
A Chinese language espionage-focused hacker tracked as ‘Earth Lusca’ was noticed concentrating on authorities businesses in a number of nations, utilizing a brand new Linux backdoor dubbed ‘SprySOCKS.’
Development Micro’s evaluation of the novel backdoor confirmed that it originates from the Trochilus open-source Home windows malware, with lots of its features ported to work on Linux methods.
Nonetheless, the malware seems to be a mix of a number of malware because the SprySOCKS’ command and management server (C2) communication protocol is much like RedLeaves, a Home windows backdoor. In distinction, the implementation of the interactive shell seems to have been derived from Derusbi, a Linux malware.
Earth Lusca assaults
Earth Lusca remained lively all through the primary half of the yr, concentrating on key authorities entities centered on overseas affairs, expertise, and telecommunications in Southeast Asia, Central Asia, the Balkans, and worldwide.
Development Micro stories seeing exploitation makes an attempt for a number of n-day unauthenticated distant code execution flaws dated between 2019 and 2022, impacting internet-exposed endpoints.
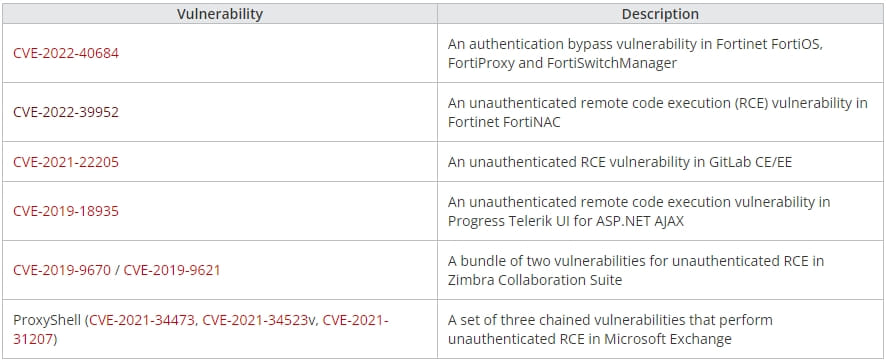
These flaws are exploited to drop Cobalt Strike beacons, which permit distant entry to the breached community. This entry is used to unfold laterally on the community whereas exfiltrating information, stealing account credentials, and deploying further payloads, like ShadowPad.
The risk actors additionally use the Cobalt Strike beacons to drop the SprySOCKS loader, a variant of the Linux ELF injector referred to as “mandibule,” which arrives on focused machines within the type of a file named ‘libmonitor.so.2.’
Development Micro’s researchers say the attackers tailored mandibule for his or her wants, however in a considerably rushed method, leaving debug messages and symbols behind.
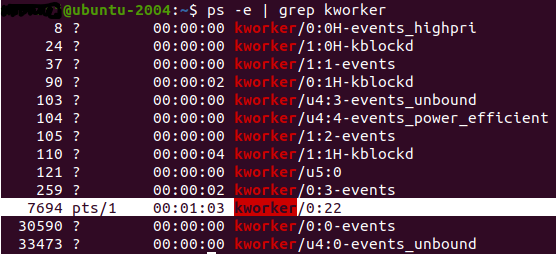
The loader runs below the title “kworker/0:22” to keep away from detection by resembling a Linux kernel employee thread, decrypts the second-stage payload (SprySOCKS), and establishes persistence on the contaminated pc.
SprySOCKS capabilities
The SprySOCKS backdoor makes use of a high-performance networking framework referred to as ‘HP-Socket’ for its operation, whereas its TCP communications with the C2 are AES-ECB encrypted.
The principle backdoor functionalities of this novel malware embrace:
- Amassing system data assortment (OS particulars, reminiscence, IP handle, group title, language, CPU),
- beginning an interactive shell that makes use of the PTY subsystem,
- itemizing community connections,
- managing SOCKS proxy configurations,
- and performing fundamental file operations (importing, downloading, itemizing, deleting, renaming, and creating directories.)
The malware additionally generates a shopper ID (sufferer quantity) utilizing the MAC handle of the primary listed community interface and a few CPU options after which converts it to a 28-byte hexadecimal string.
Development Micro stories having sampled two variations of SprySOCKS, v1.1 and v.1.3.6, indicating lively improvement of the malware.
The really useful precedence for organizations ought to be to use the out there safety updates on public-facing server merchandise, which, on this case, would forestall preliminary compromise from Earth Lusca.
