
The APT36 hacking group, aka ‘Clear Tribe,’ has been noticed utilizing no less than three Android apps that mimic YouTube to contaminate gadgets with their signature distant entry trojan (RAT), ‘CapraRAT.’
As soon as the malware is put in on a sufferer’s system, it might harvest knowledge, document audio and video, or entry delicate communication info, primarily working like a spyware and adware instrument.
APT36 is a Pakistan-aligned risk actor identified for utilizing malicious or laced Android apps to assault Indian protection and authorities entities, these coping with Kashmir area affairs, and human rights activists in Pakistan.
This newest marketing campaign was noticed by SentinelLabs, which warns folks and organizations linked to army or diplomacy in India and Pakistan to be very cautious of YouTube Android apps hosted on third-party websites.
Impersonating YouTube
The malicious APKs are distributed exterior Google Play, Android’s official app retailer, so the victims are almost certainly socially engineered to obtain and set up them.
The APKs have been uploaded to VirusTotal in April, July, and August 2023, with two of them being referred to as ‘YouTube’ and one ‘Piya Sharma’ related to the channel of a persona possible utilized in romance-based ways.
Throughout set up, the malware apps request quite a few dangerous permissions, a few of which the sufferer would possibly deal with with out suspicion for a media streaming app like YouTube.
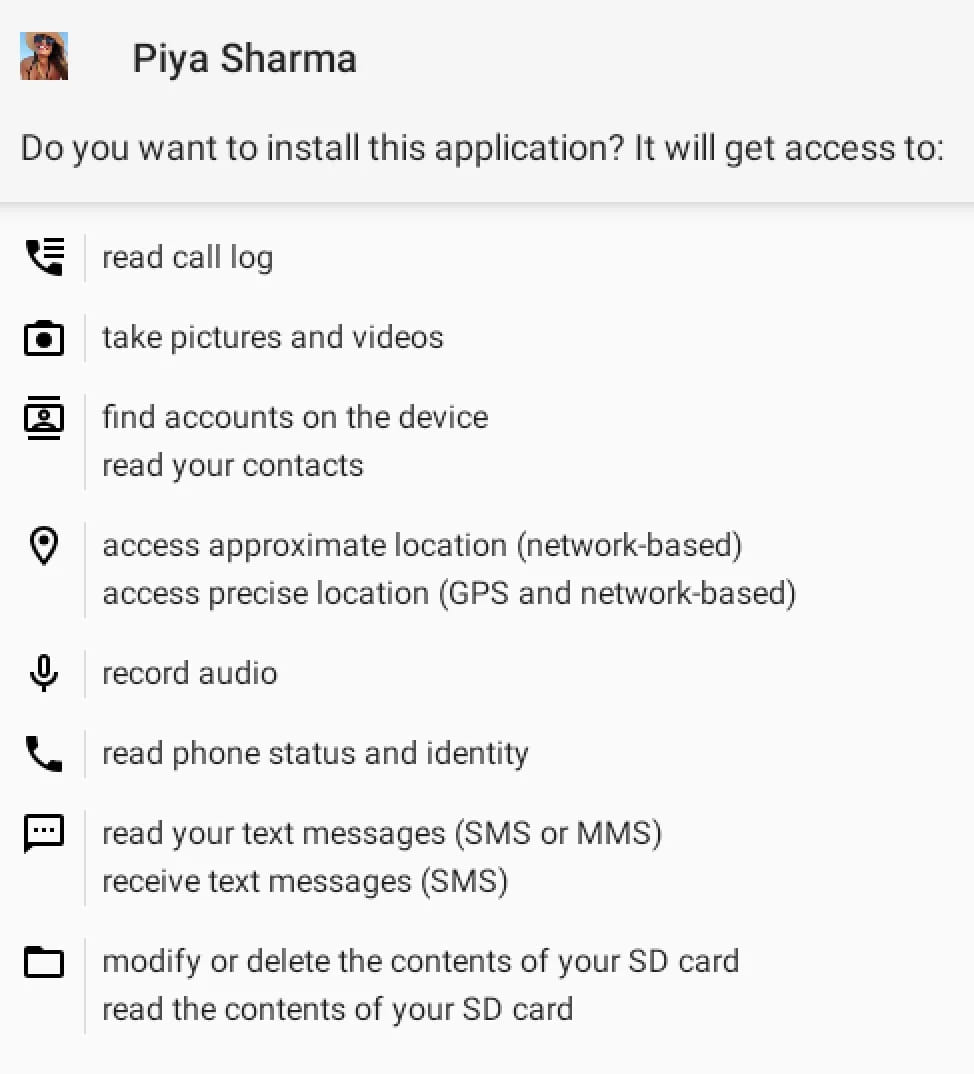
The interface of the malicious apps makes an attempt to mimic Google’s actual YouTube app, however it resembles an online browser moderately than the native app on account of utilizing WebView from throughout the trojanized app to load the service. Additionally, it misses a number of of the options obtainable on the precise platform.
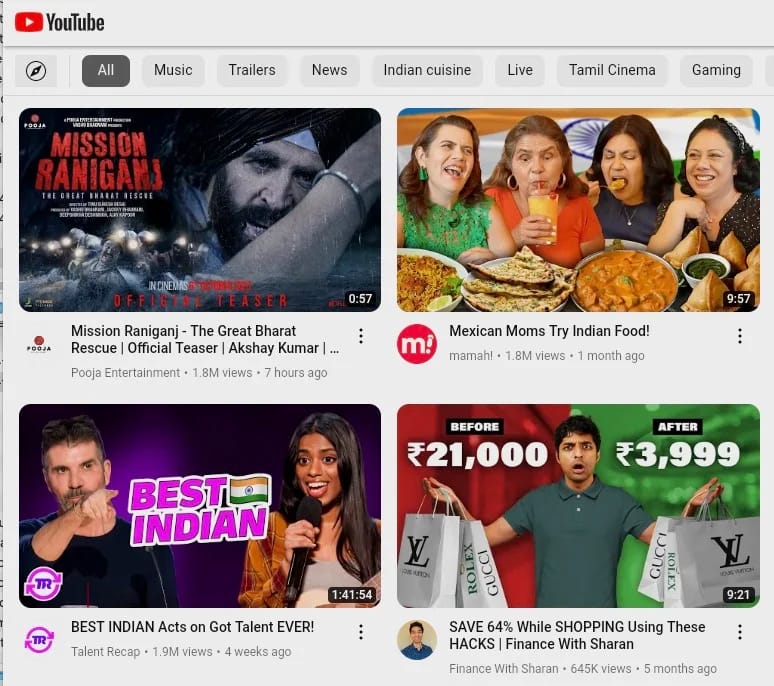
As soon as the CapraRAT is up and working on the system, it performs the next actions:
- Recording with the microphone, entrance & rear cameras
- Amassing SMS and multimedia message contents, name logs
- Sending SMS messages, blocking incoming SMS
- Initiating telephone calls
- Taking display captures
- Overriding system settings corresponding to GPS & Community
- Modifying recordsdata on the telephone’s filesystem
SentinelLabs experiences that the CapraRAT variants noticed within the latest marketing campaign function enhancements over beforehand analyzed samples, indicating steady growth.
Concerning the attribution, the C2 (command and management) server addresses CapraRAT communicates with are hardcoded within the app’s configuration file and have been related to previous Clear Tribe actions.
Some IP addresses retrieved by SentinelLabs are linked with different RAT campaigns, although the precise relationship between the risk actors and people stays unclear.
In conclusion, Clear Tribe continues its cyber espionage actions in India and Pakistan, utilizing its signature Android RAT, now disguised as YouTube, demonstrating evolution and adaptableness.
SentinelLabs observes that whereas the risk group’s weak operational safety makes their campaigns and instruments simply identifiable, their steady rollout of recent apps offers them an elusive edge, persistently reaching new potential victims.
