Domains ending in “.US” — the top-level area for the US — are among the many most prevalent in phishing scams, new analysis exhibits. That is noteworthy as a result of .US is overseen by the U.S. authorities, which is often the goal of phishing domains ending in .US. Additionally, .US domains are solely alleged to be out there to U.S. residents and to those that can show that they’ve a bodily presence in the US.
.US is the “nation code top-level area” or ccTLD of the US. Most international locations have their very own ccTLDs: .MX for Mexico, for instance, or .CA for Canada. However few different main international locations on the planet have anyplace close to as many phishing domains every year as .US.
That’s in response to The Interisle Consulting Group, which gathers phishing information from a number of trade sources and publishes an annual report on the most recent traits. Interisle’s latest examine examined six million phishing studies between Might 1, 2022 and April 30, 2023, and discovered 30,000 .US phishing domains.
.US is overseen by the Nationwide Telecommunications and Info Administration (NTIA), an government department company of the U.S. Division of Commerce. Nevertheless, NTIA presently contracts out the administration of the .US area to GoDaddy, by far the world’s largest area registrar.
Beneath NTIA laws, the administrator of the .US registry should take sure steps to confirm that their clients really reside in the US, or personal organizations primarily based within the U.S. However Interisle discovered that no matter GoDaddy was doing to handle that vetting course of wasn’t working.
“The .US ‘nexus’ requirement theoretically limits registrations to events with a nationwide connection, however .US had very excessive numbers of phishing domains,” Interisle wrote. “This means a attainable drawback with the administration or software of the nexus necessities.”
Dean Marks is emeritus government director for a bunch known as the Coalition for On-line Accountability, which has been important of the NTIA’s stewardship of .US. Marks says nearly all European Union member state ccTLDs that implement nexus restrictions even have massively decrease ranges of abuse resulting from their insurance policies and oversight.
“Even very massive ccTLDs, like .de for Germany — which has a far bigger market share of area title registrations than .US — have very low ranges of abuse, together with phishing and malware,” Marks advised KrebsOnSecurity. “In my opinion, this case with .US shouldn’t be acceptable to the U.S. authorities general, nor to the US public.”
Marks mentioned there are only a few phishing domains ever registered in different ccTLDs that additionally limit registrations to their residents, akin to .HU (Hungary), .NZ (New Zealand), and .FI (Finland), the place a connection to the nation, a proof of id, or proof of incorporation are required.
“Or .LK (Sri Lanka), the place the appropriate use coverage features a ‘lock and droop’ if domains are reported for suspicious exercise,” Marks mentioned. “These ccTLDs make a powerful case for validating area registrants within the curiosity of public security.”
Sadly, .US has been a cesspool of phishing exercise for a few years. Way back to 2018, Interisle discovered .US domains had been the worst on the planet for spam, botnet (assault infrastructure for DDOS and so forth.) and illicit or dangerous content material. Again then, .US was being operated by a distinct contractor.
In response to questions from KrebsOnSecurity, GoDaddy mentioned all .US registrants should certify that they meet the NTIA’s nexus necessities. However this seems to be little greater than an affirmative response that’s already pre-selected for all new registrants.
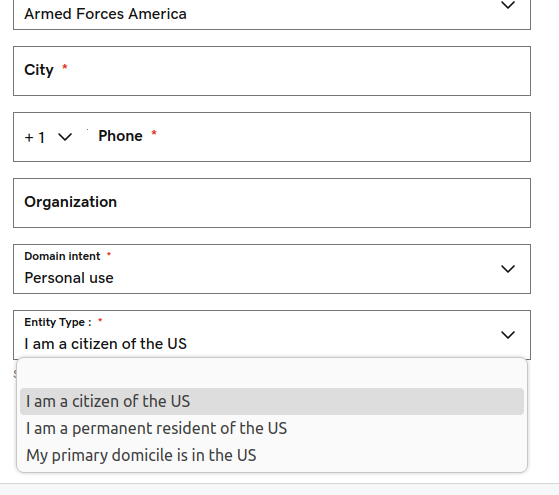
Making an attempt to register a .US area by way of GoDaddy, for instance, results in a U.S. Registration Info web page that auto-populates the nexus attestation area with the response, “I’m a citizen of the US.” Different choices embrace, “I’m a everlasting resident of the US,” and “My main domicile is within the US.” It presently prices simply $4.99 to acquire a .US area by way of GoDaddy.
GoDaddy mentioned it additionally conducts a scan of chosen registration request data, and conducts “spot checks” on registrant data.
“We conduct common critiques, per coverage, of registration information inside the Registry database to find out Nexus compliance with ongoing communications to registrars and registrants,” the corporate mentioned in a written assertion.
GoDaddy says it “is dedicated to supporting a safer on-line setting and proactively addressing this problem by assessing it towards our personal anti-abuse mitigation system.”
“We stand towards DNS abuse in any type and keep a number of techniques and protocols to guard all of the TLDs we function,” the assertion continued. “We are going to proceed to work with registrars, cybersecurity corporations and different stakeholders to make progress with this complicated problem.”
Interisle discovered important numbers of .US domains had been registered to assault among the United States’ most outstanding corporations, together with Financial institution of America, Amazon, Apple, AT&T, Citi, Comcast, Microsoft, Meta, and Goal.
“Mockingly, not less than 109 of the .US domains in our information had been used to assault the US authorities, particularly the US Postal Service and its clients,” Interisle wrote. “.US domains had been additionally used to assault international authorities operations: six .US domains had been used to assault Australian authorities providers, six attacked Nice’s Britain’s Royal Mail, one attacked Canada Submit, and one attacked the Denmark Tax Authority.”
The NTIA not too long ago revealed a proposal that may permit GoDaddy to redact registrant information from WHOIS registration data. The present constitution for .US specifies that each one .US registration data be public.
Interisle argues that with out extra stringent efforts to confirm a United States nexus for brand new .US area registrants, the NTIA’s proposal will make it much more troublesome to determine phishers and confirm registrants’ identities and nexus {qualifications}.
In a written assertion, the NTIA mentioned DNS abuse is a precedence problem for the company, and that NTIA helps “evidence-based policymaking.”
“We look ahead to reviewing the report and can have interaction with our contractor for the .US area on steps that we are able to take not solely to handle phishing, however the different types of DNS abuse as effectively,” the assertion reads.
Interisle sources its phishing information from a number of locations, together with the Anti-Phishing Working Group (APWG), OpenPhish, PhishTank, and Spamhaus. For extra phishing information, see Interisle’s 2023 Phishing Panorama report (PDF).’
Replace, Sept. 5, 1:44 p.m. ET: Up to date story with assertion offered immediately by the NTIA.

