

In its 2023 Mid-Yr Cyber Safety Report, Test Level Software program spotlighted quite a few exploits up to now this 12 months, together with novel makes use of of synthetic intelligence and an old-school assault vector: USB drives. Cybercriminals and nation-state actors see these units as one of the best ways to contaminate air gapped, segmented and guarded networks, in response to Test Level.
The report’s authors famous the Raspberry Robin worm was one of many widespread malware variants distributed by means of USB drives through “autorun.inf” recordsdata or clickable LNK recordsdata. Test Level additionally reported that state-aligned risk actors are even launching 10-year-old infections resembling ANDROMEDA through USB drives.
China-related espionage risk actor Camaro Dragon, for instance, used USB drives as a vector to contaminate organizations all around the world, in response to the report’s authors. As well as, the safety researchers identified that Russian-aligned group Gamaredon used USB drive-delivered Shuckworm to focus on Ukrainian navy and related people.
I spoke with Pete Nicoletti, international chief data safety officer for the Americas at Test Level Software program, about another top-line findings from the report. Nicoletti, who has greater than 30 years within the area, mentioned AI is a sport changer, and that out of Test Level Software program’s 70-plus engines, AI and machine studying drives 40 of them. The next transcript of my interview with Nicoletti has been edited for size and readability.
Leap to:
Discovered an orphan USB? Higher to depart or not it’s
Karl Greenberg: I used to be shocked by the report’s particulars round bodily USB drivers as a viable assault vector. Actually? As we speak?

Pete Nicoletti: As a former penetration tester, I believed the times of USB drivers… USB units getting used to hack had been going to go away, however we’ve seen an enormous uptick in firms falling for a USB drive insertion. After I used to attempt to break into firms, we used a watering gap assault: You go to the bar the place the workers go, you go to the workplace constructing or rest room the place the workers go, and also you drop a few USBs (it was once CDs, with labels saying “third quarter layoffs” and folks would seize them). We’re seeing the identical factor occurring with flash drives, and that is dramatic.
Karl Greenberg: Hackers are bodily leaving USB drives round?
Pete Nicoletti: Sure, and this tactic is infecting organizations. Earlier than COVID, we used to have higher insurance policies in opposition to utilizing USBs in corporate-owned laptops, as a result of that laptop computer can be inspected. Submit COVID, it’s BYO machine, and there are fewer company protections, in order that’s partly why we’re seeing a spike. Additionally, we’re seeing an uptick in hacktivism with politically motivated teams launching assaults and synthetic intelligence misuse resembling utilizing AI to craft emails. We simply noticed the discharge of an AI-based keystroke monitoring instrument that has about 85% to 95% accuracy in understanding the keystroke simply by sound.
Dangerous bots: AI for spam, spearphishing and malware
Karl Greenberg: How vital are AI instruments at the moment for cybersecurity practitioners, and what do you see as key methods hackers are utilizing it?
Pete Nicoletti: For those who don’t have synthetic intelligence to battle synthetic intelligence, you’re going to be a statistic, as a result of AI is decreasing the bar for the attackers. Only for spam, for example, there are much more (non-English talking) folks now who can create emails utilizing actually good English.
Principally, hackers are utilizing AI in a minimum of two methods: They’re utilizing AI to jot down snippets of code moderately than full-blown ransomware applications for, say, a zero day for a given widespread vulnerability and publicity; they’re utilizing it, for instance, to jot down a keyboard stroke collector. And they’re utilizing AI to automate spam creation utilizing hacked information to generate content material. These may, for instance, be tied to hacked non-public details about a affected person’s data which will have been half of a big breach; hackers are utilizing such information to create personalised emails: “You had been simply in for such and such a process, and also you owe an extra $200 on the invoice.”
SEE: Test Level publicizes raft of 2023 AI options (TechRepublic)
AI for the protection: Discovering spam, insurance coverage evaluations, penetration checks
Karl Greenberg: How do you stop or defend in opposition to these types of AI-powered, spearphishing campaigns?
Pete Nicoletti: All of our large provider clients use Avanan, an AI-powered (electronic mail safety) instrument we acquired two years in the past. With it, we’re capable of uncover new sorts of challenging-to-find spam — and spam remains to be 89% the vector of alternative for profitable assaults.
SEE: Test Level’s Avanan spotlights how enterprise electronic mail compromise assaults emulate authentic net providers to lure clicks (TechRepublic)
Karl Greenberg: Moreover use for lowering analyst workloads, the place else are you seeing AI getting used extra at the moment?
Pete Nicoletti: We’re seeing folks use ChatGPT and different massive language fashions to evaluate their cyber insurance coverage applications. We’re seeing folks use it to jot down up penetration checks to present them extra relevance and a deeper understanding of sure points. For those who’re not utilizing synthetic intelligence, you’re not going to be aggressive.
Schooling sector is the highest goal
Karl Greenberg: What are the opposite top-line findings from the primary half of the 12 months?
Pete Nicoletti: We’re seeing the training sector being the primary assault vertical; we’ve seen an enormous spike on this.
Karl Greenberg: Why?
Pete Nicoletti: A few causes, together with faculties transitioning to outsourced IT and utilizing extra on-line training instruments. Additionally, academic establishments don’t have the budgets the business sector has. We now have seen a minimum of one college exit of enterprise for the primary time (Lincoln Faculty in Could 2022) due to ransomware calls for. Globally, training and analysis are nonetheless the highest targets for assaults (Determine A).
Determine A
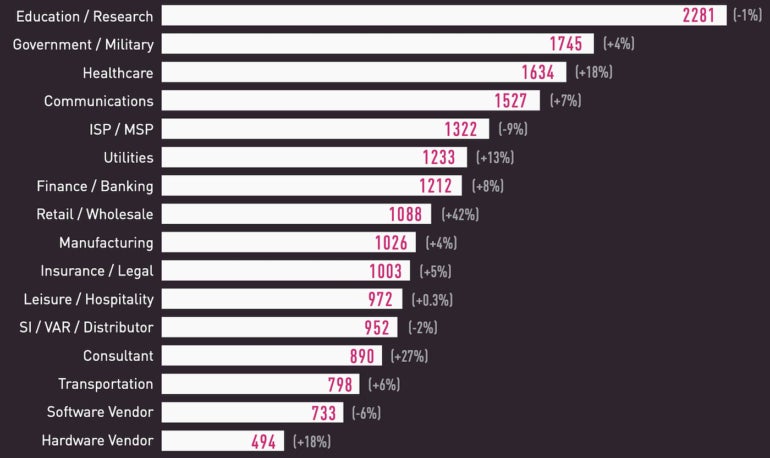
Microsoft: An enormous home with many doorways and “Home windows”
Karl Greenberg: I observed the variety of vulnerabilities in generally used company software program may be very excessive; Microsoft is primary. Why does Microsoft have so many CVEs?
Pete Nicoletti: Somebody famously mentioned they rob banks as a result of that’s the place the cash is. For those who’re a hacker, you wish to goal Microsoft as a result of it’s so ubiquitous. It’s all over the place — an utility growing firm and an working system. It’s utilized by everybody. So when you’re going to discover a zero day, whether or not you’re a state-sponsored hacking group or only a 16-year-old within the basement carrying a hoodie, you’re going to be focusing on Microsoft.
The opposite factor lots of people don’t discuss: while you flip the knob as an organization to push merchandise out the door, as a result of firms can take on a regular basis on the planet to develop one thing and check it, however firms wish to launch merchandise now, not tomorrow. And once they flip the knob to be aggressive and achieve market share, that is the unstated sort of danger of improvement that will get you in hassle.
Karl Greenberg: Which is why AI instruments in DevOps are crucial.
Pete Nicoletti: Firms with quick improvement retailers are selecting up these instruments to extend safety of their improvement pipeline, containers and Kubernetes, and it’s a lot cheaper to repair within the improvement pipeline moderately than within the check or manufacturing surroundings. So firms are lastly figuring that out.
Sound and imaginative and prescient: The following AI threats
Karl Greenberg: What about different makes use of of AI for threats past textual content and code era?
Pete Nicoletti: We now have at all times been coping with enterprise electronic mail compromise; nicely, now it’s going to be voice compromise and video compromise. It’s completely coming. We’re going to start out seeing much more photographs transformed to a video dialogue. We’ve seen voice compromises already, and each financial institution that’s utilizing voice affirmation and voice identification might be fooled now. So, if in case you have bank cards or banks that use this? Say goodbye. I wouldn’t allow that in any respect any extra.
