An affiliate of the BlackCat ransomware group, also called APLHV, is behind the assault that disrupted MGM Resorts’ operations, forcing the corporate to close down IT techniques.
In a press release right this moment, the BlackCat ransomware group claims that that they had infiltrated MGM’s infrastructure since Friday and encrypted greater than 100 ESXi hypervisors after the corporate took down the inner infrastructure.
The gang says that they exfiltrated knowledge from the community and preserve entry to a few of MGM’s infrastructure, threatening to deploy new assaults except an settlement to pay a ransom is reached.
Ransomware deployed, MGM knowledge stolen
Cybersecurity researcher vx-underground first broke the information that menace actors affiliated with the ALPHV ransomware operation allegedly breached MGM by a social engineering assault.
Whereas BleepingComputer couldn’t affirm if that was true, the BlackCat/ALPHV admin did affirm with BleepingComputer yesterday that certainly one of their “adverts” (affiliate) carried out the MGM assault, saying that it wasn’t the identical actor that hacked Western Digital in March.
Citing sources acquainted with the matter, studies on-line [1, 2] later mentioned that the menace actor that breached MGM Resorts is being tracked by cybersecurity corporations as Scattered Spider (Crowdstrike).
Different corporations use totally different names to trace the identical menace actor: 0ktapus (Group-IB), UNC3944 (Mandiant), and Scatter Swine (Okta).
In line with Bloomberg reporters, Scattered Spider has additionally breached the community of Caesars Leisure, who, in a U.S. Securities and Trade Fee on Thursday, offered a powerful trace at paying the attacker to keep away from a leak of buyer knowledge stolen within the assault. The ransom demand was allegedly $30 million.
Of their assertion right this moment, BlackCat says that MGM Resorts remained silent on the offered communication channel, indicating that the corporate has no intention to barter a ransom fee.
The hackers stress that the one motion they noticed from MGM was in response to the breach, disconnecting “each certainly one of their Okta Sync servers after studying that we had been lurking on their Okta Agent servers.”
The attacker claims they have been attempting to smell any passwords that they might not recuperate from the area controller hash dumps.
Regardless of shutting down the synchronization Okta servers, the hackers continued to be current on the community, BlackCat says of their assertion.
They claimed to nonetheless have tremendous administrator privileges on MGM’s Okta surroundings and World Administrator permissions to the corporate’s Azure tenant.
After seeing MGM taking this motion and with no intention from the corporate to have interaction in negotiations over the offered chat, the menace actor says that they deployed the ransomware assault.
“After ready a day, we efficiently launched ransomware assaults towards greater than 100 ESXi hypervisors of their surroundings on September eleventh after attempting to get in contact however failing. This was after they introduced in exterior corporations for help in containing the incident,” – BlackCat/ALPHV.
At this second, the hackers say that they have no idea what sort of information they stole from MGM however promise to extract related info and share it on-line except they attain an settlement with MGM.
To strain the corporate much more into paying, BlackCat threatened to make use of their present entry to MGM’s infrastructure to “perform further assaults.”
BleepingComputer was not capable of independently affirm BlackCat’s claims and MGM has not replied to our emails.
Who’s Scattered Spider
Scattered Spider is believed to be a bunch of menace actors who’re identified use a variety of social engineering assaults to breach company networks.
These assaults embody impersonating assist desk personel to trick customers into provide credentials, SIM swap assaults to take over the cellphone variety of a focused cell gadget, and MFA fatigue and phishing assaults to achieve entry to multi-factor authentication codes.
In contrast to most ransomware associates who’re from CIS international locations, researchers imagine that the hacking group consists of English-speaking youngsters and younger adults starting from 16-22 years of age.
Moreover, as a result of related ways, researchers imagine the group overlaps with the Lapsus$ hacking group, which had the same make-up for members and ways.
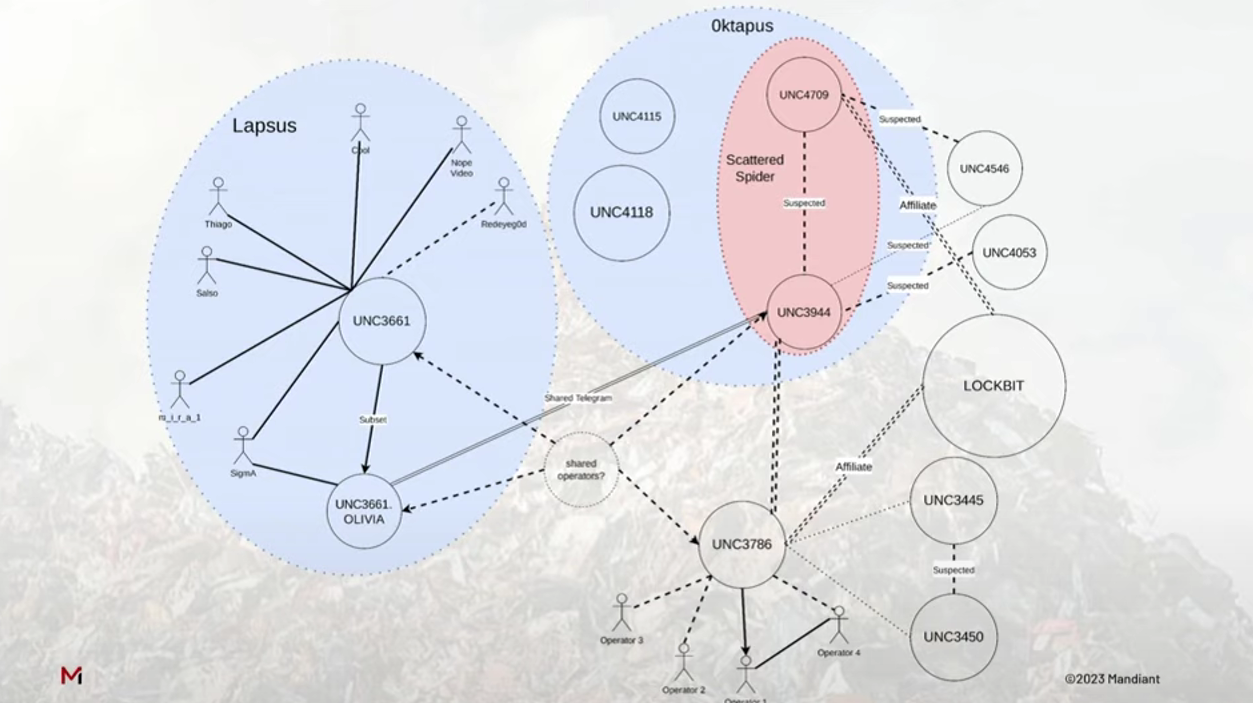
supply: Mandiant
A Scattered Spider marketing campaign known as ‘0ktapus‘ was used to focus on over 130 organizations to steal Okta id credentials and 2FA codes, with a few of these targets together with T-Cell, MetroPCS, Verizon Wi-fi, AT&T, Slack, Twitter, Binance, KuCoin, CoinBase, Microsoft, Epic Video games, Riot Video games, Evernote, AT&T, HubSpot, TTEC, and Finest Purchase.
As soon as the menace actors breach a community, they’ve a historical past of using Deliver Your Personal Susceptible Driver assaults to achieve elevated entry on a compromised gadget. This entry is then used to additional unfold laterally on the community whereas stealing knowledge and finally getting access to admin credentials.
As soon as they achieve entry to admin credentials, they will carry out additional assaults, comparable to hijacking single sign-on administration, destroying backups, and, extra lately, deploying the BlackCat/ALPHV ransomware to encrypt units.
Whereas the ransomware part is a comparatively new tactic of the hacking group, nearly all of their assaults contain extortion, the place they demand million-dollar ransoms in return for not publishing knowledge or to obtain an encryptor.

