A brand new data stealer malware named ‘MetaStealer’ has appeared within the wild, stealing all kinds of delicate data from Intel-based macOS computer systems.
MetaStealer, to not be confused with the ‘META’ info-stealer that noticed some recognition final 12 months, is a Go-based malware able to evading Apple’s built-in antivirus tech XProtect, concentrating on enterprise customers.
SentinelOne experiences it has been monitoring the malware for the previous couple of months, seeing an uncommon involvement of social engineering in its distribution.
Though the malware has some similarities with Atomic Stealer, one other Go-based macOS concentrating on info-stealer, the code overlap is proscribed, and the supply strategies are completely different.
Subsequently, SentinelOne concludes that MetaStealer is a separate operation.
Arrival on macOS techniques
SentinelOne discovered a malware pattern on VirusTotal with a remark stating the MetaStealer menace actors are contacting companies and impersonating the corporate’s purchasers to distribute the malware.
“I used to be focused by somebody posing as a design consumer, and did not notice something was out of the strange. The person I might been negotiating with on the job this previous week despatched me a password protected zip file containing this DMG file, which I assumed was a bit odd,” reads the VirusTotal remark.
“Towards my higher judgement I mounted the picture to my pc to see its contents. It contained an app that was disguised as a PDF, which I didn’t open and is once I realized he was a scammer.”
Connected to the phishing emails are disk picture recordsdata that, when mounted on the filesystem, comprise deceptively named executables that seem as PDF recordsdata to trick the sufferer into opening them.
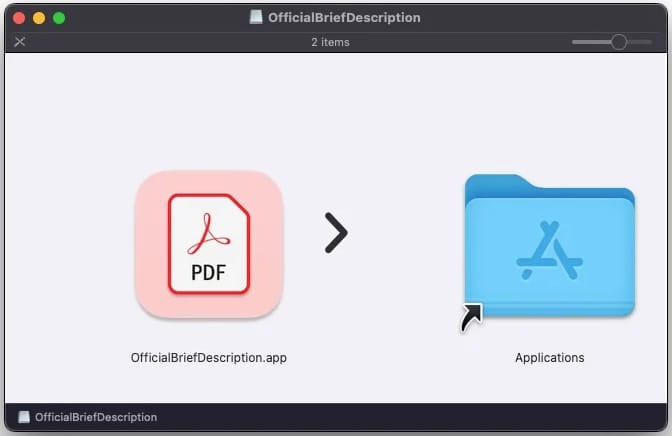
SentinelOne has noticed DMGs named after Adobe software program or consumer work, together with the next:
- Promoting phrases of reference (MacOS presentation).dmg
- CONCEPT A3 full menu with dishes and translations to English.dmg
- AnimatedPoster.dmg
- Brief_Presentation-Task_Overview-(SOW)-PlayersClub.dmg
- AdobeOfficialBriefDescription.dmg
- Adobe Photoshop 2023 (with AI) installer.dmg
The malware’s utility bundles comprise the naked necessities, specifically an Data.plist file, a Assets folder with an icon picture, and a macOS folder with the malicious Mach-O executable.
Not one of the samples examined by SentinelOne had been signed, regardless of some variations that includes an Apple Developer ID.
MetaStealer capabilities
MetaStealer makes an attempt to steal data saved on the compromised techniques, together with passwords, recordsdata, and app information, after which makes an attempt to exfiltrate them through TCP over port 3000.
Particularly, the malware options capabilities permit for exfiltrating the keychain and extracting saved passwords, stealing recordsdata from the system, and concentrating on Telegram and Meta (Fb) providers.
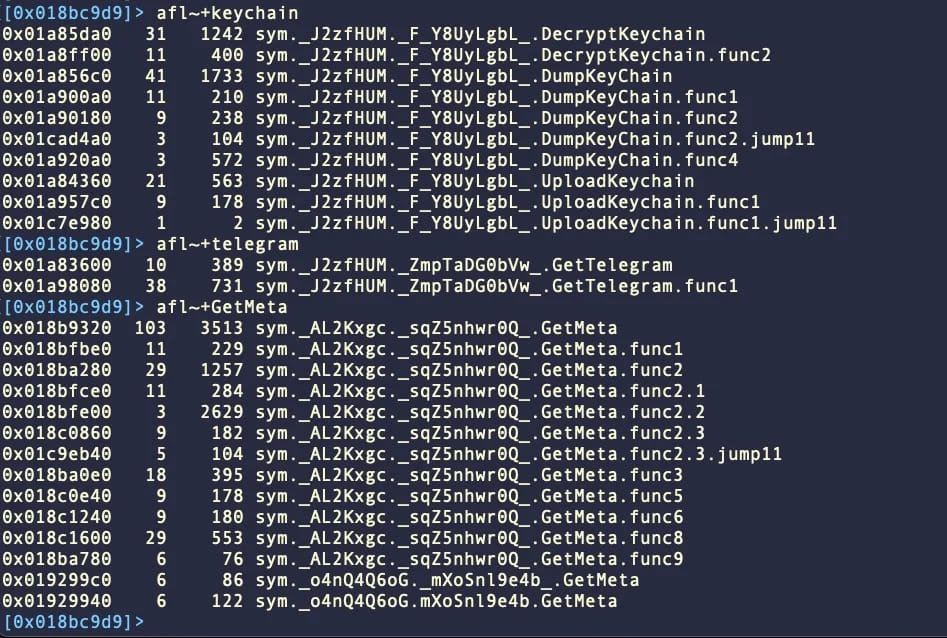
The keychain is a system-level password administration system for macOS, managing credentials for web sites, purposes, WiFi networks, certificates, encryption keys, bank card data, and even personal notes.
Therefore, the exfiltration of keychain contents is a robust function that might give the attackers entry to delicate information.
In its present model, MetaStealer solely runs on Intel x86_64 structure, which suggests it can’t compromise macOS techniques working on Apple Silicon processors (M1, M2) until the sufferer makes use of Rosetta to run the malware.
This mitigates the menace and limits it to an ever-reducing variety of potential victims as Intel-based Apple computer systems are being phased out.
Nonetheless, MetaStealer would possibly launch a brand new model that provides native assist for Apple Silicon, so it is a menace to be careful for.

