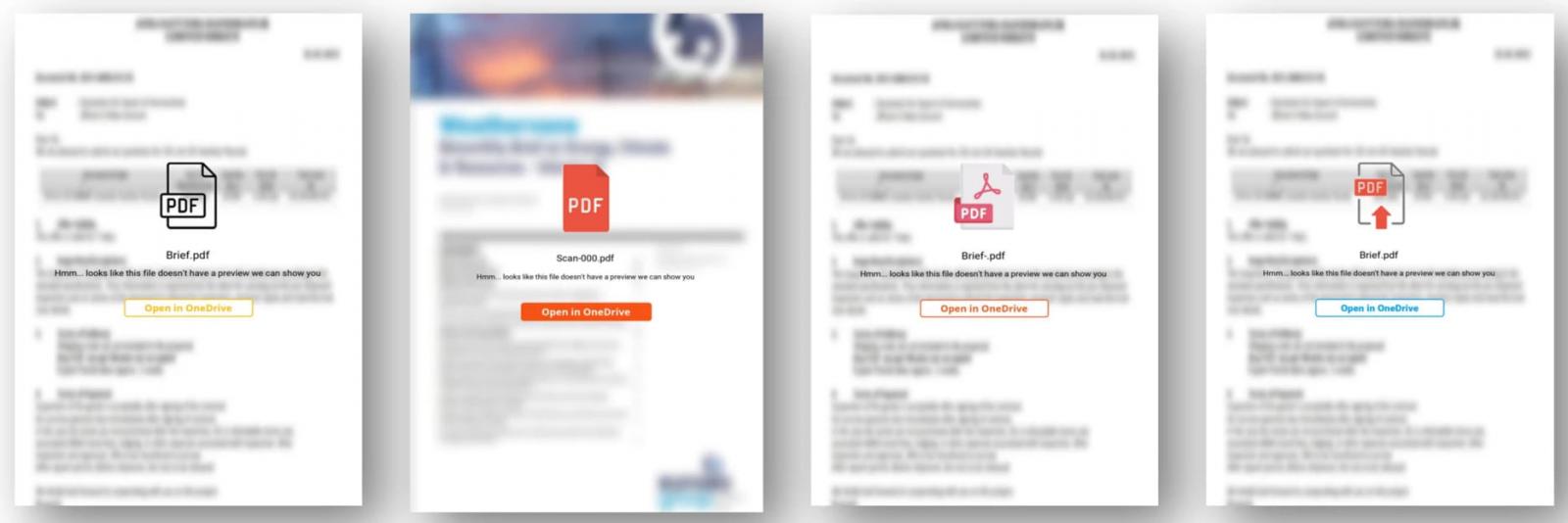
The phishing websites, hosted on illegitimate domains, goal Microsoft, Yahoo, and different emailing platforms and are sometimes protected by a CAPTCHA to filter out bots and provides a way of additional legitimacy.
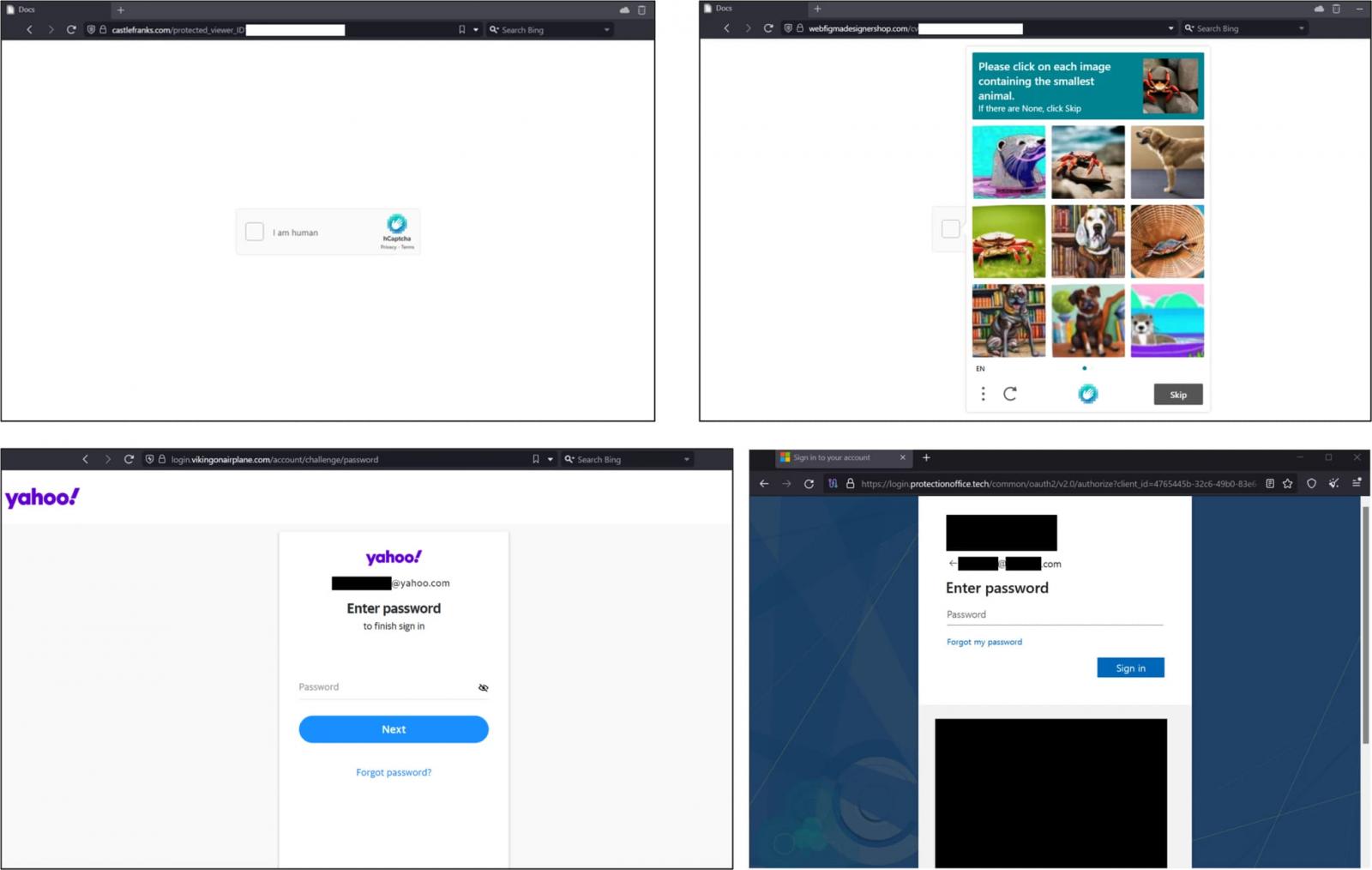
The phishing operation is backed by the open-source EvilGinx proxy assault framework that steals each consumer credentials and session cookies. This enables Callisto to bypass two-factor authentication when logging in with the stolen credentials.
Subsequent, the attackers use the stolen data to entry the sufferer’s e-mail account, analyze their inbox, and arrange forwarding guidelines that give them ongoing entry to the sufferer’s future communications.
At this closing stage, Callisto operators determine and have interaction in any lateral phishing alternatives, utilizing their entry to the sufferer’s inbox to hit different key targets.
Microsoft has additionally printed a report at this time highlighting the next new strategies, ways, and procedures adopted by the risk actor after April 2023:
- Use of server-side scripts that block automated scanning of the malicious infrastructure.
- Use of e-mail advertising and marketing platform providers like HubSpot and MailerLite to masks true e-mail addresses.
- Use of DNS supplier to masks the IP addresses of the VPS infrastructure.
- Use of area era algorithm (DGA) for higher evasion and resistance to blocks.
Defending in opposition to the Callisto risk and any spear-phishing assault requires a multi-faceted strategy, together with utilizing phishing-resistant MFA strategies like {hardware} keys, implementing strict conditional entry insurance policies, and monitoring for irregular exercise.
Sanctioned by the US and UK
A world legislation enforcement consisting of businesses from the UK, US, Australia, Canada, and New Zealand has recognized two members of the Callisto hacking group.
These are Aleksandrovich Peretuatko, believed to be an FBS Middle 18 intelligence officer, and Andrey Stanislavovich Korinets, aka “Alexey Doguzhiev.”
The 2 are thought-about instantly accountable for Callisto operations concentrating on a number of UK organizations, some leading to unauthorized entry and exfiltration of delicate knowledge.
As a part of at this time’s announcement, each the UK and the US have sanctioned the 2 members for trying to undermine the UK’s democratic course of.
“The UK has sanctioned two people for partaking in spear phishing operations with the intention to make use of data obtained to undermine UK democratic processes,” reads a press assertion from the US Division of the Treasury.
“The US, in help of and in solidarity with the UK, has additionally taken motion in opposition to the identical people, figuring out their connection to the FSB unit and its exercise that has focused US essential authorities networks.”
The US authorities’s Rewards for Justice program additionally provides a $10 million reward for data on Callisto’s group members and their actions.
